The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The retail sector continues to experience an increase in cyber threats, driven by outdated infrastructure, distributed environments, and expanding attack surfaces. Recent data breaches involving well-known brands such as Harrods, Marks & Spencer, Cartier, The North Face, and Victoria’s Secret have brought this issue to light. These events underscore the dynamic and complex threat environment that retailers face today. They also emphasize that retail is a key target for well-resourced and opportunistic threat actors.
In the last two years, the retail sector has experienced a substantial increase in cybersecurity vulnerabilities and breaches, leading to serious operational and financial ramifications. In 2024, 80% of retailers reported being targets of cyberattacks, with over half admitting a growing sense of vulnerability to these threats[1]. The frequency and severity of these incidents are increasing: retail data breaches grew by 18% year-over-year in 2024, with the average breach now costing $2.96 million[2].
Ransomware continues to pose a sizable threat, with the retail industry being the second most targeted sector for ransomware attacks in 2023 and the first half of 2024. In this timeframe, the U.S. retail sector reported 256 ransomware incidents in 2024, an increase from 206 incidents reported in the first three quarters of 2023[3].
Understaffed IT teams, high turnover, and a lack of cybersecurity training, particularly for temporary and seasonal staff, have heightened vulnerabilities. The repercussions of these breaches go well beyond immediate financial impacts. Business disruptions and the damage to their reputation can be considerable and profound.
Notably, 33% of retailers have faced regulatory action due to inadequate protection of customer data[4].
What is especially concerning about these incidents is their tendency to exploit vulnerabilities that could be addressed with effective preventive security measures. This highlights the urgent need for a more comprehensive and strategic approach to cybersecurity.
Traditional cybersecurity measures aren’t keeping pace
The retail sector’s IT infrastructure is inherently vulnerable. The attack surface is wide with thousands of distributed locations, outdated systems that are challenging to update, third-party connections, and the need for constant uptime. Additionally, the rise of e-commerce has turned retail into a 24/7/365 operation, placing additional strain on IT resources and creating more potential vulnerabilities. Furthermore, risks extend beyond retail stores—logistics, inventory management, transportation, and backend systems all present possible attack access points.
Traditional security tools have not kept pace with the evolving landscape of cyber threats. Many of these solutions were originally designed for static and centralized environments, making them increasingly inadequate in the face of fast-moving threats that can easily exploit vulnerabilities across distributed and diverse endpoints such as laptops, smartphones, and cloud services, which often fall outside the direct control of traditional security measures.
Once attackers access a network, they can move laterally within the system, navigating various connected devices and systems. This lateral movement can occur alarmingly quickly, often within just a few minutes, enabling them to disable critical services and infrastructure before a retailer realizes it has been compromised.
Preventative Security as a Strategic Shift
Today’s retailers require lightweight, efficient, and functional security within limited infrastructure. More importantly, they need systems that stop breaches before they escalate.
This necessitates a strategic shift from reacting to preventing threats, and one way in which retailers can improve endpoint security is by adopting IGEL’s Preventative Security Model .
.
For retailers, IGEL OS, the Secure Endpoint OS for Now & Next:
- Immutable, read-only OS: Reduces exploitability and eliminates persistence of malware.
- Centralized configuration management: Via IGEL UMS, enabling rapid policy deployment across distributed fleets.
- Boot chain of trust: UEFI Secure Boot through to application launch, validating integrity at every step.
- PCI-DSS alignment: Designed to protect PII and cardholder data, reducing compliance burden.
- Single sign-on integration: With platforms like Okta, Entra ID, and Ping Identity to enforce identity-driven access control.
- Peripheral and protocol compatibility: Ensures business continuity without compromising usability.
- Ransomware mitigation: Architectural safeguards lower both the probability and the impact of endpoint compromise.
Rethinking Endpoint Recovery for Business Continuity
For organizations still relying on traditional endpoints, recovery from a security event often translates to logistical disruption. Device reimaging, hardware replacement, and manual reconfiguration introduce significant delays—especially in distributed retail environments with limited IT presence. When laptops are compromised or encrypted by ransomware, recovery can require full device replacement, resulting in downtime, shipping delays, and high support overhead.
IGEL OS can be used to return services utilizing the compromised endpoint hardware in place. IGEL OS runs from a read-only partition with no local data persistence. Compromised endpoints can be quickly restored using IGEL USB Boot, Dual Boot, or managed hypervisor fallback methods. This eliminates the need for physical device swaps or complex reimaging workflows.
The result is a business continuity model that is immediate, scalable, and resilient—even in environments with constrained IT support. IGEL allows organizations to return to a known-good state in minutes, not days, reducing operational disruption and breach containment costs. When combined with centralized policy enforcement via IGEL UMS, this architecture ensures security and continuity across the entire endpoint estate—without increasing complexity.
Final Thoughts
Retail security leaders are no longer measured solely by breach prevention—but by how effectively they limit operational impact when threats materialize. The endpoint remains one of the most exposed surfaces in this equation. IGEL offers an architecture that reduces the likelihood of compromise and provides rapid continuity for traditional endpoints. For CISOs, adopting a preventative, resilient endpoint strategy is not just a security imperative—it’s a business enabler.
To learn more about IGEL’s Preventative Security Model and IGEL OS: The Secure Endpoint OS for Retail, click here.
[1] https://www.vikingcloud.com/blog/retail-cybersecurity-stats-threats-and-solutions
[2] https://www.nccgroup.com/us/is-your-retail-business-prepared-for-cyber-threats-this-2024-holiday-season/
[3] https://cyberint.com/blog/other/retail-threat-landscape-2024/
The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The post How to deploy a VM with IGEL Managed Hypervisor in four simple steps appeared first on IGEL.
]]>If you are interested as to why we are releasing a Hypervisor, I recommend you read this Blog post: https://www.igel.com/blog/igel-managed-hypervisor-secure-your-legacy-workloads/
Let’s get started!
What you will need
- IGEL Universal Management Server (UMS) v 12.07.100 or later
- IGEL OS12.6.1 or later
- IGEL Managed Hypervisor App (releasing in Q2 2025)
- WebDAV server to store and deploy the disk images (I used IIS on my UMS server for this in a LAB environment)
The process is very simple; create a VM on an OS12.6.1 or later endpoint, capture the disk image, create a profile in UMS to deploy the disk image to a target OS12.6.1 or later endpoint, then you can remotely manage OS12 and the VM from UMS.
Create
The first step is to create your own ‘Golden Image’. Open the Virtual Machine Manager, click File, New Virtual Machine.
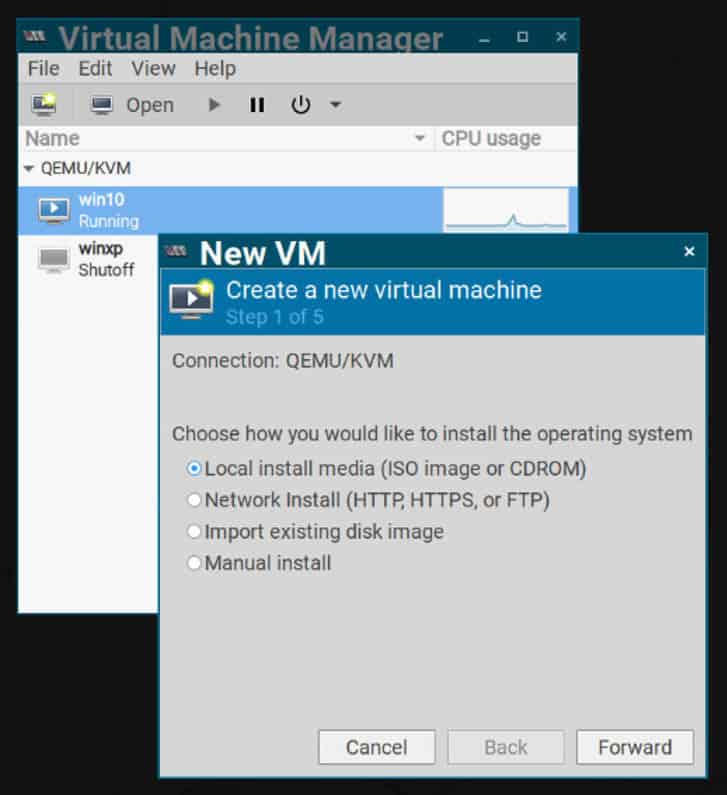
This starts with a wizard which will take you through the steps to create the virtual machine. From selecting the operating system, the storage, CPU and memory to the attached peripherals. In my case I used
a USB storage device with Windows10 and Windows XP ISO files.
Install your selected OS and configure as required.
Capture
Now you have your ‘Golden Image’ we can capture the image and get it ready for deployment. Part of the IGEL Managed Hypervisor app is an export utility called IMH Exporter. To export the VM image to the WebDAV server simply open the IMH Exporter, enter the URL to the WebDAV server and select the VM name you want to export.
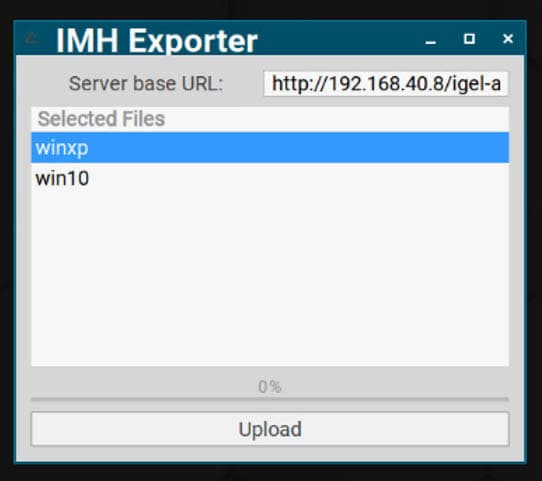
The IMH Exporter will then create two files on the WebDAV server: %vm_name%.img and %vm_name%.xml. The .img file is the disk image (this will be a large file, you will need to consider the storage size and network when exporting) the .xml file is a configuration file detailing all the component the VM needs, such as network, memory, CPU etc.
Deploy
Now we have the Image and the config file we can create a UMS Profile to deploy the Image to a target device (Tip: make sure you don’t send the VM to the device you used to create it on as you will get inconsistent results, if you need to use the same device remove the golden image first)
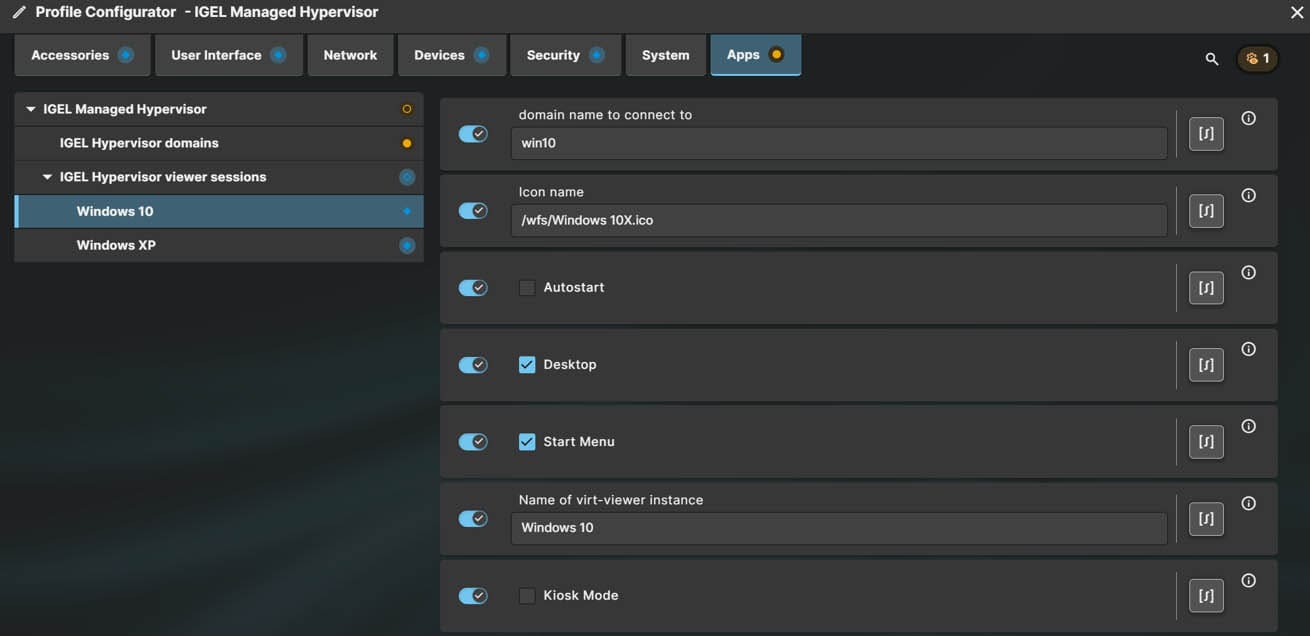
There are two sections in the IMH App Profile, IGEL Hypervisor Domains and IGEL Hypervisor viewer sessions.
IGEL Hypervisor Domains is used for image deployment. (a domain in this case is the name of the VM). Fill out the details for your VM and the URL to the XML file on the WebDAV server.
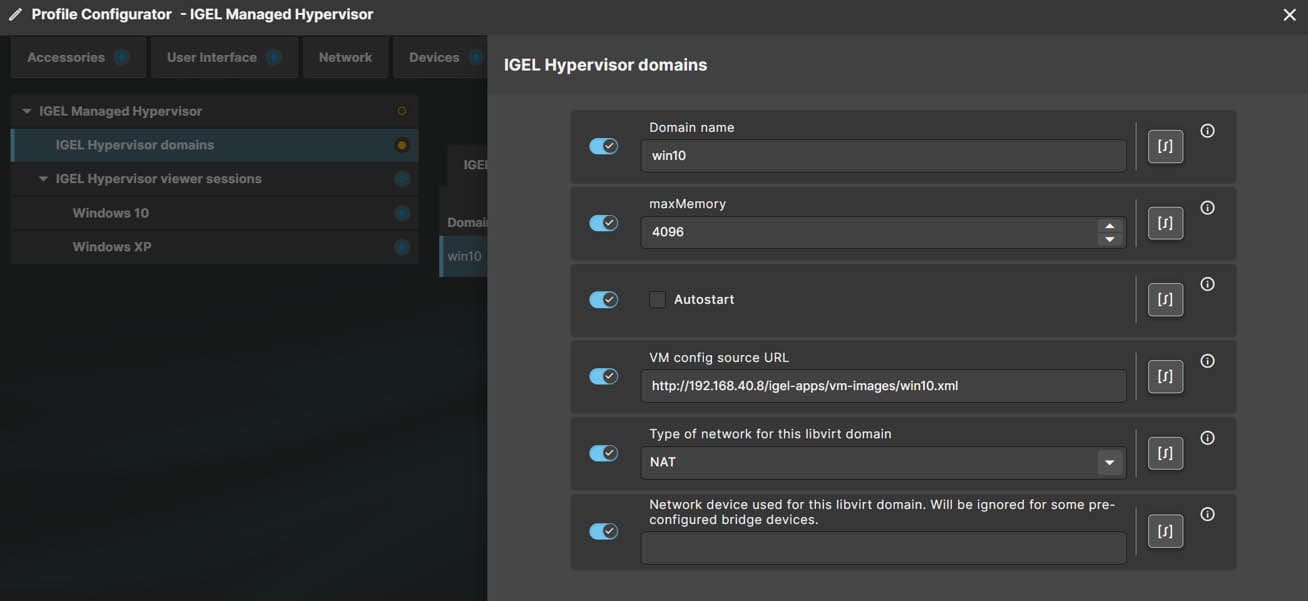
IGEL Hypervisor viewer sessions are used to create an icon which will start a VM viewer on IGEL OS allowing you to see the VM screen, select if you want the VM to auto-start, where the icon will be displayed and if you want the VM to run in kiosk mode.
Apply the profile settings and assign it to a target device.
Manage
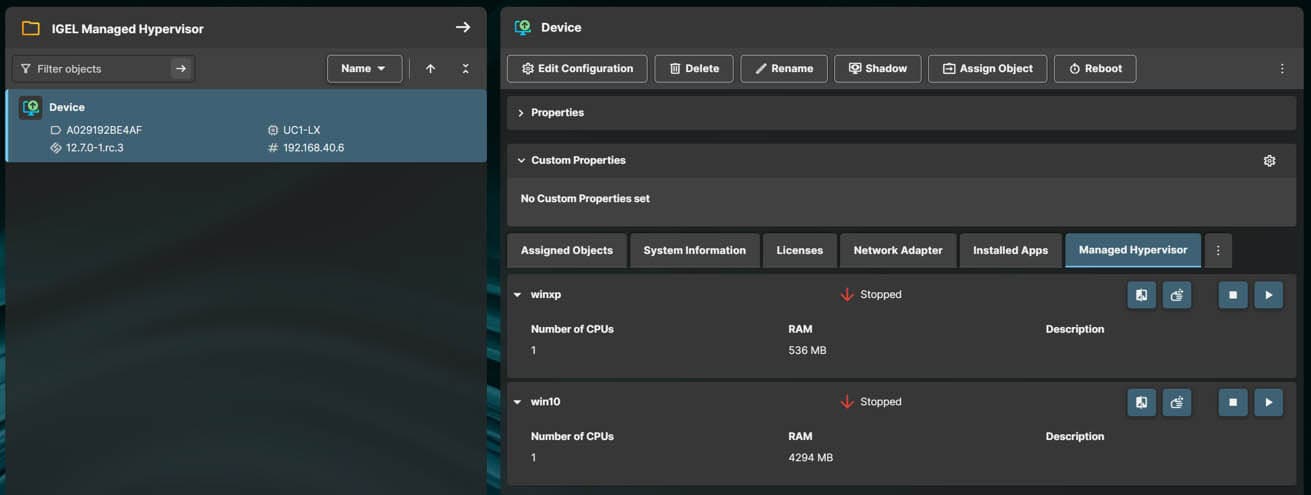
If all has gone well, you will now have a VM successfully deployed and running. To manage the VM navigate to the OS12 device in UMS, there will be a new TAB called Managed Hypervisor, click this and you will see the VM’s installed on the device and their status. From here you can perform various management tasks, such as, Start, Stop, Delete and re-image.
There we have it, four simple steps to getting your first IGEL Managed Hypervisor VM up and running.
If you would like to learn more about the IGEL Managed Hypervisor I will be running Webinars on Wednesday 14th May 2025 diving further into the details, discussing where IMH fits and running through setting everything up.
Registration links below:
10:00am BST | 10:00am ET | 16:00pm AEST
The post How to deploy a VM with IGEL Managed Hypervisor in four simple steps appeared first on IGEL.
]]>The post Strengthening Cybersecurity in Healthcare appeared first on IGEL.
]]>The public comment period closed on March 7, 2025, with more than 4,000 responses. As healthcare IT teams await the final ruling, now is the time to strengthen endpoint security strategies—not just for compliance, but to ensure operational resilience in an increasingly hostile threat landscape.
HIPAA’s Modernized Security Expectations
The proposed updates reflect the realities of today’s cyber environment and push healthcare providers, payers, and business associates toward more prescriptive security controls, including:
- 72-hour system restoration for impacted ePHI environments
- Mandatory Multi-Factor Authentication (MFA)
- Data encryption at rest and in transit
- Comprehensive security policy documentation
- Annual asset inventories and network mapping
- Ongoing risk analysis and incident response readiness
How IGEL Helps Healthcare Meet HIPAA Security Requirements
IGEL’s Preventative Security Model (PSM) supports Zero Trust architecture and goes beyond traditional antivirus or EDR approaches. Here’s how IGEL helps organizations stay secure and compliant with the proposed HIPAA Security Rule:
| Capability | IGEL Key Benefits for HIPAA Compliance |
| 1. Read-Only OS Prevents Malware Execution |
|
| 2. Zero Trust Framework & Secure Identity Access |
|
| 3. Audit-Ready Compliance with Centralized Management |
|
| 4. Built-in MFA & Biometric Access |
|
| 5. Full Encryption & Secure Remote Access |
|
| 6. Rapid Disaster Recovery |
|
| 7. Cost-Effective, Sustainable Security |
|
Final Thoughts
The proposed HIPAA Security Rule changes will require healthcare organizations to adopt more proactive, tech-forward endpoint strategies. IGEL’s secure OS and management ecosystem are purpose-built to meet these demands—minimizing cyber risk while optimizing cost and compliance.
Take Action Now
Ready to align your endpoint strategy with HIPAA’s proposed security rules?
Contact IGEL to explore how our solutions can future-proof your compliance, recovery, and security posture—without needing to replace your hardware.
The post Strengthening Cybersecurity in Healthcare appeared first on IGEL.
]]>The post Expand App Access on IGEL OS with Progressive Web Apps appeared first on IGEL.
]]>Why Progressive Web Apps Matter
PWAs bridge the gap between web and native applications, delivering an app-like experience while remaining lightweight and browser-based. They bring several benefits, including:
- Offline Support – PWAs can function even when connectivity is limited.
- Push Notifications & Background Sync – Improves engagement and real-time updates.
- Cross-Platform Compatibility – Works seamlessly across devices and operating systems.
- Centralized Deployment – IGEL administrators can deploy PWAs to IGEL OS desktops, allowing users to access them just like any other application, with a seamless launch experience.
For IGEL OS users, this means another secure and efficient way to access enterprise applications while maintaining IT control and minimizing overhead.
Expanding Application Delivery: PWAs & Beyond
PWAs complement the existing application delivery methods IGEL already provides:
- Virtual Apps & Desktops via DaaS & VDI – With Omnissa, Microsoft AVD/Windows 365, and Citrix, organizations can virtualize applications securely without endpoint dependencies.
- Enterprise Browsers – IGEL OS natively supports Edge, Firefox, and Island, providing secure, direct access to web applications.
- IGEL Managed Hypervisor (IMH) – When Windows is required at the endpoint, IMH delivers an immutable, rollback-ready Windows instance for critical environments.
- Additional PWAs – expanding the number of PWA’s available from the IGEL App Portal now including Microsoft Office apps like Teams, Outlook, Word, Excel, PowerPoint, and Copilot, and Google Gmail, centrally managed and deployed for seamless access.
A Secure Foundation with the Preventative Security Model
Like all IGEL innovations, PWA support is built on the foundation of the Preventative Security Model (PSM), ensuring:
- A secure-by-design approach that eliminates attack vectors rather than reacting to them.
- Integration with IGEL’s security ecosystem, including authentication, encryption, and Zero Trust principles.
- Simplified management and control—centralizing security and access policies while reducing endpoint complexity.
A Unified Approach to Secure Application Access
With expanded PWA support, IGEL OS offers an even broader application access strategy that meets organizations where they are—whether through DaaS, VDI, enterprise browsers, hypervisor-based Windows, or IGEL native apps. By enabling centralized deployment of PWAs, IGEL ensures users experience them just like traditional applications, while IT maintains full control over security, configuration, and access policies.
Ready to Leverage PWAs on IGEL OS?
If your organization is looking for a modern, secure, and cost-effective way to deploy applications, PWAs on IGEL OS are an excellent option. Combined with our robust ecosystem of application delivery methods, IGEL provides the ultimate flexibility for secure enterprise access.
Would you like to explore how IGEL OS can support your digital workspace strategy?
View the IGEL PWA demo video
Contact us today to learn more.
View the Microsoft Teams PWA on IGEL App Portal
The post Expand App Access on IGEL OS with Progressive Web Apps appeared first on IGEL.
]]>The post How IGEL and Omnissa Deliver Secure and Efficient User Desktop and Application Solutions appeared first on IGEL.
]]>To begin to understand the impact of these two companies’ solutions, imagine a self-service approach to onboarding and accessing corporate computing resources. Simply adding users to an organization domain, the when, where, and how an end user sets up his or her workstation and gains secure access to applications is a completely automated process requiring no operational support from IT.
In this article, we will explore how these two companies work together to ensure flexible, scalable, secure, and cost-efficient access to virtual desktops and applications while delivering:
- End-to-End Security
- Service Continuity
- Enhanced User Experience
- Cost Savings
Meeting In the Middle
IGEL and Omnissa each provide separate halves of the desktop and application delivery solution stack. Omnissa manages the secure delivery of desktops and applications, and IGEL securely connects users to their desktop and application resources.
IGEL – The Endpoint Device Solution
The IGEL solution begins with the IGEL Secure Endpoint OS (aka IGEL OS). IGEL OS is a highly secure, fully encrypted, lightweight operating system designed specifically for accessing desktops and applications delivered by Omnissa. It provides unparalleled endpoint security through IGEL’s Preventative Security Model to ensure device integrity and improve stability while reducing its attack surface, which minimizes the risk of cyber threats like malware, ransomware, and other vulnerabilities.
to ensure device integrity and improve stability while reducing its attack surface, which minimizes the risk of cyber threats like malware, ransomware, and other vulnerabilities.
IGEL includes unified management that offers centralized control of all IGEL OS-powered devices. This is achieved through a next-generation cloud platform called IGEL Cloud Services that includes the IGEL App Portal, the IGEL Onboarding Service, Licensing, and Insights.
This combination of IGEL OS and IGEL Cloud Services provides device deployment and configuration, control over local applications, and secure access to computing resources delivered by Omnissa.
Omnissa – The Desktop and Application Service Solution
Omnissa Horizon 8 enables the creation and management of virtual desktops and applications, and it also incorporates security features like multi-factor authentication (MFA), support for smart cards, and secure tunneling through the Unified Access Gateway.
To reduce the time and complexity of desktop management and application updates, Omnissa provides streamlined deployment and automation through technologies such as Instant Clones, which enable rapid provisioning of desktops, and App Volumes, for on-demand delivery of applications.
Omnissa Workspace ONE is a support platform that integrates device management, application management, access control, and more into a unified solution. It includes Identity and Access Management to provide secure single sign-on (SSO) and multi-factor authentication (MFA), ensuring secure access to applications. Workspace ONE also incorporates robust security features such as conditional access policies, data loss prevention, and real-time security monitoring.
Finally, through the Workspace ONE Intelligent Hub running on an IGEL edge device, IT administrators can view and control devices in the Workspace ONE UEM Console and proactively monitor users’ workplace experience using DEX.
Putting Everything Together
With IGEL and Omnissa fully in place, a user’s initial deployment of a workstation and connection to his or her computing resources works as follows:
- Powers up the workstation device running IGEL OS.
- Configures the network connection, wired or wireless as required
- Authenticates against IGEL Onboarding Service using domain credentials
- IGEL Onboarding Services connects to Omnissa Identity Service
- Multi-factor Authentication is used when required
- The IGEL device is configured, updated, and the requisite applications (e.g. Omnissa Horizon Client, Omnissa Intelligent Hub, Zoom VDI Plugin, etc.) are automatically installed.
- User is prompted to register the IGEL device with Workspace ONE UEM.
- The IGEL device presents the user with Omnissa Access Login screen.
- User logs into Omnissa Access portal using MFA as required.
- User is automatically connected using SSO (access tokens) to Horizon Desktop using Horizon Blast protocol
- Desktop is automatically provisioned by Horizon management plane
- User applications are delivered on-demand using Horizon App Volumes
After initial deployment of the workstation, future connections to the Horizon desktop and application resources begin with the Omnissa Access Login screen (Step #6 above).
Conclusion
The combination of the IGEL Secure Endpoint OS, IGEL Cloud Services, and Omnissa Horizon backed by Workspace ONE represents a powerful, cost-effective, and secure solution for delivering virtual desktops and applications. IGEL transforms everyday hardware into secure and efficient endpoints, while Omnissa provides the robust Horizon platform for accessing corporate resources from anywhere, anytime. Together, they offer enterprises a secure, manageable, and scalable VDI environment that meets the demands of a modern workforce.
To learn more about IGEL and Omnissa, visit the IGEL Omnissa Partner web page or complete the online webform to test IGEL OS with Omnissa Horizon and Workspace ONE.
The post How IGEL and Omnissa Deliver Secure and Efficient User Desktop and Application Solutions appeared first on IGEL.
]]>The post Important fix for IGEL AVD App appeared first on IGEL.
]]>As IGEL works through our own QA testing customers wishing to have early access can request a private build or technical preview. To get this please contact with your IGEL Sales Engineer or IGEL Support.
IGEL OS12 customers should request IGEL AVD App 1.2.1.rc1 or 1.3.0.tp5. IGEL AVD App 1.3.x enables Smart Card authentication and should be requested if you are using or testing this functionality. Otherwise please request 1.2.1.rc1.
Following your request for RC, IGEL will contact you as soon as the GA versions are available.
Also included in the fixed RD Client SDK is a fix for reconnect session hangs when using RDP Shortpath (UDP traffic).
The post Important fix for IGEL AVD App appeared first on IGEL.
]]>The post Serious about security? Come to DISRUPT 24 and find out why you should be. appeared first on IGEL.
]]>At IGEL DISRUPT in Miami, learn and live the Preventative Security Model, Chain of Trust, and other components in the IGEL OS architecture mean and how they will help you avoid today’s modern cyber threats. You will get the details on how the modular operating system helps you avoid exposing risks, get insights on what the read-only operating system assists with when it comes to operating system reliability, and learn why IGEL will help protect intellectual property. It will all be combined with a high-stakes demo, making the audience much more comfortable choosing IGEL OS as an endpoint strategy, for me as a presenter – very risky!
Come see ‘Preventative Security Model, Chain of Trust, Read-Only Operating System … What does it mean in reality?’ in the Security track and experience the ‘WHY IGEL OS!!’
Check out the full DISRUPT agenda: https://www.igel.com/disrupt24/
I’ll see you in Miami.
/Fredrik Brattstig
The post Serious about security? Come to DISRUPT 24 and find out why you should be. appeared first on IGEL.
]]>The post Revolutionizing the Enterprise Endpoint OS: IGEL’s Game-Changing Approach to the Secure Endpoint OS Now and Next appeared first on IGEL.
]]>- Enterprise IT continues its march away from running workloads at the endpoint, and embraces SaaS, DaaS, VDI and secure browsing
- A move to Windows 11 will be top of mind for organizations in 2024. Not only are Microsoft recommending moving to running Windows in the cloud, they are also calling out Azure Virtual Desktop and Windows 365 in their earnings announcements as surpassing $1B in revenue
- Cyber-security remains atop the headlines in terms of policy, ransomware attacks, and the impact of AI
- 2024 sees the start of mandatory sustainability disclosures in the EU. While wholesale greenhouse gas (GHG) reporting is not mandatory in the US, many organizations are actively reporting on sustainability and California’s Climate Accountability Package enforces mandatory scope 3 reporting on any organizations with revenues of more than $1B that does business in California.
Building on our rich history of engineering excellence and industry partnerships, as we enter 2024 IGEL is uniquely positioned to help organizations meet the challenges outlined above while also reducing IT spend.
Here’s how:
Redefine Endpoint Security.
IGEL’s Preventative Security Model eliminates the endpoint vulnerabilities targeted by bad actors. IGEL Endpoint OS supports Zero Trust and SASE initiatives through:
eliminates the endpoint vulnerabilities targeted by bad actors. IGEL Endpoint OS supports Zero Trust and SASE initiatives through:
- Read-Only OS. Users cannot unwittingly (or wittingly) download and install malware to the endpoint.
- No local storage of data. No customer, patient, financial or other information can be downloaded to the endpoint or exfiltrated through attached USB devices. This ensures lost or stolen devices do not create a breach investigation, or that malicious internal users are not able to surreptitiously steal data.
- Trusted Application Platform. A secure boot process ensures no code has been tampered with. A reboot returns the device to a known good state enabling organizations to confidently restore services in minutes rather than weeks or months from a cyber-attack
- Authentication, SSO Integration and SASE. IGEL partners with the leading authentication vendors including Microsoft, Imprivata, Okta, Ping Identity, VMware and Citrix to integrate with broader standards. We also partner with SASE and Secure Service Edge partners to optimize Zero Trust implementations
- Modular Design. At just 2GB, IGEL OS is a much smaller attack surface than a traditional endpoint OS. IGEL OS 12 only contains what the user needs to accomplish their tasks. Additional functionality such as partner integrations with Citrix and VMware, the above security vendors and more, can be downloaded from the IGEL App Portal.
Focus on Vertical Solutions
IGEL recognizes that the challenges, workflows, governance requirements and necessary integrations can be unique across industries. We have formalized partnerships and deep integration with the major software and hardware partners in each industry vertical. IGEL is utilized by many of the largest organizations around the world including:
- Healthcare & LifeSciences: 5 of the top 5 hospital groups in Europe. 5 of the top 10 biggest Healthcare providers in the US. Many of the world’s largest Healthcare Payers/insurers and 5 out of 10 leading pharmaceutical manufacturers
- Manufacturing – 10 of top 10 in Europe. 4 of the top 10 in North America
- Retailers: 5 of the top 10 North America
- Finance: 3 of the top 10 Banks in Europe.
- Government: Used across Federal such as Defence as well as State & Local government around the world.
Minimizing TCO and Maximizing Sustainability
An analysis of real-world customer deployments from IGEL’s TCO tool reveals that before IGEL, the total cost per endpoint device including the tangibles such as device purchase, software, deployment, management etc. is approximately $1000 per device per year over a 4-year period (assumes a device refresh every 4 years). With IGEL, we are able to reduce those costs between 50% and 75% (sometimes more) through:
- Removal of the various security and management agents that need to be selected, purchased, tested, deployed, managed etc.
- Enabling the purchase of devices with less powerful processors as the applications and workloads have been moved to SaaS, DaaS or VDI
- Extending the lifecycle of the endpoint from 3 to 5 years to 6 to 8 years.
With organizations assessing whether Windows 11 in the cloud is the best option, implementing IGEL can help optimize budget spend away from the constant endpoint budget drain, to a more sustainable cloud first approach. Please contact IGEL for your customer TCO analysis
The Power of Partnership
IGEL is a partner centric company. From leading software and hardware companies, including Citrix, Microsoft, VMware, Lenovo, LG, and HP, to vertical specific partnerships including Imprivata. Through these collaborations, we can provide tailored solutions that meet requirements unique to each of our targeted industries.
IGEL is also a 100% channel-focused company. Our channel partners are a cornerstone of our business, and we are fully committed to cultivating and maintaining strong partnerships with them.
Shaping the Future of Endpoint Security and Management
In 2024, IGEL will once again host the End User Computing event of the year, DISRUPT. IGEL DISRUPT 24 will be held in Miami from April 29 to May 1. We fully expect this to be the largest event ever and will be joined by the biggest names in the EUC and Security universe. We will also host a second event in September, IGEL DISRUPT EMEA in Munich.
Looking Forward to 2024
The end-user computing market is, arguably, ripe for its biggest shake up in almost 30 years. IGEL, with our technology and channel partners, is leading the change, helping our customers meet their security, cost and sustainability goals. Reflecting this, and as a symbol of our excitement in, and commitment to this market, you may have noticed that the IGEL.com website now reflects our new branding, messaging and excitement for the year ahead.
We look forward to working with you on shaping your endpoint security strategy both for now, and next.
The post Revolutionizing the Enterprise Endpoint OS: IGEL’s Game-Changing Approach to the Secure Endpoint OS Now and Next appeared first on IGEL.
]]>The post O’Boy, what a year! 2023 is almost in the books; let’s look in the rearview mirror. appeared first on IGEL.
]]>The IGEL App Portal opens possibilities for third-party software vendors to package and make apps available for the IGEL OS. Technologies like ControlUP Edge DX and Remote DX, deviceTRUST, and Liquidware Stratusphere UX have been added as the IGEL App SDK has been made available for Application vendors. Many more to come!
IGEL released the IGEL Windows 365 App, enabling easy access to Microsoft Windows 365 resources, and continues to evolve Windows 365 access together with IGEL Azure Virtual Desktop App.
IGEL has built and released the new IGEL Imprivata Agent, which makes IGEL OS the only endpoint OS enabling Imprivata Tap-and-Go for Windows 365 and Azure Virtual Desktop.
The IGEL Imprivata app also Tap-in to VMWare Horizon, and full support for Citrix Cloud and on-prem is around the corner.
With the new structure of IGEL OS, more use-cases are fulfilled. IGEL OS is now the ideal operating system for cloud-delivered workspaces, on-premises delivered Desktops and Apps and extends with “browser only” and local apps workflows.
During 2023, what everyone in the past referred to as Citrix was joined and split up into separate business units under the name of Cloud Software Group, where Citrix is one business unit, NetScaler is one, XenServer is one, etc. IGEL has a strong business relationship with Citrix and sees that the tech release avalanche that Citrix released is mind-blowing. So many new innovations have been released over the past year and integrated into Citrix Workspace App for Linux and IGEL OS. Citrix has also switched the focus from “Cloud only” to Cloud and On-Prem = Equals, working on feature parity and giving the customer the choice of where to run the workloads. Hybrid approach! From what I see with Citrix, there is no “One fits all” anymore. Good evolution!
On that note, Broadcom has acquired VMWare, and there is a market vacuum about what will happen with VMWare EUC. Hopefully, the VMWare Horizon (EUC) value will be valued by another organization and continue its long-term success as a VDI platform.
What’s intriguing to think of when it comes to Cloud vs. On-Prem is that Citrix CVAD/Daas and VMWare Horizon/Horizon Cloud have been making efforts to give the customer the Hybrid choice, Microsoft also has an answer: Azure Stack HCI, and with the ongoing development on Azure Virtual Desktop on Azure Stack HCI Microsoft is also acknowledging the hybrid choice. You might ask yourself why does anyone need on-prem when you have the hyper-scalers to run your workloads? The simple answer is twofold – Latency and legal requirements of the organizations.
Let’s quickly break this down: Latency – Depending on the type of workload you are delivering, low latency is key for good End User Experience. It can be about accessing local peripherals but also about delivering Rich media session streams. Think about the complexity of delivering multi-screen 4K resolutions at 60 frames per second; latency will be devastating. The legal side of things? Can governments put workloads and data in a cloud originating from another country?
With all the changes in the market that have been going on during 2023, this has also affected #Community. Looking at IGEL Community, it’s a growing resort for people discussing ideas and challenges. It is such a valuable platform, as when digging deeper into IGEL, what you see on the surface when test-driving the OS and management, there is so much more on the capabilities. When you start looking at scripting and customization, the IGEL Community is a resource to count on! The IGEL community grew 10% YtD in 2023.
Some of the Citrix User Groups announced changes from the CUGC brand to more of an EUC forum. I’ve seen that in the Nordics and the UK, at least. Citrix also announced changes to CUGC.
On a personal level, when it comes to community activities, I have been recognized by Citrix to become a CTP (Citrix Technology Professional) for my work in sharing knowledge with the community. IGEL also recognized me for my contributions and awarded me to become an IGEL Community Insider. I added my renewal of Microsoft MVP (Most Valuable Professional) for my third year and my NVIDIA NGCA (NVIDIA vGPU Community Advisor) for my fifth year.
The #AI revolution has started! Microsoft made an enormous footprint in making AI available for anyone, anywhere. Just look at Bing Chat. It gives anyone access to AI datasets and the possibility to leverage the new technology. Then, Co-Pilot rolled out to virtually all apps in the Microsoft portfolio. You are right; Microsoft wasn’t the main driver in the early stages of AI, though, by tight collaboration with OpenAI, they rapidly extended the AI use cases. All were announced at Microsoft Ignite mid-November -23. I’d say it has started!
IGEL has been going through organizational changes over the last year, including adding Klaus Oesterman as CEO and making significant changes to the leadership team. Exciting to see the changes in market focus. Keep your eyes out for all the changes that are in the pipeline!
So, what about 2024? My view of what’s coming!
IGEL will undoubtedly continue expanding the IGEL APP Portal portfolio. More apps from 3rd party software vendors will be made available. I’m thinking of Enterprise Browsers as they will play a more prominent role going forward. I know that we will see a remake of IGEL OS desktop GUI (Graphical User Interface) that takes the User Experience to a new level. We have already started to see usability improvements in IGEL OS supporting the mobile use case, and that journey will accelerate. Of course, IGEL will continue to update the Apps we package for OS 12.
I have seen numbers of 700 Million Windows 10 machines still alive. Those 700M (?) devices are facing the EOL of Windows 10 in 2025. It’s mind-blowing to think about the IT waste that will be created for all the machines that need to be replaced, as the hardware requirements for Windows 11 are different and more demanding. IGEL has the solution for you, together with Virtualization technologies and the delivery of virtual apps and desktops. What if you re-image your Windows 10 devices that will go out of support and instead put your Windows desktop in a data center, be it in the cloud or on-premises? You will be able to extend the lifetime of your existing machines and save lots of money, as you won’t need to buy new hardware. Your budget changes from CAPEX to OPEX and will be much more predictable. Did you know that somewhere around 85% of the carbon footprint results from the manufacturing and shipping of the unit? By not “rip and replace” your hardware, you will contribute to a greener world. Yes, some of the devices might need to be refreshed, and over time, devices need to be refreshed. That’s why IGEL is teaming up with manufacturers like Lenovo, LG, and HP. When the time comes, you will replace your hardware units with slimmer devices, again contributing to less emissions.
The race for Windows 11 upgrade will have to increase rapidly in 2024 for corporations to have a chance of avoiding running unsupported operating systems at mass in late 2025, which is a jeopardizing game. Hybrid work will continue to evolve, and I’m sure you want to ensure your users have a trouble-free endpoint in their hands. IGEL OS gives you good protection from Ransomware and other rouge code.
I believe we will see an extension of offloading technologies as optimizing the User Experience is still becoming more requested. New Microsoft Teams has just been released, indicating that new technology is coming to the virtualization EUC space.
The evolution of AI will probably introduce more players in the market on the GPU side. NVIDIA is leading this space, though I believe AMD and Intel can potentially deliver alternatives. At Microsoft Ignite, Satya Nadella announced Azure Maia AI chip. It will be interesting to follow this evolution!
IGEL will extend its MSP (Managed Service Provider) offering to expand its footprint in this segment. Broadening the usability and the licensing possibilities will be key to success.
I look forward to seeing more niche players in the IGEL App Portal as diversity adds value. I’m looking at Parallels RAS, HP Anywhere, Amazon Workspaces, and others. Would be really interesting to see more alternative VDI offerings. Citrix has a nice integration with Linux Desktops and Apps for VDI. ThinLinc is already part of the IGEL App Portal, which gives you Linux VDI. I’m also looking forward to seeing more local apps offered, where we today have Zoom, for instance. Why not give every customer the possibility to package their own apps?
With that said, I wish you happy holidays, a Merry Christmas, and a Happy New Year! See you in 2024!
/Fred
The post O’Boy, what a year! 2023 is almost in the books; let’s look in the rearview mirror. appeared first on IGEL.
]]>The post Experts Share Insights on Securing Healthcare Environments at DISRUPT on Tour appeared first on IGEL.
]]>Recently, we demonstrated IGEL OS for healthcare environments in our offices in Augsburg, Germany, in partnership with deviceTRUST, HP, Lenovo, and LG. The purpose of the event was to showcase the importance of future-proofing IT environments to provide the best possible patient care. Our team presented various concepts, technologies, and solutions that can meet the strictest requirements for safety, availability, and cost-effectiveness, which are vital in the healthcare sector.
During the event, we asked attendees about the most critical challenges facing healthcare organizations today. Their responses highlighted the importance of remote work, security, and cost pressure. Attendees emphasized the need for secure end devices and stable systems to support remote work. They also noted that on-site presence is still required for medical care. Furthermore, they stressed the importance of transparent login to ensure user acceptance of security measures, with data security being a top priority. Other important points raised included managing endpoints outside the network, the importance of manageability, and the need for two-factor authentication and biometric tokens for client security.
Ransomware is an ongoing threat
When asked about the specific challenges and opportunities for their organizations in 2024, attendees’ responses included the need for ISO certification and process customization to mitigate risks. Ransomware was identified as an ongoing threat, which in one case is being addressed by implementing LAN segmentation, zero trust mechanisms, and attack detection software. To prevent unauthorized executable files, one organization is restricting users from launching these types of files. The company is also implementing software solutions, such as XDR, training employees/raising awareness on cybersecurity, and deploying thin clients to improve protection.
When explaining the ransomware threat, one attendee who uses Citrix in combination with IGEL OS and Windows 10/11-powered endpoints said: “Our systems are largely protected from attacks and unauthorized access by technical measures such as firewall, proxy, 3-stage filtering of emails with a sandbox for email attachments, MFA, conditional access and administrative measures such as a role-based authorization concept and much more.”
The user is still the weakest link
They continued, “We regularly have penetration tests carried out to uncover security gaps and vulnerabilities, which we can then specifically close. In addition, all user data is secured via a system that technically prevents the backups from being compromised. There is no such thing as 100% security if people have access to the systems – the user is always the weakest link in the security chain. Ultimately, it is a matter of time when it hits us. However, we feel quite well prepared with our security measures.”
Overall, attendees enjoyed the event, with one organization saying, “The lectures were very interesting, and the customer presentations were very good. It was a relaxed environment for the exchange of ideas with manufacturers and customers.”
For more information on how IGEL is helping healthcare organizations achieve better patient outcomes with a simpler and more secure end-user computing approach visit: https://www.igel.com/customer-stories/healthcare/.
The post Experts Share Insights on Securing Healthcare Environments at DISRUPT on Tour appeared first on IGEL.
]]>
