The post One Workspace, Every User – The Power of the Adaptive Secure Desktop™ appeared first on IGEL.
]]>- The Preventative Security Model
 – IGEL’s strategic framework aligning endpoint, security, and operational strategies.
– IGEL’s strategic framework aligning endpoint, security, and operational strategies. - The Preventative Security Architecture
 – The hardened design foundation that removes attack vectors by default.
– The hardened design foundation that removes attack vectors by default.
Now, in Part 3, we turn to how these ideas come alive at the edge — with the Adaptive Secure Desktop .
.
This isn’t a desktop in the traditional sense. It’s a role-based workspace delivery model — one that flexes to meet the needs of every user, while enforcing the principles of failsafe security.
It’s where strategy and execution meet the end user.
A Workspace That Adapts to Context
Modern work is dynamic. Users aren’t always in the office. Roles change. Risk levels shift. Yet most organizations still deliver the same desktop to everyone — and secure it the same way, too.
The Adaptive Secure Desktop flips that.
Instead of a one-size-fits-all OS, it delivers a context-aware workspace.
- Clinician in a hospital? Instant badge-tap access to virtual desktops with no local data.
- Retail associate at a kiosk? Locked-down browser mode tied to a single SaaS platform.
- Remote knowledge worker? Full desktop experience via DaaS, with security layered in via SASE and IAM controls.
- Contractor or M&A user? Temporary, policy-bound workspace spun up with limited permissions and app access.
The workspace changes based on who the user is, where they are, what device they’re using, and what risk profile applies — all orchestrated through IGEL OS and UMS.
Enforced by Architecture, Not Just Policy
What makes the Adaptive Secure Desktop different from traditional workspace delivery?
It’s not just a VDI session. It’s not just app publishing. It’s a security-first execution model, enforced at the OS level:
- Read-only system image: No tampering, no malware persistence.
- No local data: All access is to virtual or cloud-hosted resources.
- Hardware-rooted trust: Every boot verified, every component signed.
- USB controls and isolation: Based on role and context — not static policies.
- Dynamic access methods: Delivered based on persona — DaaS, SaaS, local apps, browsers.
And all of this is centrally managed through IGEL Universal Management Suite, giving IT full control without needing to touch the endpoint directly.
Zero Trust, Realized at the Edge
The Adaptive Secure Desktop is where IGEL’s Preventative Security Model meets Zero Trust execution.
- Every session is authenticated
- Every endpoint is validated
- Every action is governed by context
It allows customers to enforce their own Zero Trust policies — not just by integrating with IAM and SASE platforms, but by ensuring that every endpoint behaves as if it can’t be trusted until proven otherwise.
Consistency Without Complexity
From a single platform, organizations can:
- Support frontline, knowledge, and temporary users with precision.
- Deliver fast, reliable access to virtual or cloud apps — without compromising security.
- Scale globally with consistent policies, minimal overhead, and no reliance on constant patching or imaging.
It’s a future-proof foundation — built not just for what users need today, but for how work will evolve next.
The Takeaway
The Adaptive Secure Desktop is the practical delivery layer of IGEL’s Preventative Security vision. It translates strategic alignment and hardened architecture into a secure, streamlined, and personalized user experience.
This is where compliance, control, and creativity coexist. And it’s available now — through IGEL, through our ecosystem of IGEL Ready partners, and most importantly, through your own enterprise security and workspace vision.
Because transformation isn’t something you wait for. It’s something you deliver — securely, simply, and at scale.
For more information on the Preventative Security Architecture, the Preventative Security Model, and the Adaptive Secure Desktop, please submit the form below.
The post One Workspace, Every User – The Power of the Adaptive Secure Desktop™ appeared first on IGEL.
]]>The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The retail sector continues to experience an increase in cyber threats, driven by outdated infrastructure, distributed environments, and expanding attack surfaces. Recent data breaches involving well-known brands such as Harrods, Marks & Spencer, Cartier, The North Face, and Victoria’s Secret have brought this issue to light. These events underscore the dynamic and complex threat environment that retailers face today. They also emphasize that retail is a key target for well-resourced and opportunistic threat actors.
In the last two years, the retail sector has experienced a substantial increase in cybersecurity vulnerabilities and breaches, leading to serious operational and financial ramifications. In 2024, 80% of retailers reported being targets of cyberattacks, with over half admitting a growing sense of vulnerability to these threats[1]. The frequency and severity of these incidents are increasing: retail data breaches grew by 18% year-over-year in 2024, with the average breach now costing $2.96 million[2].
Ransomware continues to pose a sizable threat, with the retail industry being the second most targeted sector for ransomware attacks in 2023 and the first half of 2024. In this timeframe, the U.S. retail sector reported 256 ransomware incidents in 2024, an increase from 206 incidents reported in the first three quarters of 2023[3].
Understaffed IT teams, high turnover, and a lack of cybersecurity training, particularly for temporary and seasonal staff, have heightened vulnerabilities. The repercussions of these breaches go well beyond immediate financial impacts. Business disruptions and the damage to their reputation can be considerable and profound.
Notably, 33% of retailers have faced regulatory action due to inadequate protection of customer data[4].
What is especially concerning about these incidents is their tendency to exploit vulnerabilities that could be addressed with effective preventive security measures. This highlights the urgent need for a more comprehensive and strategic approach to cybersecurity.
Traditional cybersecurity measures aren’t keeping pace
The retail sector’s IT infrastructure is inherently vulnerable. The attack surface is wide with thousands of distributed locations, outdated systems that are challenging to update, third-party connections, and the need for constant uptime. Additionally, the rise of e-commerce has turned retail into a 24/7/365 operation, placing additional strain on IT resources and creating more potential vulnerabilities. Furthermore, risks extend beyond retail stores—logistics, inventory management, transportation, and backend systems all present possible attack access points.
Traditional security tools have not kept pace with the evolving landscape of cyber threats. Many of these solutions were originally designed for static and centralized environments, making them increasingly inadequate in the face of fast-moving threats that can easily exploit vulnerabilities across distributed and diverse endpoints such as laptops, smartphones, and cloud services, which often fall outside the direct control of traditional security measures.
Once attackers access a network, they can move laterally within the system, navigating various connected devices and systems. This lateral movement can occur alarmingly quickly, often within just a few minutes, enabling them to disable critical services and infrastructure before a retailer realizes it has been compromised.
Preventative Security as a Strategic Shift
Today’s retailers require lightweight, efficient, and functional security within limited infrastructure. More importantly, they need systems that stop breaches before they escalate.
This necessitates a strategic shift from reacting to preventing threats, and one way in which retailers can improve endpoint security is by adopting IGEL’s Preventative Security Model .
.
For retailers, IGEL OS, the Secure Endpoint OS for Now & Next:
- Immutable, read-only OS: Reduces exploitability and eliminates persistence of malware.
- Centralized configuration management: Via IGEL UMS, enabling rapid policy deployment across distributed fleets.
- Boot chain of trust: UEFI Secure Boot through to application launch, validating integrity at every step.
- PCI-DSS alignment: Designed to protect PII and cardholder data, reducing compliance burden.
- Single sign-on integration: With platforms like Okta, Entra ID, and Ping Identity to enforce identity-driven access control.
- Peripheral and protocol compatibility: Ensures business continuity without compromising usability.
- Ransomware mitigation: Architectural safeguards lower both the probability and the impact of endpoint compromise.
Rethinking Endpoint Recovery for Business Continuity
For organizations still relying on traditional endpoints, recovery from a security event often translates to logistical disruption. Device reimaging, hardware replacement, and manual reconfiguration introduce significant delays—especially in distributed retail environments with limited IT presence. When laptops are compromised or encrypted by ransomware, recovery can require full device replacement, resulting in downtime, shipping delays, and high support overhead.
IGEL OS can be used to return services utilizing the compromised endpoint hardware in place. IGEL OS runs from a read-only partition with no local data persistence. Compromised endpoints can be quickly restored using IGEL USB Boot, Dual Boot, or managed hypervisor fallback methods. This eliminates the need for physical device swaps or complex reimaging workflows.
The result is a business continuity model that is immediate, scalable, and resilient—even in environments with constrained IT support. IGEL allows organizations to return to a known-good state in minutes, not days, reducing operational disruption and breach containment costs. When combined with centralized policy enforcement via IGEL UMS, this architecture ensures security and continuity across the entire endpoint estate—without increasing complexity.
Final Thoughts
Retail security leaders are no longer measured solely by breach prevention—but by how effectively they limit operational impact when threats materialize. The endpoint remains one of the most exposed surfaces in this equation. IGEL offers an architecture that reduces the likelihood of compromise and provides rapid continuity for traditional endpoints. For CISOs, adopting a preventative, resilient endpoint strategy is not just a security imperative—it’s a business enabler.
To learn more about IGEL’s Preventative Security Model and IGEL OS: The Secure Endpoint OS for Retail, click here.
[1] https://www.vikingcloud.com/blog/retail-cybersecurity-stats-threats-and-solutions
[2] https://www.nccgroup.com/us/is-your-retail-business-prepared-for-cyber-threats-this-2024-holiday-season/
[3] https://cyberint.com/blog/other/retail-threat-landscape-2024/
The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The new research from Gartner, “Improve Business Continuity Using Desktop as a Service” is striking a similar chord with me. If the enterprise desktop place that we are living in today is so vulnerable, why don’t we just move to the place that is safer?
Stay with me..
The July 2024 CrowdStrike agent failure was a powerful example of the operational exposure most organizations still face. Gartner’s research “Improve Business Continuity Using Desktop as a Service” which references this incident, highlights the strategic role of Desktop as a Service (DaaS) and cloud-hosted virtual desktops in minimizing downtime, and also the use, of what Gartner term a “thin client operating system”. But in doing so, it also highlights a prevailing mindset: **that we are designing the endpoint for failover, rather than designing for failsafe.**
Lets quickly tackle that term – “thin client operating system”. Now I’m looking at this it deserves its own blog, but – The term “thin client” is inextricably linked to the hardware. Search on the term “thin client” and what do you see? A page full of hardware. Wikipedia even states “a simple (low-performance) computer”. Ask an AI engine what the benefits of a thin client are and you’ll find improved security, lower TCO, improved reliability and uptime. Lets take those benefits (often, but not always, delivered by or enabled by the software – IGEL) and lets run them on any device,not just “thin clients”.
At IGEL, we believe in a more targeted, fit for purpose strategy: Yes, have a plan. Yes, embrace VDI, DaaS and browser. But first, ask: what if your endpoint was designed to minimize the risk of failure in the first place?
The Recovery Assumption: The Traditional Endpoint as the Failure Point
Gartner is right to emphasize preparedness. Failures—from agent misfires to ransomware—do happen. But implicit in the recovery model is the assumption that a traditional, built for every eventuality, writeable endpoint is the default (specifically calling out resetting it). And that means layering on security agents, patching, backups, and more.
IGEL, see the endpoint differently: not as something to defend with layers, but something to simplify and harden by design.
Security by Design: The Preventative Security Model
IGEL’s Preventative Security Model shifts endpoint thinking from detection and remediation to proactive prevention and simplification.
- Immutable, Read-Only OS: Stops tampering and malware persistence.
- No Local Data: Removes exfiltration and encryption targets.
- Cryptographically Verified Boot: Ensures the system starts in a known-good state.
- Minimized Attack Surface: Only the necessary components are delivered to the device.
This is not about claiming unbreakable software. IGEL OS is software after all. But it’s software architected with the principles of Zero Trust and attack surface minimization at its core.
Workloads no longer run at the endpoint
With applications increasingly moving away from the endpoint and into the cloud, and Gartner themselves predicting that by 2030 Secure Enterprise Browsers will be a central component of application access strategies, isn’t it time to rethink the endpoint? Isn’t this a point in time to redefine the enterprise endpoint – just like the Enterprise Browser is being redefined?
Business Continuity Begins with Fewer Incidents
Gartner is right: you need a business continuity plan. Virtual desktops and cloud scaling are essential. But we believe true endpoint resilience starts before recovery:
- Design devices that are difficult to compromise
- Limit what runs locally and how it’s accessed
- Deliver workspaces adaptively, based on user role and risk
Case in Point: Dual-Layer Resilience in Action
During the July 2024 CrowdStrike incident, IGEL endpoints remained operational and unaffected. Azure Virtual Desktops could be reset in minutes, as shared by Microsoft’s Scott Manchester—showcasing the agility of modern cloud workspaces. This isn’t applicable to AVD, but all DaaS providers. This combination—IGEL at the endpoint and workloads (DaaS, Enterprise Browser) in the cloud—represents a blueprint for secure, scalable, and resilient desktop delivery.
So (and you’ve been patient) if our destination, in the event of a compromise or failure, is a more resilient infrastructure, powered by a more resilient endpoint operating system and VDI, DaaS, or enterprise browser – rather than go on holiday there, why don’t we just live there?
The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The post IGEL Insights to Deliver Unified Endpoint Telemetry & Management Data appeared first on IGEL.
]]>Gaining visibility into endpoint performance, security, and user experience has long been a challenge. Many monitoring and analytics tools require custom-built agents or complex integrations, adding operational overhead while increasing security risks. IGEL Insights eliminates these barriers, delivering real-time telemetry and data management through a new API and an integrated IGEL UMS dashboard.
This enables IT teams, security analysts, and technology partners to access critical endpoint data without the need for custom IGEL agent applications. By integrating IGEL Insights with DEX, SIEM, SOAR, Threat Management, and Cyber-Physical System Monitoring solutions, organizations can reduce downtime, enhance security, and optimize endpoint performance.
What IGEL Insights Will Deliver
IGEL Insights will provide two key access points for understanding and managing IGEL OS endpoints:
IGEL UMS Dashboard: Real-Time Performance Data for IT Administrators
- A built-in dashboard within IGEL Universal Management Suite (UMS) will provide key performance and system health metrics for IGEL administrators.
- IT teams will be able to monitor endpoint activity, identify performance issues, and optimize operations without the need for external integrations.
- Designed for day-to-day management, the UMS dashboard will present a curated set of essential data while maintaining a simple and intuitive interface.
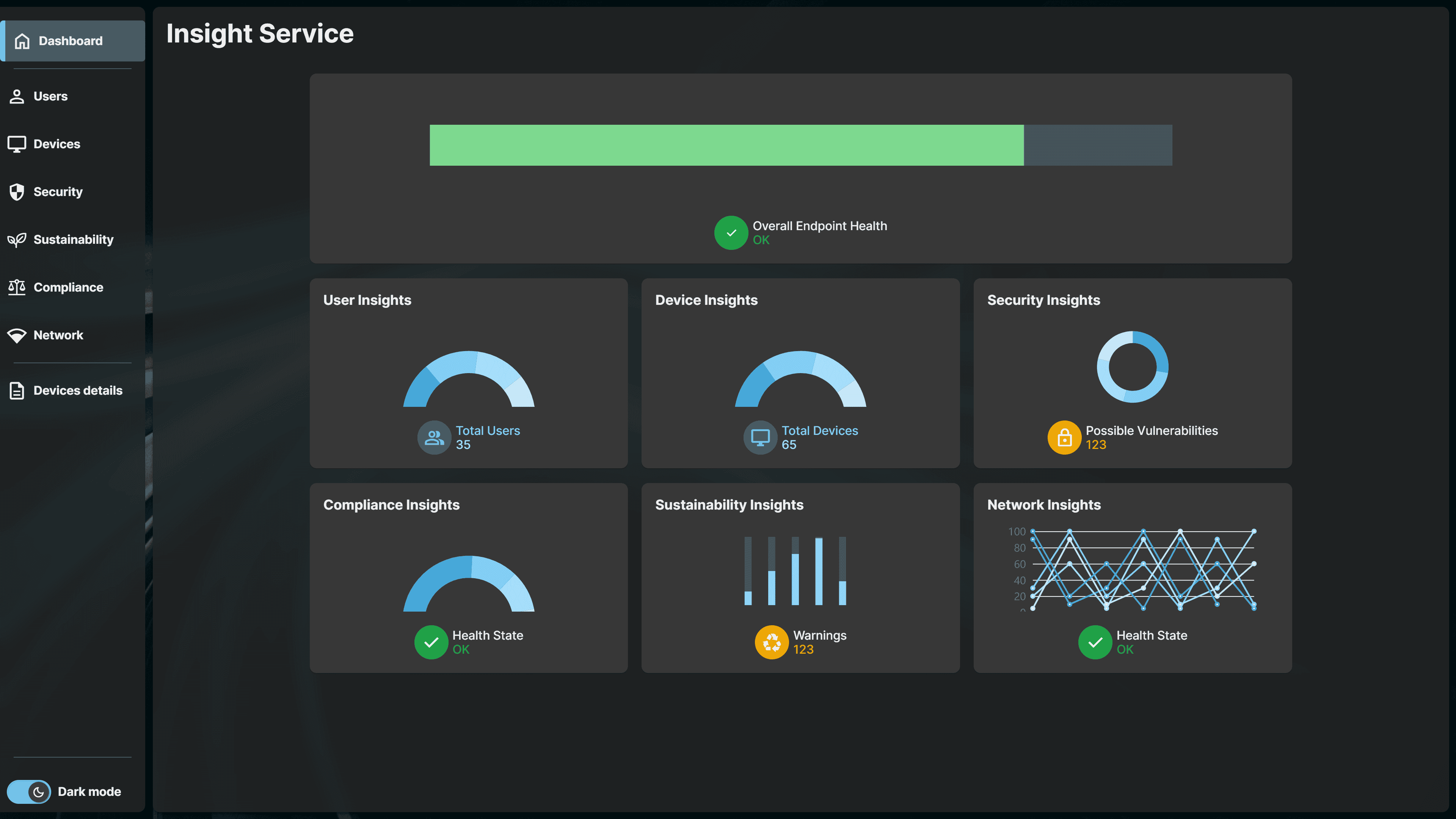 IGEL Insight Service Dashboard. Click image to view the demo video.
IGEL Insight Service Dashboard. Click image to view the demo video.
IGEL Insights API: Deep Endpoint Intelligence for Partners & Security Teams
- The IGEL Insights API will expose 100% of the captured telemetry and management data for integration with DEX, SIEM, SOAR, Threat Management, and Cyber-Physical System Monitoring solutions.
- Partners and IT teams will be able to correlate IGEL OS telemetry with other IT and security data for root cause analysis, compliance enforcement, and proactive threat detection.
- Removes the need for custom IGEL agent applications, allowing direct agentless access to data for real-time monitoring and automation.
Transforming Endpoint Monitoring and Security
By leveraging IGEL Insights, organizations will gain a new level of visibility into endpoint behavior while enhancing their existing monitoring and security platforms.
- IT administrators will benefit from integrated performance monitoring through IGEL UMS, ensuring high availability and uptime.
- Technology partners and security teams will gain deep telemetry data via API, enabling them to improve root cause analysis and incident response.
- Enterprise IT teams will be able to reduce support costs, optimize remote work environments, and improve compliance through enhanced endpoint intelligence.
With the first partner API expected at the end of Q2, IGEL is expanding how organizations access and leverage IGEL OS data to support security, compliance, and performance initiatives.
Enhancing IT & Security Through Seamless Data Integration
By making real-time telemetry and management data more accessible, IGEL Insights will empower organizations to take a proactive approach to endpoint security and performance. Whether through the integrated IGEL UMS dashboard or the comprehensive IGEL Insights API, IT teams and security partners will be able to act faster, reduce risk, and optimize user experience—without unnecessary complexity.
Want to learn more?
Stay tuned for upcoming announcements and prepare to integrate IGEL Insights into your security and IT operations strategy.
View the Demo Video
The post IGEL Insights to Deliver Unified Endpoint Telemetry & Management Data appeared first on IGEL.
]]>The post A Defense in Depth Approach to Business Continuity appeared first on IGEL.
]]>Achieving operational resilience demands robust planning and risk management amidst constant siege from cyber threats and unforeseen disruptions. IT leaders planning business continuity and security must ask themselves one critical question: How fast can we recover? Cybersecurity breaches and IT outages are no longer rare occurrences—they are the storm clouds on every CIO’s horizon. In 2024 alone, incidents ranging from ransomware attacks, to software outages, natural disasters or so-called snow days cost enterprises billions and left operational teams scrambling to regain control.
Resilience is enabled by a robust business continuity plan (BCP). While most organizations back up data and upgrade infrastructure, one crucial component often goes overlooked—the endpoint. The frontline devices that users depend on daily are the most vulnerable, and when compromised, can disrupt operations at scale.
IGEL Business Continuity solution is not just about reactive disaster recovery but about proactive resilience. By combining an emergency “911” or “999” solution, organizations can get back up and running quickly and securely, amidst a breach or outage.
Defense in Depth (DiD) is a cybersecurity strategy that uses multiple layers of security controls to protect data and systems from threats. Instead of relying on a single defense mechanism, DiD ensures that if one layer is compromised, others are still in place to mitigate risks. IGEL Business Continuity offers an in–depth approach to endpoint recovery including IGEL Business Continuity Dual Boot, IGEL Business Continuity USB boot and services.
What sets IGEL apart is not just speed but strategy. Deployment is set up in advance with an IGEL Specialist, ensuring that authentication protocols, virtual desktop clients, and collaboration tools like Teams and Zoom are integrated and ready. IT regains control and can manage recovery in minutes and hours, not days or even weeks.
Moreover, as part of the IGEL Preventative Security Model, IGEL OS operates as a read-only system with no local data storage, aligning perfectly with zero-trust security principles. No endpoint data, no persistent risk.
In hybrid work scenarios, IGEL Business Continuity extends beyond office walls. Employees stranded at home by weather or transport issues can securely access corporate resources using personal devices, booting directly into IGEL OS without risking company data leaks.
Cyber threats and IT outages will continue to rise. But with IGEL Business Continuity in your BCP toolkit, they don’t have to disrupt your operations. Don’t wait for an emergency to test your business continuity plan. Strengthen it now with IGEL Business Continuity.
View the Demo Video
Learn more, visit igel.com/business-continuity
The post A Defense in Depth Approach to Business Continuity appeared first on IGEL.
]]>The post Is Endpoint Recovery Part of Your Business Continuity Plan? appeared first on IGEL.
]]>The Endpoint: A Gateway to Vulnerability
According to IBM, as many as 90% of successful cyber-attacks originate from the endpoint. These are the devices we use every day—desktops, laptops, and other connected hardware. Despite this alarming statistic, endpoint recovery is often an afterthought in business continuity planning. Why is that?
One reason could be the assumption that if the data is secure, the business is secure. But this overlooks the reality that compromised endpoints can serve as entry points for attacks, leading to data breaches, ransomware, and other forms of cybercrime. If the endpoint is compromised, how will your organization continue to operate effectively? This question highlights the critical gap in many business continuity strategies.
IGEL Business Continuity: Bridging the Gap
At IGEL, we recognize the importance of securing and maintaining continuity for endpoints, especially in an era where ransomware and other cyber threats are increasingly sophisticated. That’s why we developed IGEL Business Continuity, a solution designed to ensure that even when Windows endpoints are compromised, your organization can continue to operate with minimal disruption.
Recover from Ransomware in Minutes
IGEL Business Continuity enables compromised Windows endpoints to be clean booted into IGEL OS in minutes, using the same hardware. By utilizing IGEL Business Continuity USB Boot, a dedicated USB drive or IGEL Business Continuity Dual Boot partition, employees can quickly reconnect to essential online services like Office 365, Teams, and Zoom. This ensures that communications can resume, and users can access recovered services as they become available. With Business Continuity Services included, organizations can minimize downtime and maintain business operations, even in the worst-case scenarios.
Watch this short demo video showing endpoint recovery in just over one minute.
Clean-Boot Compromised Windows Endpoints
When ransomware strikes, the Windows operating system is typically altered to contain malicious code. IGEL Business Continuity bypasses the compromised Windows OS by booting directly into a clean IGEL OS environment. This allows administrators to swiftly reconnect users to business-critical resources, while deciding on the best course of action—whether re-imaging, replacing, or transitioning those endpoints to IGEL OS to prevent future attacks. As part of the IGEL Preventative Security Model , this approach reduces the attack surface, eliminating vulnerabilities that bad actors often exploit. Simply IGEL it as a more secure alternative to Windows.
, this approach reduces the attack surface, eliminating vulnerabilities that bad actors often exploit. Simply IGEL it as a more secure alternative to Windows.
Work-from-Home Events: Be Prepared for the Unexpected
Business Continuity isn’t just about dealing with cyber threats. Natural disasters, transportation strikes, and other unexpected events can prevent employees from accessing their office-based IT equipment. In these situations, IGEL Business Continuity USB Boot acts as an ’emergency break glass’ option. Employees can use their personal x86 64-bit devices to boot cleanly into IGEL OS, providing secure access to company resources without compromising data security. The Preventative Security Model of IGEL OS ensures that no company data is copied to the personal device, and normal operations can resume as soon as the USB drive is removed.
of IGEL OS ensures that no company data is copied to the personal device, and normal operations can resume as soon as the USB drive is removed.
Flexible Solutions for Your Unique Needs
IGEL Business Continuity offers flexible options to fit your organization’s specific requirements:
- IGEL Dual Boot: a protected IGEL partition alongside the Windows partition. It can be installed with Windows management tools, no-touch on an endpoint. In the event the Windows OS is compromised, the IGEL Dual Boot enables the user to clean boot to secure IGEL OS, operations can quickly reinstate secure connection to communication and business services.
- IGEL USB Boot: a dedicated USB drive distributed to the user and set up with IT specialist services during onboarding. In the event the hard disk on the compromised endpoint fails, IGEL Business Continuity USB Boot enables IT to clean boot a compromised Windows endpoint to IGEL OS, retrieve the latest updates from IGEL UMS management to securely reconnect to communication and business services.
Expert Guidance with Business Continuity Services
An IGEL Business Continuity Specialist assists in setting up the required IGEL infrastructure and configuration of the endpoint image. Regularly, this image can either be updated on the IGEL Business Continuity USB Boot or, through remote management of the endpoints, on the IGEL Dual Boot partition. Different endpoint requirements depending on user location, business unit, or use case, —such as authentication, virtual desktop clients, and collaboration tools—may arise and need to be installed on each USB device/boot image. The specialist collaborates with the customer’s IT teams to prepare test and refine the images and participate in scheduled recovery exercises throughout the year. This proactive setup ensures the organization’s business continuity plan is in place, allowing IT teams to focus on incident response when needed.
Conclusion: Don’t Leave Your Endpoints Unprotected
While it’s encouraging to see organizations take data protection seriously, it’s equally important to recognize the critical role endpoints play in your overall security and continuity strategy. As cyber threats evolve, ensuring endpoint recovery is no longer optional—it’s essential. IGEL Business Continuity provides a reliable, secure solution that helps you stay connected and operational, even when faced with the unexpected. If you’re looking for a secure alternative to Windows that minimizes risk and maximizes uptime, Simply IGEL it.
Don’t wait until it’s too late. Integrate endpoint recovery into your Business Continuity Plan today with IGEL.
The post Is Endpoint Recovery Part of Your Business Continuity Plan? appeared first on IGEL.
]]>