The post One Workspace, Every User – The Power of the Adaptive Secure Desktop™ appeared first on IGEL.
]]>- The Preventative Security Model
 – IGEL’s strategic framework aligning endpoint, security, and operational strategies.
– IGEL’s strategic framework aligning endpoint, security, and operational strategies. - The Preventative Security Architecture
 – The hardened design foundation that removes attack vectors by default.
– The hardened design foundation that removes attack vectors by default.
Now, in Part 3, we turn to how these ideas come alive at the edge — with the Adaptive Secure Desktop .
.
This isn’t a desktop in the traditional sense. It’s a role-based workspace delivery model — one that flexes to meet the needs of every user, while enforcing the principles of failsafe security.
It’s where strategy and execution meet the end user.
A Workspace That Adapts to Context
Modern work is dynamic. Users aren’t always in the office. Roles change. Risk levels shift. Yet most organizations still deliver the same desktop to everyone — and secure it the same way, too.
The Adaptive Secure Desktop flips that.
Instead of a one-size-fits-all OS, it delivers a context-aware workspace.
- Clinician in a hospital? Instant badge-tap access to virtual desktops with no local data.
- Retail associate at a kiosk? Locked-down browser mode tied to a single SaaS platform.
- Remote knowledge worker? Full desktop experience via DaaS, with security layered in via SASE and IAM controls.
- Contractor or M&A user? Temporary, policy-bound workspace spun up with limited permissions and app access.
The workspace changes based on who the user is, where they are, what device they’re using, and what risk profile applies — all orchestrated through IGEL OS and UMS.
Enforced by Architecture, Not Just Policy
What makes the Adaptive Secure Desktop different from traditional workspace delivery?
It’s not just a VDI session. It’s not just app publishing. It’s a security-first execution model, enforced at the OS level:
- Read-only system image: No tampering, no malware persistence.
- No local data: All access is to virtual or cloud-hosted resources.
- Hardware-rooted trust: Every boot verified, every component signed.
- USB controls and isolation: Based on role and context — not static policies.
- Dynamic access methods: Delivered based on persona — DaaS, SaaS, local apps, browsers.
And all of this is centrally managed through IGEL Universal Management Suite, giving IT full control without needing to touch the endpoint directly.
Zero Trust, Realized at the Edge
The Adaptive Secure Desktop is where IGEL’s Preventative Security Model meets Zero Trust execution.
- Every session is authenticated
- Every endpoint is validated
- Every action is governed by context
It allows customers to enforce their own Zero Trust policies — not just by integrating with IAM and SASE platforms, but by ensuring that every endpoint behaves as if it can’t be trusted until proven otherwise.
Consistency Without Complexity
From a single platform, organizations can:
- Support frontline, knowledge, and temporary users with precision.
- Deliver fast, reliable access to virtual or cloud apps — without compromising security.
- Scale globally with consistent policies, minimal overhead, and no reliance on constant patching or imaging.
It’s a future-proof foundation — built not just for what users need today, but for how work will evolve next.
The Takeaway
The Adaptive Secure Desktop is the practical delivery layer of IGEL’s Preventative Security vision. It translates strategic alignment and hardened architecture into a secure, streamlined, and personalized user experience.
This is where compliance, control, and creativity coexist. And it’s available now — through IGEL, through our ecosystem of IGEL Ready partners, and most importantly, through your own enterprise security and workspace vision.
Because transformation isn’t something you wait for. It’s something you deliver — securely, simply, and at scale.
For more information on the Preventative Security Architecture, the Preventative Security Model, and the Adaptive Secure Desktop, please submit the form below.
The post One Workspace, Every User – The Power of the Adaptive Secure Desktop™ appeared first on IGEL.
]]>The post From Reactive to Resilient – Inside the Preventative Security Architecture™ appeared first on IGEL.
]]> (PSM) — IGEL’s strategic framework for aligning endpoint, security, and application strategies across the modern enterprise. But strategy without execution is just ambition.
(PSM) — IGEL’s strategic framework for aligning endpoint, security, and application strategies across the modern enterprise. But strategy without execution is just ambition.
That’s where IGEL’s Preventative Security Architecture comes in.
Beyond “Monitor, Detect, Remediate”
Traditional endpoints were designed for general-purpose use—built to accommodate consumers, gamers, and enterprises alike—not to meet the specific demands of secure enterprise environments. Today’s standard endpoint stack is designed to detect, monitor, and remediate threats — assuming that compromise is inevitable.
IGEL turns that assumption on its head.
The Preventative Security Architecture takes a fundamentally different approach — one that prioritizes designing out risk through immutability, minimalism, and policy enforcement at every layer of the endpoint experience.
This isn’t just a better way to secure IGEL OS. It’s a blueprint for customers to establish their own preventative security architecture — one that aligns with their Zero Trust journey, compliance goals, and operational realities.
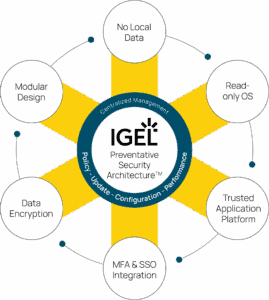
The Core Principles of Preventative Security Architecture
The architecture rests on five pillars:
- Immutable OS State: IGEL OS is locked down at the system level. Unauthorized changes simply can’t persist — or even run.
- Zero Local Data: No data lives on the endpoint. IGEL endpoints are stateless — there’s nothing to exfiltrate or encrypt.
- Secure Boot and Trusted Application Platform: Boot-time chain-of-trust backed by UEFI and TPM ensures only validated components load.
- Minimal Attack Surface: A 2GB core footprint, with optional modules added only as needed — reducing vulnerability density.
- Centralized, Granular Policy Control via UMS: Over 9,000 configurable settings. Enforce consistency without needing endpoint agents.
This is what “secure by design” looks like in practice — not theoretical protections, but tangible barriers that eliminate the opportunity for exploitation.
Your Preventative Security Architecture
This isn’t about locking customers into IGEL’s view of security. It’s about giving them a foundation to build their own preventative strategy — a Preventative Security Architecture that scales with their policies, their risks, and their compliance mandates.
Whether it’s:
- Rolling out a Zero Trust initiative,
- Aligning SOC frameworks such as NIST CSF or ISO 27001,
- Responding to rising ransomware threats
- Transitioning from Windows to a hybrid DaaS model,
IGEL’s architecture supports that journey. Not by dictating it — but by enabling it.
IGEL Ready – The Ecosystem That Powers It
Every strong architecture needs strong integrations. These are provided by the IGEL Ready program.
Through our expansive partner ecosystem, organizations can integrate leading Zero Trust, SSE/SASE, IAM, UEM and compliance solutions into the IGEL experience — natively. Partners like:
- Zscaler, Palo Alto, Netskope (for secure access)
- Microsoft Entra ID, Workspace ONE Access, Imprivata and Okta (for identity and conditional access)
- Island and Microsoft Edge (for browser-based workspaces)
- HP, LG, Lenovo (for secure and sustainable hardware endpoints)
These aren’t bolt-ons. They’re validated. Secure. Orchestrated. And ready to scale.
The Payoff – Simpler, Safer, Resilient
By adopting a preventative security architecture, enterprises can:
- Reduce risk – by removing attack vectors before they can be exploited.
- Reduce cost – by eliminating layers of endpoint agents and streamlining patch cycles.
- Reduce noise – by minimizing alerts and avoiding alert fatigue.
- Improve compliance – through posture-based access and centralized controls.
This is the architecture for the next generation of secure work — and it’s not just IGEL’s. It’s yours.
In Part 3, we’ll tie it all together with the Adaptive Secure Desktop — a dynamic, context-aware workspace delivery model that puts this architecture into motion for every user, device, and role.
— a dynamic, context-aware workspace delivery model that puts this architecture into motion for every user, device, and role.
The post From Reactive to Resilient – Inside the Preventative Security Architecture™ appeared first on IGEL.
]]>The post Rethinking Endpoint Strategy with IGEL appeared first on IGEL.
]]>
This needs to be the era of designing for failsafe.
Instead of relying on detection and remediation, the endpoint must be built to resist compromise — integrated, intelligent, and inherently resilient. IGEL’s Preventative Security Model is the strategic foundation for that shift.
is the strategic foundation for that shift.
This blog series unpacks the full scope of IGEL’s security and workspace transformation strategy in three parts:
- Preventative Security Model
 – IGEL’s unifying framework that aligns application access, security, and hardware strategy.
– IGEL’s unifying framework that aligns application access, security, and hardware strategy. - Preventative Security Architecture
 – The enforcement layer that operationalizes failsafe and becomes your organizations Preventative Security Architecture.
– The enforcement layer that operationalizes failsafe and becomes your organizations Preventative Security Architecture. - Adaptive Secure Desktop
 – A curated on-demand workspace that meets every user, role, and risk profile.
– A curated on-demand workspace that meets every user, role, and risk profile.
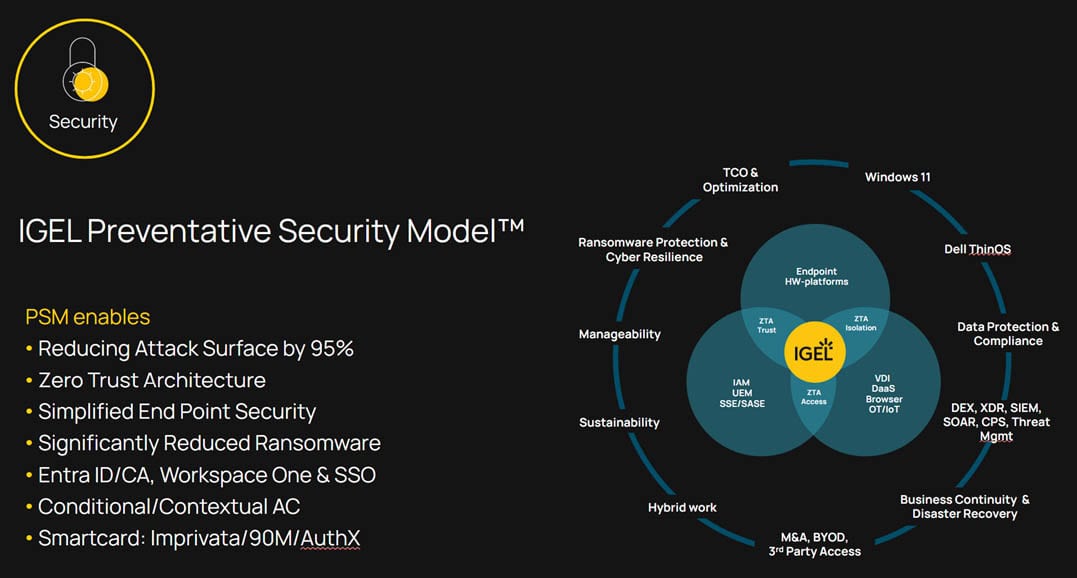
The Preventative Security Model
The Preventative Security Model (PSM) is IGEL’s approach to unifying modern endpoint strategies. It’s not an agent. It’s not a policy engine. It’s a philosophy — one that repositions the endpoint from a reactive risk surface to a strategic control layer.
And it’s built for a world that looks very different than it did five years ago.
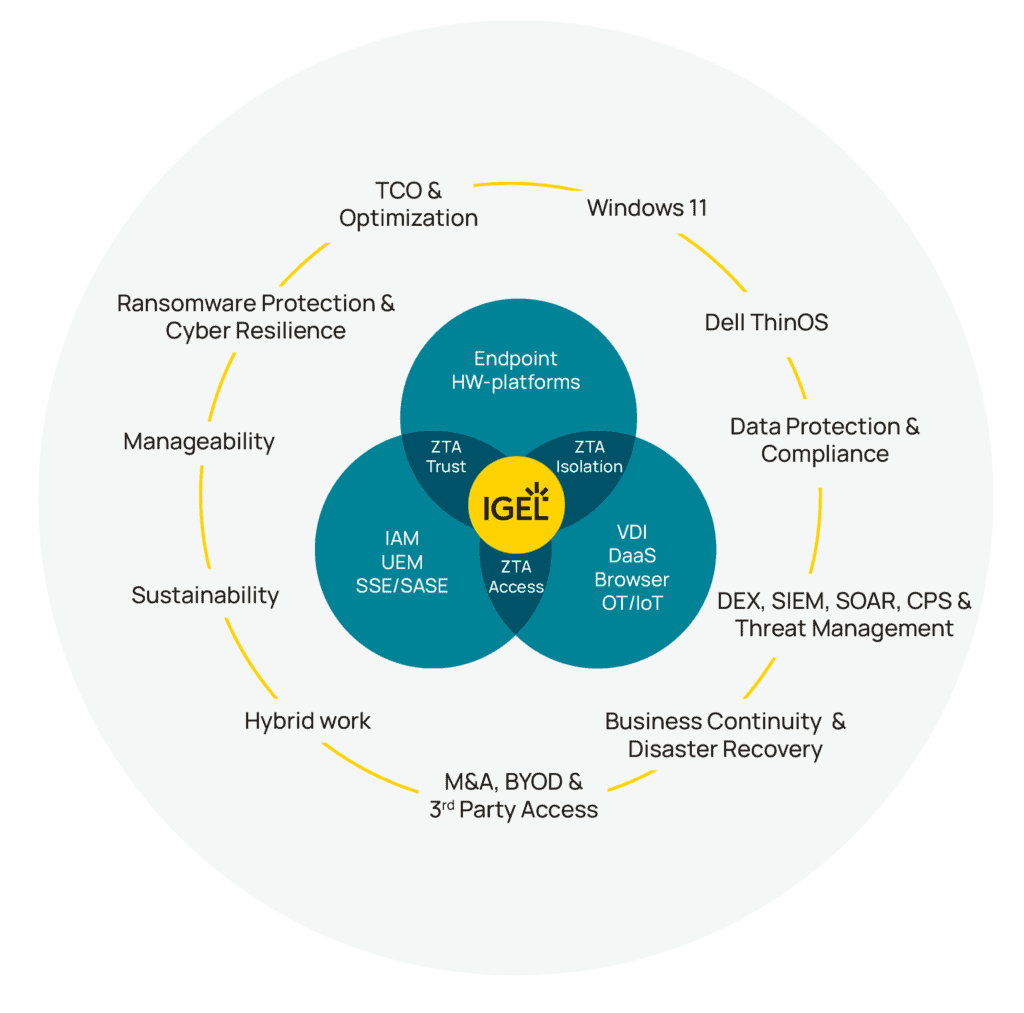
The Endpoint Has Shifted — So Must Our Strategy
Enterprise computing has moved. Workloads have left the endpoint. SaaS, DaaS, and enterprise browsers now carry the weight of productivity. Users roam. Devices are fluid. Data must stay protected — without relying on where it physically lives.
IGEL is the constant in that transition. Both now and next.
The Preventative Security Model provides the framework that connects:
- Application access: Whether delivering full desktops, browser-based tools, native Linux apps, Progressive Web Apps, hybrid SaaS, or even Windows workloads, PSM enables five flexible delivery models — each tailored to user’s needs and risk posture.
- Zero Trust strategy: Zero Trust is a security model that assumes no user or device is inherently trusted and requires continuous verification of identity, context, and access for every interaction within a network. Zero Trust isn’t a product. You don’t buy Zero Trust from a single company. PSM integrates deeply with leading IAM, UEM, SASE, and SaaS vendors to enforce Zero Trust principles from the device outward for secure information access.
- Endpoint sustainability: With endpoints no longer requiring three-to-five-year hardware refreshes due to the simplified workloads, PSM supports long-term device reuse — particularly relevant as organizations scramble to meet Windows 10 EOL activities and deadlines, the EU’s Corporate Sustainability Reporting Directive(CSRD), and Environmental, Social and Governance targets (ESG)
- Operational flexibility: From remote onboarding to rapid reconfiguration during M&A, PSM provides the consistency needed to adapt at speed.
IGEL Ready – The Force Multiplier for the Preventative Security Model
PSM is powered by the IGEL Ready ecosystem — a diverse and growing network of partners across security, identity, peripherals, communications, and hardware. These aren’t just integrations. They’re certified relationships that extend IGEL’s strategy into enterprise environments at scale.
Through IGEL Ready, PSM supports:
- HP, LG, Lenovo, and other leading OEMs to ensure secure, performant hardware compatibility.
- Identity platforms like Microsoft’s EntraID, Omnissa Workspace ONE Access, Imprivata, Okta and Ping for integrated SSO and MFA.
- Security vendors including Zscaler, Palo Alto Networks, and Netskope for Zero Trust and SSE enforcement.
- Peripheral support for clinical, financial, manufacturing, government and retail workflows — including smartcards, speech mics, OT equipment, barcode scanners, document scanners and signature pads to name only a few.
Together, this ecosystem ensures that IGEL endpoints can sit at the centre of a modern, multi-vendor Zero Trust strategy — without friction, without fragility.
Strategic Outcomes Delivered
The Preventative Security Model is not just about securing endpoints. It’s about enabling enterprise transformation. Across industries, PSM is already delivering impact:
- Business Continuity: Fast recovery of compromised traditional endpoints utilizing the in-place hardware
- M&A acceleration: Standardize and secure diverse endpoint fleets across acquired orgs without rip-and-replace.
- Windows 11 readiness: Shift Windows to the cloud, maintain existing hardware, and simplify support.
- Sustainability, CSRD and ESG: Extend endpoint lifespan, reduce e-waste, and align IT with carbon reduction targets.
- Zero Trust execution: Connect policy enforcement from identity to device, in real time, at scale.
Where traditional endpoint stacks are reactive and bloated, PSM is lightweight, adaptive, and policy-aligned — a failsafe foundation for the cloud-first enterprise.
Next up: Preventative Security Architecture, where we explore how IGEL OS eliminates attack vectors and enforces failsafe security by design.
The post Rethinking Endpoint Strategy with IGEL appeared first on IGEL.
]]>The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The retail sector continues to experience an increase in cyber threats, driven by outdated infrastructure, distributed environments, and expanding attack surfaces. Recent data breaches involving well-known brands such as Harrods, Marks & Spencer, Cartier, The North Face, and Victoria’s Secret have brought this issue to light. These events underscore the dynamic and complex threat environment that retailers face today. They also emphasize that retail is a key target for well-resourced and opportunistic threat actors.
In the last two years, the retail sector has experienced a substantial increase in cybersecurity vulnerabilities and breaches, leading to serious operational and financial ramifications. In 2024, 80% of retailers reported being targets of cyberattacks, with over half admitting a growing sense of vulnerability to these threats[1]. The frequency and severity of these incidents are increasing: retail data breaches grew by 18% year-over-year in 2024, with the average breach now costing $2.96 million[2].
Ransomware continues to pose a sizable threat, with the retail industry being the second most targeted sector for ransomware attacks in 2023 and the first half of 2024. In this timeframe, the U.S. retail sector reported 256 ransomware incidents in 2024, an increase from 206 incidents reported in the first three quarters of 2023[3].
Understaffed IT teams, high turnover, and a lack of cybersecurity training, particularly for temporary and seasonal staff, have heightened vulnerabilities. The repercussions of these breaches go well beyond immediate financial impacts. Business disruptions and the damage to their reputation can be considerable and profound.
Notably, 33% of retailers have faced regulatory action due to inadequate protection of customer data[4].
What is especially concerning about these incidents is their tendency to exploit vulnerabilities that could be addressed with effective preventive security measures. This highlights the urgent need for a more comprehensive and strategic approach to cybersecurity.
Traditional cybersecurity measures aren’t keeping pace
The retail sector’s IT infrastructure is inherently vulnerable. The attack surface is wide with thousands of distributed locations, outdated systems that are challenging to update, third-party connections, and the need for constant uptime. Additionally, the rise of e-commerce has turned retail into a 24/7/365 operation, placing additional strain on IT resources and creating more potential vulnerabilities. Furthermore, risks extend beyond retail stores—logistics, inventory management, transportation, and backend systems all present possible attack access points.
Traditional security tools have not kept pace with the evolving landscape of cyber threats. Many of these solutions were originally designed for static and centralized environments, making them increasingly inadequate in the face of fast-moving threats that can easily exploit vulnerabilities across distributed and diverse endpoints such as laptops, smartphones, and cloud services, which often fall outside the direct control of traditional security measures.
Once attackers access a network, they can move laterally within the system, navigating various connected devices and systems. This lateral movement can occur alarmingly quickly, often within just a few minutes, enabling them to disable critical services and infrastructure before a retailer realizes it has been compromised.
Preventative Security as a Strategic Shift
Today’s retailers require lightweight, efficient, and functional security within limited infrastructure. More importantly, they need systems that stop breaches before they escalate.
This necessitates a strategic shift from reacting to preventing threats, and one way in which retailers can improve endpoint security is by adopting IGEL’s Preventative Security Model .
.
For retailers, IGEL OS, the Secure Endpoint OS for Now & Next:
- Immutable, read-only OS: Reduces exploitability and eliminates persistence of malware.
- Centralized configuration management: Via IGEL UMS, enabling rapid policy deployment across distributed fleets.
- Boot chain of trust: UEFI Secure Boot through to application launch, validating integrity at every step.
- PCI-DSS alignment: Designed to protect PII and cardholder data, reducing compliance burden.
- Single sign-on integration: With platforms like Okta, Entra ID, and Ping Identity to enforce identity-driven access control.
- Peripheral and protocol compatibility: Ensures business continuity without compromising usability.
- Ransomware mitigation: Architectural safeguards lower both the probability and the impact of endpoint compromise.
Rethinking Endpoint Recovery for Business Continuity
For organizations still relying on traditional endpoints, recovery from a security event often translates to logistical disruption. Device reimaging, hardware replacement, and manual reconfiguration introduce significant delays—especially in distributed retail environments with limited IT presence. When laptops are compromised or encrypted by ransomware, recovery can require full device replacement, resulting in downtime, shipping delays, and high support overhead.
IGEL OS can be used to return services utilizing the compromised endpoint hardware in place. IGEL OS runs from a read-only partition with no local data persistence. Compromised endpoints can be quickly restored using IGEL USB Boot, Dual Boot, or managed hypervisor fallback methods. This eliminates the need for physical device swaps or complex reimaging workflows.
The result is a business continuity model that is immediate, scalable, and resilient—even in environments with constrained IT support. IGEL allows organizations to return to a known-good state in minutes, not days, reducing operational disruption and breach containment costs. When combined with centralized policy enforcement via IGEL UMS, this architecture ensures security and continuity across the entire endpoint estate—without increasing complexity.
Final Thoughts
Retail security leaders are no longer measured solely by breach prevention—but by how effectively they limit operational impact when threats materialize. The endpoint remains one of the most exposed surfaces in this equation. IGEL offers an architecture that reduces the likelihood of compromise and provides rapid continuity for traditional endpoints. For CISOs, adopting a preventative, resilient endpoint strategy is not just a security imperative—it’s a business enabler.
To learn more about IGEL’s Preventative Security Model and IGEL OS: The Secure Endpoint OS for Retail, click here.
[1] https://www.vikingcloud.com/blog/retail-cybersecurity-stats-threats-and-solutions
[2] https://www.nccgroup.com/us/is-your-retail-business-prepared-for-cyber-threats-this-2024-holiday-season/
[3] https://cyberint.com/blog/other/retail-threat-landscape-2024/
The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The post Compliance Without Compromise; Trusted No-Click Access for Securing Healthcare Workspaces appeared first on IGEL.
]]>We all know how crucial it is for clinical staff to access applications quickly and securely. Many healthcare organizations today are focused on centralizing their endpoint infrastructure through the adoption of Desktop-as-a-Service (DaaS), Software-as-a-Service (SaaS), virtual desktop infrastructure (VDI), and enterprise browser-based applications.
These organizations want easy access to essential applications without compromising security, productivity, or patient care quality. And they need more flexible and adaptable workflows as they transition applications like electronic health records (EHRs) to the cloud.
Effortless, secure, and convenient
Enter IGEL, Imprivata and Omnissa – partners in innovation, providing a robust solution designed specifically for healthcare environments.
By integrating IGEL OS with Imprivata through the IGEL Agent for Imprivata, healthcare organizations can utilize No Click AccessTM to their Omnissa Horizon® desktops or apps. This streamlined authentication process leverages proximity card technology, allowing clinicians to access their virtual desktops and applications with a simple badge tap.
This integration not only helps to shorten login times but also bolsters compliance with important security regulations, like HIPAA and GDPR. As a result, healthcare professionals can spend more time focusing on patient care, which directly enhances service delivery and leads to better patient outcomes.
Moreover, the collaboration between IGEL, Imprivata, and Omnissa offers additional valuable benefits. By combining the Omnissa Horizon platform with IGEL OS, healthcare organizations can enhance workflow efficiency and security. This powerful combination facilitates rapid, secure access to patient data and clinical applications from any device, enabling seamless roaming clinical workflows essential in both inpatient and ambulatory services settings.
Safeguard data, improve efficiency, reduce complexity, and costs
Traditional methods of detection, assessment, and remediation are not effective. Instead, healthcare organizations must prioritize preventive security measures.
IGEL’s Preventive Security Model minimizes the risk of data breaches and supports Zero Trust initiatives by ensuring sensitive information is not stored on the endpoint. This isolation and centralized user profile management through Omnissa Horizon greatly enhances organizations’ security posture, which is crucial given today’s serious data breach concerns.
minimizes the risk of data breaches and supports Zero Trust initiatives by ensuring sensitive information is not stored on the endpoint. This isolation and centralized user profile management through Omnissa Horizon greatly enhances organizations’ security posture, which is crucial given today’s serious data breach concerns.
Furthermore, the lightweight and efficient nature of IGEL’s secure OS platform allows healthcare providers to utilize laptops, thin clients, and even zero clients without the burdensome overhead of traditional hardware.
This approach:
- Reduces the cost of clinical workstations by 50-75% while bolstering security. IGEL OS operates in a read-only format with a small footprint, minimizing the risks associated with endpoint management and reducing the need for multiple security agents.
- Removes complexities associated with endpoint management. With the IGEL Universal Management Suite (UMS), managing these endpoints becomes a breeze, providing healthcare IT teams with the tools they need to oversee a large network of devices.
What’s next?
In today’s digital world, healthcare organizations have a wonderful opportunity to adopt solutions that not only fulfill their operational needs but also enrich the experiences for both patients and providers.
IGEL OS is built for SaaS, DaaS, VDI and enterprise browsers. By partnering with IGEL, Imprivata, and Omnissa, your organization can simplify workflows, strengthen data security, and enhance the user experience for your clinical staff.
Are you looking to transform your healthcare organization’s approach to digital workspace access? Discover how IGEL and our ecosystem partners can help your team deliver outstanding patient care with efficiency and confidence.
Register today for our upcoming webinar with Imprivata and Omnissa. Your clinicians deserve quick and easy access to the resources they need—let us partner with you to make that a reality!
The post Compliance Without Compromise; Trusted No-Click Access for Securing Healthcare Workspaces appeared first on IGEL.
]]>The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The new research from Gartner, “Improve Business Continuity Using Desktop as a Service” is striking a similar chord with me. If the enterprise desktop place that we are living in today is so vulnerable, why don’t we just move to the place that is safer?
Stay with me..
The July 2024 CrowdStrike agent failure was a powerful example of the operational exposure most organizations still face. Gartner’s research “Improve Business Continuity Using Desktop as a Service” which references this incident, highlights the strategic role of Desktop as a Service (DaaS) and cloud-hosted virtual desktops in minimizing downtime, and also the use, of what Gartner term a “thin client operating system”. But in doing so, it also highlights a prevailing mindset: **that we are designing the endpoint for failover, rather than designing for failsafe.**
Lets quickly tackle that term – “thin client operating system”. Now I’m looking at this it deserves its own blog, but – The term “thin client” is inextricably linked to the hardware. Search on the term “thin client” and what do you see? A page full of hardware. Wikipedia even states “a simple (low-performance) computer”. Ask an AI engine what the benefits of a thin client are and you’ll find improved security, lower TCO, improved reliability and uptime. Lets take those benefits (often, but not always, delivered by or enabled by the software – IGEL) and lets run them on any device,not just “thin clients”.
At IGEL, we believe in a more targeted, fit for purpose strategy: Yes, have a plan. Yes, embrace VDI, DaaS and browser. But first, ask: what if your endpoint was designed to minimize the risk of failure in the first place?
The Recovery Assumption: The Traditional Endpoint as the Failure Point
Gartner is right to emphasize preparedness. Failures—from agent misfires to ransomware—do happen. But implicit in the recovery model is the assumption that a traditional, built for every eventuality, writeable endpoint is the default (specifically calling out resetting it). And that means layering on security agents, patching, backups, and more.
IGEL, see the endpoint differently: not as something to defend with layers, but something to simplify and harden by design.
Security by Design: The Preventative Security Model
IGEL’s Preventative Security Model shifts endpoint thinking from detection and remediation to proactive prevention and simplification.
- Immutable, Read-Only OS: Stops tampering and malware persistence.
- No Local Data: Removes exfiltration and encryption targets.
- Cryptographically Verified Boot: Ensures the system starts in a known-good state.
- Minimized Attack Surface: Only the necessary components are delivered to the device.
This is not about claiming unbreakable software. IGEL OS is software after all. But it’s software architected with the principles of Zero Trust and attack surface minimization at its core.
Workloads no longer run at the endpoint
With applications increasingly moving away from the endpoint and into the cloud, and Gartner themselves predicting that by 2030 Secure Enterprise Browsers will be a central component of application access strategies, isn’t it time to rethink the endpoint? Isn’t this a point in time to redefine the enterprise endpoint – just like the Enterprise Browser is being redefined?
Business Continuity Begins with Fewer Incidents
Gartner is right: you need a business continuity plan. Virtual desktops and cloud scaling are essential. But we believe true endpoint resilience starts before recovery:
- Design devices that are difficult to compromise
- Limit what runs locally and how it’s accessed
- Deliver workspaces adaptively, based on user role and risk
Case in Point: Dual-Layer Resilience in Action
During the July 2024 CrowdStrike incident, IGEL endpoints remained operational and unaffected. Azure Virtual Desktops could be reset in minutes, as shared by Microsoft’s Scott Manchester—showcasing the agility of modern cloud workspaces. This isn’t applicable to AVD, but all DaaS providers. This combination—IGEL at the endpoint and workloads (DaaS, Enterprise Browser) in the cloud—represents a blueprint for secure, scalable, and resilient desktop delivery.
So (and you’ve been patient) if our destination, in the event of a compromise or failure, is a more resilient infrastructure, powered by a more resilient endpoint operating system and VDI, DaaS, or enterprise browser – rather than go on holiday there, why don’t we just live there?
The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The post How to deploy a VM with IGEL Managed Hypervisor in four simple steps appeared first on IGEL.
]]>If you are interested as to why we are releasing a Hypervisor, I recommend you read this Blog post: https://www.igel.com/blog/igel-managed-hypervisor-secure-your-legacy-workloads/
Let’s get started!
What you will need
- IGEL Universal Management Server (UMS) v 12.07.100 or later
- IGEL OS12.6.1 or later
- IGEL Managed Hypervisor App (releasing in Q2 2025)
- WebDAV server to store and deploy the disk images (I used IIS on my UMS server for this in a LAB environment)
The process is very simple; create a VM on an OS12.6.1 or later endpoint, capture the disk image, create a profile in UMS to deploy the disk image to a target OS12.6.1 or later endpoint, then you can remotely manage OS12 and the VM from UMS.
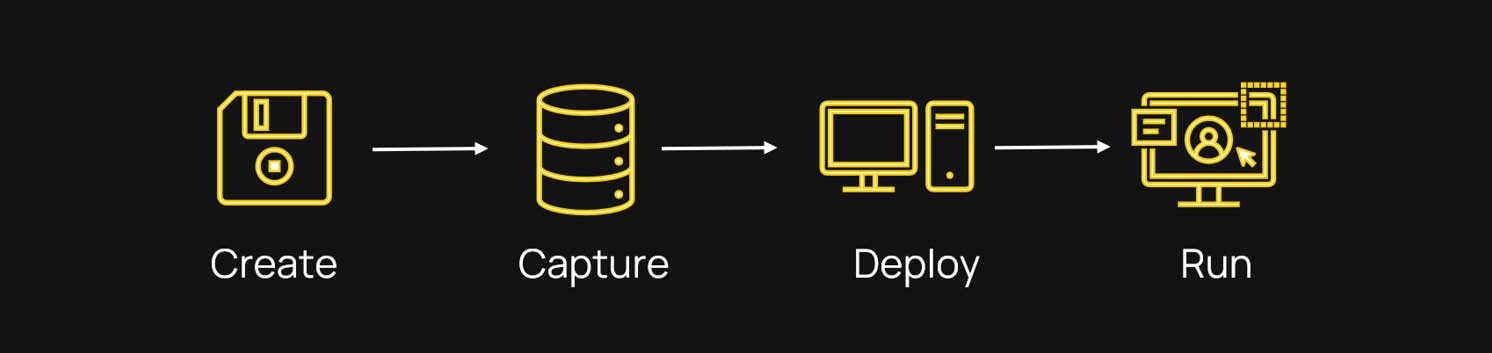
Create
The first step is to create your own ‘Golden Image’. Open the Virtual Machine Manager, click File, New Virtual Machine.
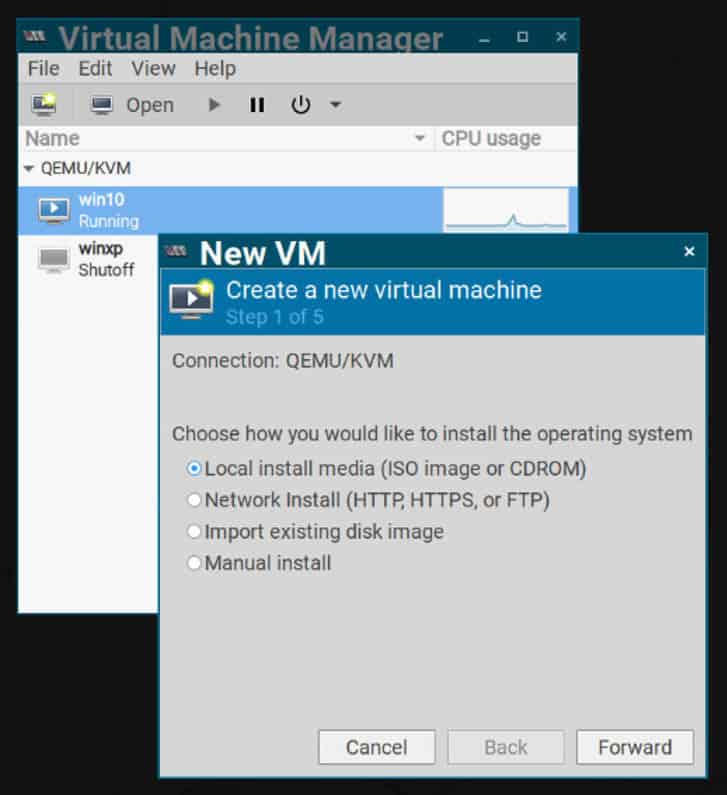
This starts with a wizard which will take you through the steps to create the virtual machine. From selecting the operating system, the storage, CPU and memory to the attached peripherals. In my case I used
a USB storage device with Windows10 and Windows XP ISO files.
Install your selected OS and configure as required.
Capture
Now you have your ‘Golden Image’ we can capture the image and get it ready for deployment. Part of the IGEL Managed Hypervisor app is an export utility called IMH Exporter. To export the VM image to the WebDAV server simply open the IMH Exporter, enter the URL to the WebDAV server and select the VM name you want to export.
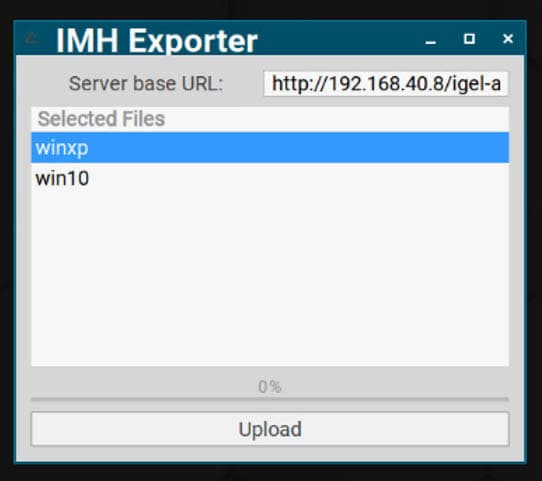
The IMH Exporter will then create two files on the WebDAV server: %vm_name%.img and %vm_name%.xml. The .img file is the disk image (this will be a large file, you will need to consider the storage size and network when exporting) the .xml file is a configuration file detailing all the component the VM needs, such as network, memory, CPU etc.
Deploy
Now we have the Image and the config file we can create a UMS Profile to deploy the Image to a target device (Tip: make sure you don’t send the VM to the device you used to create it on as you will get inconsistent results, if you need to use the same device remove the golden image first)
There are two sections in the IMH App Profile, IGEL Hypervisor Domains and IGEL Hypervisor viewer sessions.
IGEL Hypervisor Domains is used for image deployment. (a domain in this case is the name of the VM). Fill out the details for your VM and the URL to the XML file on the WebDAV server.
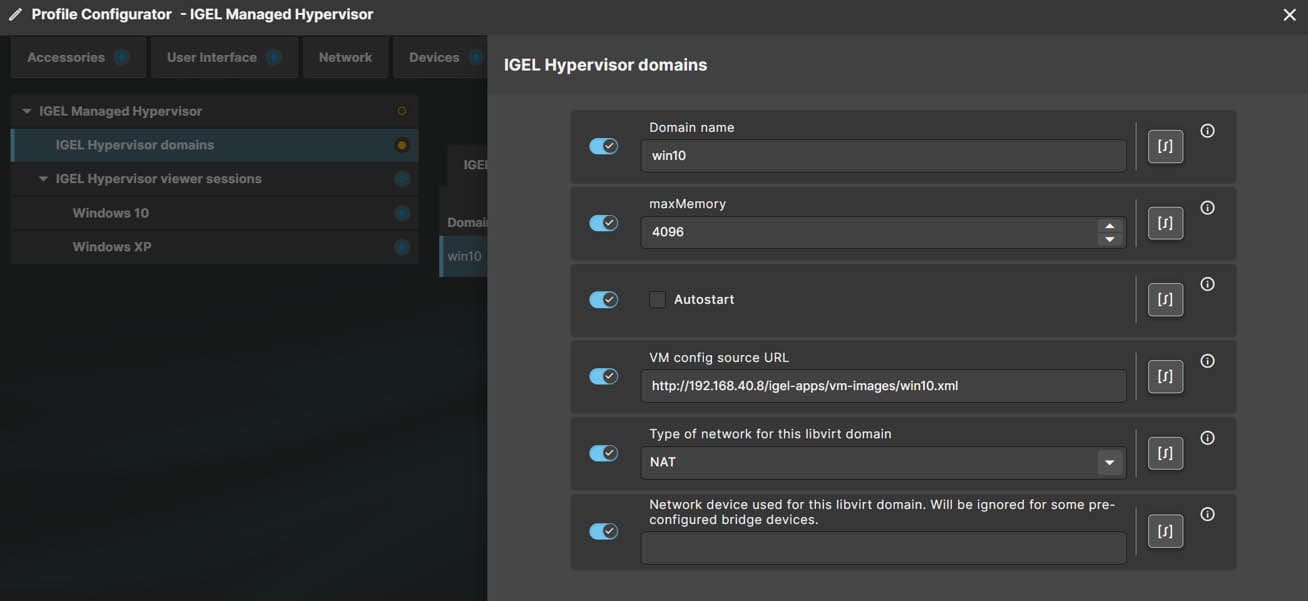
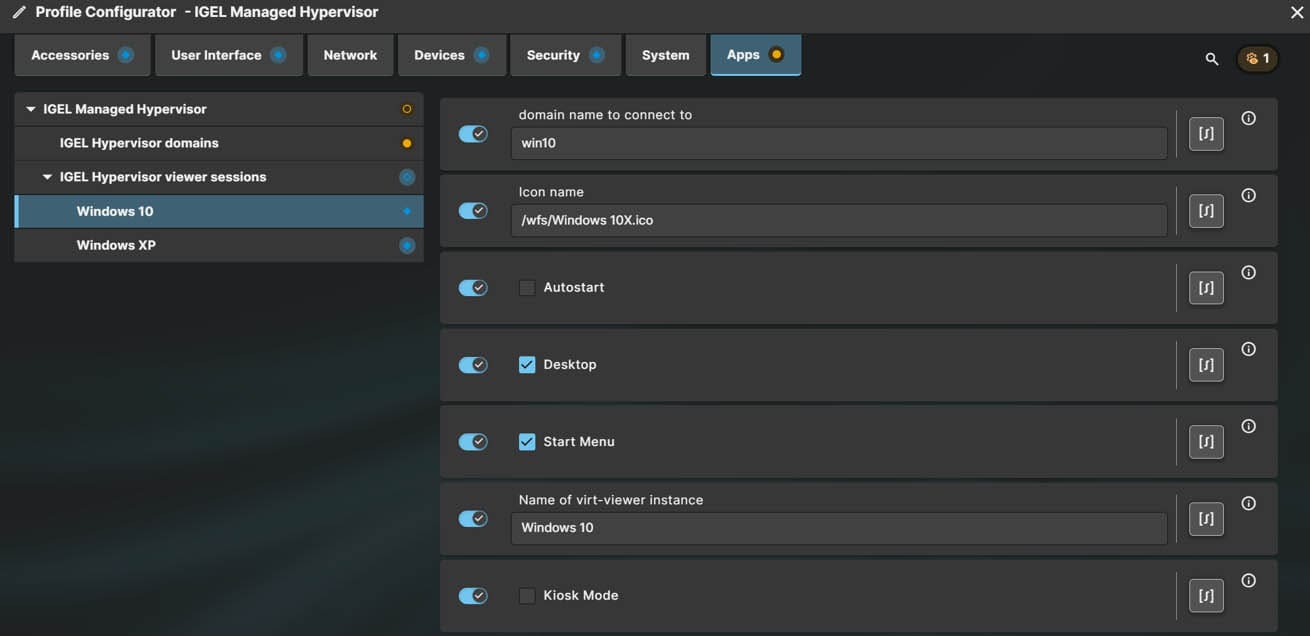
IGEL Hypervisor viewer sessions are used to create an icon which will start a VM viewer on IGEL OS allowing you to see the VM screen, select if you want the VM to auto-start, where the icon will be displayed and if you want the VM to run in kiosk mode.
Apply the profile settings and assign it to a target device.
Manage
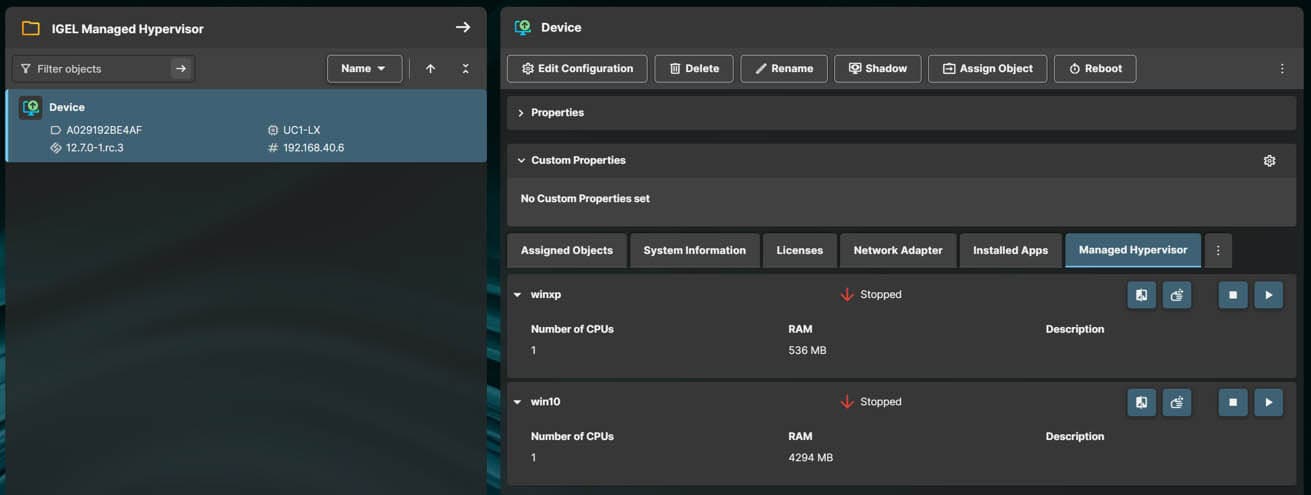
If all has gone well, you will now have a VM successfully deployed and running. To manage the VM navigate to the OS12 device in UMS, there will be a new TAB called Managed Hypervisor, click this and you will see the VM’s installed on the device and their status. From here you can perform various management tasks, such as, Start, Stop, Delete and re-image.
There we have it, four simple steps to getting your first IGEL Managed Hypervisor VM up and running.
If you would like to learn more about the IGEL Managed Hypervisor I will be running Webinars on Wednesday 14th May 2025 diving further into the details, discussing where IMH fits and running through setting everything up.
Registration links below:
10:00am BST | 10:00am ET | 16:00pm AEST
The post How to deploy a VM with IGEL Managed Hypervisor in four simple steps appeared first on IGEL.
]]>The post The hybrid multicloud future is here. Are your endpoints up to the task? appeared first on IGEL.
]]>How did we get here?
The last decade has seen increasing use of public cloud services to deliver apps and desktops to end-users. As the pendulum continues to swing more toward public cloud services to allow companies to back away from the high ongoing cost and labor of maintaining their own data centers and VDI networks, the traditional VDI providers are now providing companies like Microsoft, AWS, Google, and others to deliver ubiquitous cloud desktop and app delivery services. In fact, according to Cybersecurity Insiders, as of early 2025, 54% of organizations have adopted hybrid cloud models, integrating on-prem and public cloud environments to optimize flexibility and control. And that upward trend is showing no signs of slowing down.
The key is to enable seamless co-existence and transition from the many thousands of existing private clouds that run within on-prem data centers. Having already established itself as the leading provider of hyperconverged infrastructure (HCI) for private cloud delivery of virtual apps and desktops, Nutanix rapidly assumed leadership in enabling an easily managed, unified approach to seamless enterprise private/public virtual desktop and app delivery: namely, the hybrid multicloud.
The role of the hybrid multicloud endpoint
Now that hybrid multicloud is here to stay and growing, one critically important factor is the security, digital experience, and cost-effectiveness of the end-user and their endpoint device.
Traditional fully-contained Windows devices represent a distinct mismatch with how access to apps and desktops has evolved, with the following most glaring deficiencies:
- Labor-intensive, disruptive, time-consuming updates
- Limited flexibility in adapting to business needs
- Security vulnerabilities caused by decentralized setups
- Cumbersome management and limited enterprise-wide insight
- Costly and cumbersome management processes (e.g., OS and agent updates)
Fueled by the Nutanix Cloud Platform, the hybrid multicloud requires lean, secure endpoint devices that “don’t get in the way” of what end-users need and what IT organizations must enforce. Hybrid multicloud endponts must be malware resistant, resilient in the face of potential disruption, enable optimal end-user performance, and easy to manage at scale across a widely distributed workforce. Enter IGEL OS, the secure endpoint OS platform for now and next, and the IGEL Preventative Security ModelTM.
A lean, secure endpoint unleashes the full power of the hybrid multicloud
The IGEL Preventative Security ModelTM (PSM) serves as the foundation for a secure, malware-resistant, agentless end-user experience that avoids cyberthreats like ransomware that commonly attack vulnerable endpoints while freeing up resources to enable a highly productive end-user digital experience. Working hand-in-glove with a broad array of proven, IGEL Ready security technology partners including Nutanix, the IGEL PSM casts a broad, protective defense over end-user device roles and use cases, from hospital clinicians to financial services employees to retail workers. The benefit is clear – while Nutanix enables and fuels the managed, efficient, and productive hybrid multicloud, the IGEL OS platform with the IGEL PSM helps to protect your end-users’ devices and enable consistently excellent user experiences without the security, management, and performance overhead limitations of traditional approaches. Thus, the IGEL OS platform is not only the ideal complement to Nutanix for modern end-to-end computing, IGEL OS is the perfect endpoint for the hybrid multicloud.
Why Nutanix Plus IGEL?
Nutanix is an IGEL Ready partner and recently participated as a gold level sponsor at the recent IGEL Now and Next event in Miami. At the event, IGEL interviewed Jim Luna, Global Head of Business Development – Cloud and Technology Alliances at Nutanix, on the relationship between IGEL and Nutanix. Virtualizing Windows (including Windows 11) with virtualization/broker software running on the Nutanix Cloud Platform solution in your datacenter or cloud, and replacing Windows or any other OS with IGEL OS on your endpoint devices enables a modern, streamlined, flexible, and resilient approach to desktop management and control.
“At Choice Solutions, we’re focused on delivering secure, scalable, and future-ready solutions that enable our customers to thrive in today’s hybrid multicloud environments. Partnering with IGEL and Nutanix allows us to do exactly that. Together, we provide a seamless, cost-efficient platform that simplifies endpoint management, strengthens security, and delivers a consistent, high-performance user experience across any location or workload.” — Jim Steinlage, President & CEO, Choice Solutions
The following benefits can be quickly realized, all of which should be considered “table stakes” for successful hybrid multicloud computing:
- Improved Scalability
Nutanix enables organizations to efficiently and cost-effectively scale from hundreds to thousands of virtual desktops while using multiple private/public clouds. Its rapid deployment capabilities help ensure businesses can meet both immediate and long-term demands. The IGEL OS platform makes it easy to quickly scale the number of end-users, especially during rapid expansion periods or M&A transactions.
- Advanced Security
Nutanix seamlessly supports all the security features required of Windows 10 and Windows 11 apps and desktops, helping businesses safeguard their systems from modern threats. The IGEL OS platform complements Nutanix on the endpoint as a lean, minimal software footprint OS with near zero overhead, making it a non-target for cyber-attacks. The IGEL PSM sets IGEL apart with robust security and protective malware/ransomware resistance, and includes:
- tamper-resistant, read-only OS
- no local data storage on the device
- trusted application platform integrity verification
- modular design minimizes the attack surface
- extensive integration with leading security, authentication, SSO, and SASE technologies
- Streamlined IT Management and Control
Centralized IT operations on the Nutanix platform simplify desktop management, with:
- Faster recovery and easier updates
- Integrated file services for efficient data management
- Single-click disaster recovery solutions
Likewise, centralized web-based IGEL Universal Management Suite (UMS) and IGEL App Server service offer:
- Full management and control for up to 100K+ IGEL endpoints
- Easy, efficient software updates – say good-bye to the giant software release
- Keen insight with corrective measures for all endpoints across the enterprise
- Integration with other management/service systems via a REST API
- Lower Costs
Switching to virtualized environments and avoiding endpoint hardware swap-outs can significantly cut costs. So can optimizing the use of both private infrastructure and public cloud-based services. On endpoints, potential for significant cost savings can be achieved through repurposed device hardware, reduced IT overhead, and lower energy consumption as leaner, more efficient endpoints can typically run for years longer.
- Efficient Operations to Promote Sustainability Goals
Nutanix can help organizations pursue their sustainability goals through opportunities to reduce energy consumption and e-waste, all while maintaining top-tier performance. IGEL does likewise through opportunities to extend the life of your existing endpoints, including those migrated from Windows 10 to Windows 11 (and keeping them out of landfill sites), and enable the use of energy-efficient endpoint devices like thin and zero clients.
What Sets Nutanix Apart?
The Nutanix hybrid multicloud platform offers a seamless environment for on-premises, cloud, and edge systems. Key features include a flexible pay-per-use model that helps ensure organizations pay for actual usage, optimizing infrastructure costs; consistent performance via localized data management for reliable user experiences across workloads; and a future-ready hybrid architecture design that helps to maintain security and delivers simplicity, while also being cost-effective and highly scalable. In essence, Nutanix bridges the gap between public clouds and an organization’s private cloud infrastructure to create a seamless, fully managed multicloud environment where apps and data can reside anywhere. At the edge, IGEL offers the ideal endpont “on-ramp” to the Nutanix-enabled and powered multicloud, for end-users located anywhere.
What Sets IGEL Apart?
As the secure endpoint OS platform for now and next, IGEL OS on your endpoints serves as the ideal, future-ready complement to Nutanix-powered hybrid multicloud environments. In particular, the following distinct advantages set the IGEL OS platform apart from any other endpoint OS alternatives:
- Secure: The IGEL Preventative Security ModelTM turns your endpoints into non-targets and helps protect your people and their devices from cyber-attacks
- Excellent performance with business continuity: Lean, efficient IGEL OS improves endpoint performance; inherent resilience gets your end-users quickly up and running after any form of work stoppage (e.g., natural disaster, human error, malware episode)
- Future-Ready Design: IGEL OS is designed as the ideal endpoint OS in a hybrid multicloud world for your digital workspaces – secure browser, SasS, DaaS, and VDI
- TCO and sustainability: IGEL provides opportunities for CapEx and OpEx savings, reduced energy costs, and reduced e-waste in landfills
Choose the end-to-end solution designed for the hybrid multicloud.
Hybrid multicloud computing has arrived and it continues to grow. Nutanix and IGEL can help make your entire enterprise more secure and economical, and easier to manage, while giving your end-users a performance and experience upgrade! The Nutanix Cloud Platform, IGEL OS, and the IGEL PSM combine for a more efficient and improved end-user computing environment with improved security, management, control, and insight.
Be fully armed to take maximum advantage of the future of hybrid multicloud computing with Nutanix and IGEL.
You are encouraged to attend the Nutanix .NEXT 2025 conference and expo in Washington D.C. May 7 – 9, where IGEL is a Silver sponsor of the event. Stop by the IGEL booth in the Solutions Expo to see the latest solutions and innovations from IGEL, and don’t miss IGEL’s John Walsh, who will be presenting at our sponsored breakout session titled Beyond the Endpoint: Enabling Zero Trust Across IT and OT with IGEL and Nutanix. A brief extract of John’s talk follows:
Looking to extend Zero Trust beyond the data center? Join IGEL’s Field CTO – Critical Sectors, John Walsh at .NEXT to discover how IGEL’s secure, read-only OS and Preventative Security Model are helping organizations protect their IT and OT environments—without adding complexity or cost. This breakout will show how IGEL integrates with Nutanix to deliver a unified, policy-driven security layer across endpoints and across the enterprise, enabling faster modernization, simplified compliance, and safer access to critical applications in even the most regulated industries. Whether you’re dealing with legacy systems, hybrid and distributed workforces, or edge computing, this session will show you how to turn Zero Trust into a practical, scalable, and cost-effective reality.
are helping organizations protect their IT and OT environments—without adding complexity or cost. This breakout will show how IGEL integrates with Nutanix to deliver a unified, policy-driven security layer across endpoints and across the enterprise, enabling faster modernization, simplified compliance, and safer access to critical applications in even the most regulated industries. Whether you’re dealing with legacy systems, hybrid and distributed workforces, or edge computing, this session will show you how to turn Zero Trust into a practical, scalable, and cost-effective reality.
_______________________________________________________________________________
Take advantage of the Nutanix free test drive
Check out the IGEL OS platform and the IGEL Preventative Security ModelTM for yourself!
Download a trial version
About IGEL
IGEL is the leading secure endpoint OS platform for enterprises now and next. Designed for secure browser, SaaS, DaaS, and VDI, the IGEL OS platform delivers a first-class user experience that is seamless to manage – saving money, fueling growth, advancing sustainability, and driving organizations forward. IGEL OS takes a zero-trust approach to security through the unique IGEL Preventative Security Model , removing the attack vectors often exploited by bad actors. Trusted by leading healthcare, financial services, retail, manufacturing, and government leaders worldwide, IGEL has a growing ecosystem of more than 100 integrated IGEL Ready ecosystem partners in more than 50 countries. For more information on what IGEL can do for you, visit IGEL.
, removing the attack vectors often exploited by bad actors. Trusted by leading healthcare, financial services, retail, manufacturing, and government leaders worldwide, IGEL has a growing ecosystem of more than 100 integrated IGEL Ready ecosystem partners in more than 50 countries. For more information on what IGEL can do for you, visit IGEL.
The post The hybrid multicloud future is here. Are your endpoints up to the task? appeared first on IGEL.
]]>The post Strengthening Cybersecurity in Healthcare appeared first on IGEL.
]]>The public comment period closed on March 7, 2025, with more than 4,000 responses. As healthcare IT teams await the final ruling, now is the time to strengthen endpoint security strategies—not just for compliance, but to ensure operational resilience in an increasingly hostile threat landscape.
HIPAA’s Modernized Security Expectations
The proposed updates reflect the realities of today’s cyber environment and push healthcare providers, payers, and business associates toward more prescriptive security controls, including:
- 72-hour system restoration for impacted ePHI environments
- Mandatory Multi-Factor Authentication (MFA)
- Data encryption at rest and in transit
- Comprehensive security policy documentation
- Annual asset inventories and network mapping
- Ongoing risk analysis and incident response readiness
How IGEL Helps Healthcare Meet HIPAA Security Requirements
IGEL’s Preventative Security Model (PSM) supports Zero Trust architecture and goes beyond traditional antivirus or EDR approaches. Here’s how IGEL helps organizations stay secure and compliant with the proposed HIPAA Security Rule:
| Capability | IGEL Key Benefits for HIPAA Compliance |
| 1. Read-Only OS Prevents Malware Execution |
|
| 2. Zero Trust Framework & Secure Identity Access |
|
| 3. Audit-Ready Compliance with Centralized Management |
|
| 4. Built-in MFA & Biometric Access |
|
| 5. Full Encryption & Secure Remote Access |
|
| 6. Rapid Disaster Recovery |
|
| 7. Cost-Effective, Sustainable Security |
|
Final Thoughts
The proposed HIPAA Security Rule changes will require healthcare organizations to adopt more proactive, tech-forward endpoint strategies. IGEL’s secure OS and management ecosystem are purpose-built to meet these demands—minimizing cyber risk while optimizing cost and compliance.
Take Action Now
Ready to align your endpoint strategy with HIPAA’s proposed security rules?
Contact IGEL to explore how our solutions can future-proof your compliance, recovery, and security posture—without needing to replace your hardware.
The post Strengthening Cybersecurity in Healthcare appeared first on IGEL.
]]>The post Securing the Edge: AWS and IGEL Unite at Now and Next 2025 appeared first on IGEL.
]]>As a proud Platinum Sponsor of the IGEL Now and Next 2025 conference, the AWS End User Computing team is excited to showcase our collaboration with IGEL to revolutionize secure endpoint management and cloud connectivity. This premier event offers a unique opportunity to explore how AWS End User Computing (EUC) services and IGEL secure endpoints to create robust, flexible, and secure digital workspaces.
Our platinum sponsorship underscores our commitment to customers and the vision we share with IGEL for the future of secure, cloud-enabled digital workspaces. Throughout the conference, the AWS team will be front and center, discussing the most pressing security and connectivity challenges faced by organizations today at our booth.
I’m thrilled to be participating in the keynote presentations on both Tuesday and Wednesday, where I’ll dive deep into how we are tackling our customers’ most critical concerns. Our focus remains squarely on customer obsession – understanding and solving real-world problems faced by IT teams in securing their distributed workforces while optimizing performance and cost-efficiency.
I’m also excited to announce that Melissa Stein, our Director of Product, EUC, will join Tuesday’s Women in Tech panel and will be presenting ‘Think end-to-end to work anywhere, secure everywhere’ in addition to Wednesday’s keynote.
Don’t miss this opportunity to engage directly with AWS experts, attend our keynote sessions, and visit our sponsor booth to experience firsthand how AWS and IGEL are shaping the future of secure, cloud-connected digital workspaces.
The post Securing the Edge: AWS and IGEL Unite at Now and Next 2025 appeared first on IGEL.
]]>
