The post FIDO2 Authentication to Azure Virtual Desktop and Windows 365 appeared first on IGEL.
]]>For my fellow tech enthusiasts, this blog offers my insights into this solution.
FIDO2 authentication is frequently asked for and can be seen as an evolution or replacement for the ‘legacy’ smart card secure authentication. FIDO2 improves authentication speeds, and the security sticks are in a user-friendly format.
Connecting to AVD and W365
Connecting to AVD and W365 is a three-step process (simplified), first you authenticate to EntraID web pages, then you authenticate to the Azure Gateways, and finally you Authenticate to the VM you want to remote. With the previous versions of the Microsoft RDClientSDK, the three steps were only possible using credential stuffing – capturing the username and password from the user, and then in a secure manner provide the captured credentials in the connection process.
A Game Changer
To enable FIDO2 authentication, IGEL implemented support for RDSAADAUTH enabled in the RDClientSDK. Simplified, it gives the user the possibility to Authenticate to EntraID, to retrieve a token, RDSAADAUTH then takes this token and presents it to the Azure Gateways and the VM. This is the preferred way of modern Entra Authentication. RDClientSDK version 3, which is the foundation of the IGEL AVD App 1.3.x where the 3 stands for the SDK version that the App is based on gave IGEL access to Microsoft Authentication Library (MSAL) and RDSAADAUTH.
When IGEL built out the configuration to benefit from RDSAADAUTH, the next step was to build the FIDO2 integration. When a user has Security Key authentication method enabled, and Entra calls for a security pin and to prove presence, we needed to add a code to catch that event and provide what Entra requires.
Watch the demo video.
Stay tune to IGEL for the IGEL AVD App 1.3.2 on IGEL App Portal in the next weeks.
More Choice for Users
IGEL will now be able to provide you a choice to access your AVD or Windows365 workloads using the following authentication methods:
- Username/Password + MFA
- Certificate Based Authentication using smart cards
- Certificate Based Authentication using YubiKey PIV
- FIDO2 authentication
- Imprivata Tap-and–Go
That with the many options of customizing the user interface, everything from a clean Kiosk interface ‘Boot to AVD/Windows365’ providing a very simple access stations, to any type of desktop integration, and customization of the user experience with customized graphics, IGEL address any use case so you are not locking yourself into one single service.
I hope you found this useful!
/Fred
Stay tuned to the upcoming blogs on Tips & Tricks with Fred Brattstig.
Related Blogs
For the smart card authentication, MSAL was the key, as it embeds the smart card authentication.
Read the PIV Blog CAC/PIV smart cards, YubiKey and more. Insider Tips on how IGEL OS use both
I have been playing with specifically YubiKeys, and they come in multiple variants, where I like the YubiKey 5c Nano, in the one user – one device. But for the multi-user – one device I like the YubiKey 5 and 5c better (comes with either USB-A or USB-C interface).
The post FIDO2 Authentication to Azure Virtual Desktop and Windows 365 appeared first on IGEL.
]]>The post Simplify Custom App Creation and Deployment appeared first on IGEL.
]]>The App Creator Portal is your web-based tool for securely packaging and signing third-party Linux apps to run on IGEL OS 12. It replaces the legacy Custom Partitions method, which required manual scripting. Now, packaging and deploying your apps is a visual, low-effort process with built-in security controls—no scripting required. With the newest update, we have introduced Application Recipes directly on the homepage and added detailed build and packaging logs to make the entire app creation process more intuitive and transparent. These improvements remove complexity and provide a better experience for IGEL admins managing custom app delivery in modern endpoint environments.
Updated App Creator Portal homepage. Click to view the demo video.
Application Recipes Now on the Homepage
Getting started is easier than ever. With community-driven App Recipes now featured on the homepage, you can quickly find pre-built templates for popular apps—complete with installation logic, dependency management, and packaging instructions. These Recipes come from the IGEL Community GitHub and drastically cut the time it takes to get your apps ready for deployment. Recipes can also be created by customers themselves, or by IGEL Customer Experience teams upon request.
Application Build and Packaging Logs
We have added full-long visibility for packaging and build processes, giving you the insight needed to:
- Troubleshoot failed builds
- Diagnose missing dependencies or permission errors
- Validate every step of the packaging workflow
- Download logs for internal escalation or vendor support
Whether you are working on your first app or optimizing at scale, these logs empower you to build confidently and efficiently.
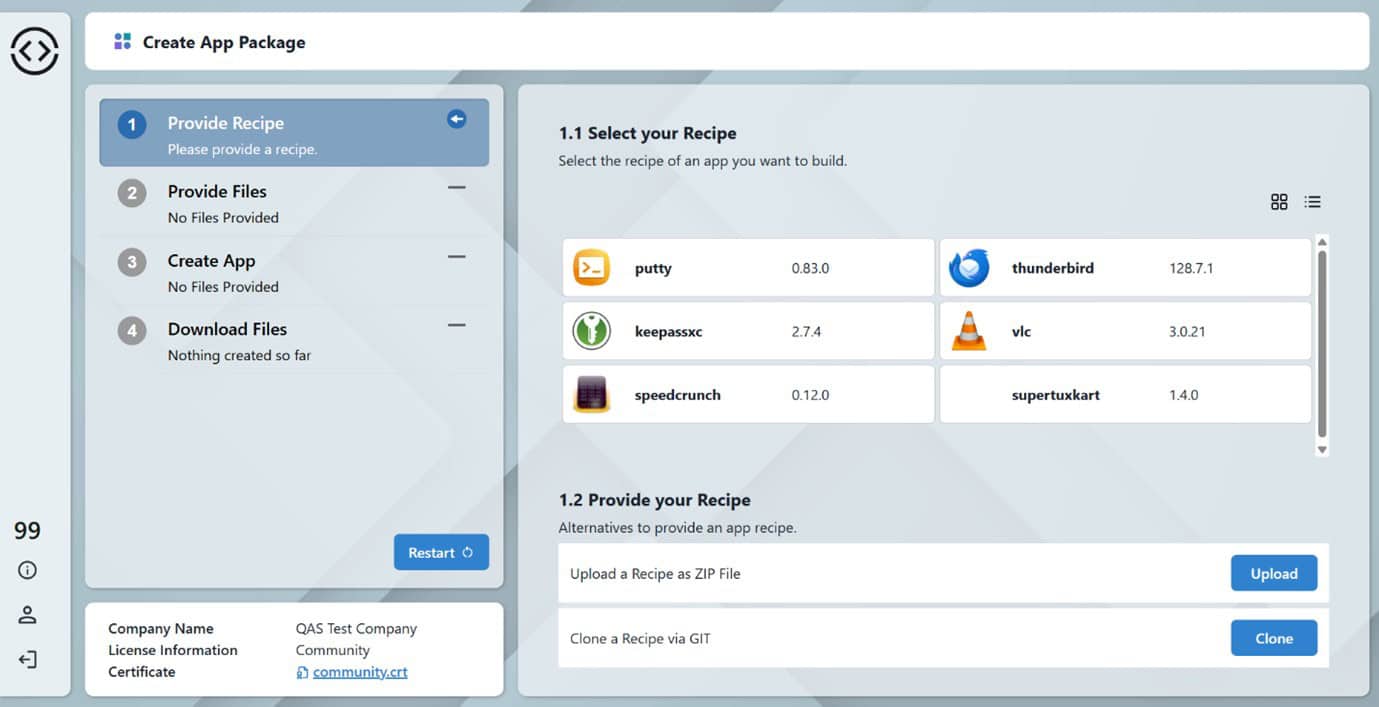
A step by step quick user guide
- Select your Recipe
Now available on the App Creator Portal homepage: select from existing recipes, upload your own, or clone a GitHub URL of your choice. - Get the binary
Download the third-party Linux installer (usually a .deb) from the vendor or upload an existing binary. Note that some recipes may require multiple binaries—or none. - Upload
Use the App Creator Portal to upload the application binary. The ACP analyzes the recipe to identify the required binary or binaries and lists them by name, ensuring you do not miss anything. - Package and Sign
Standard Edition – Digitally sign the application with a community certificate.
Enterprise Edition – Digitally sign the application with your organization’s unique enterprise signing certificate. - Download and Deploy
Use IGEL’s Universal Management Suite (UMS) to deploy the signed app and signing certificate to your endpoints.
Note: Apps created via the App Creator Portal do not appear in the standard IGEL App Portal. These are private packages, signed exclusively for your corporate environment and intended only for your devices. They are also not stored on the ACP—packages are deleted after download in accordance with legal requirements.
One Platform. Full Control.
These enhancements align with IGEL’s Preventative Security Model and lean OS philosophy: deploy only what you need when you need it—without compromising visibility or control. By reducing the manual steps and adding insight into packaging pipelines, we are helping organizations improve operational efficiency, cut deployment time, and strengthen endpoint reliability. This model reduces your attack surface, simplifies compliance, and ensures only trusted software runs on your endpoints. That makes the App Creator Portal essential for securely running apps not yet available in the official IGEL App Portal.
You are in control of your custom apps. IGEL supports the App Creator Portal, the certificate infrastructure, and the packaging service. The IGEL Community maintains Recipes and tooling. You manage the applications themselves.
Together, this shared responsibility model gives you agility, transparency, and security—with none of the manual complexity of traditional Linux app packaging.
Ready to simplify your custom app deployment?
Visit the IGEL App Creator Portal
Watch the Demo Video
Learn more about IGEL App Creator in the Knowledge Base
The post Simplify Custom App Creation and Deployment appeared first on IGEL.
]]>The post Included in the latest release of UMS 12.05.100 IGEL is pleased to announce a new (and much requested) WEB App feature: Corporate Identity Customizations! appeared first on IGEL.
]]>In this blog post I discuss the three easy steps to getting your Corporate Identity onto your IGEL OS11 & OS12 devices, simply Import, Create & Apply!
As we move to feature parity between the Universal Management (UMS) Console and the UMS WEB App, the feature formally named Firmware Customizations available in the UMS Console has now been re-jigged and made available to Admins using the UMS WEB App and is now called Corporate Identity Customizations (CIC) allowing admins to simply and easily apply corporate identity to devices running OS11 & OS12 and later.
CIC is a wizard or intent driven way to simply apply your Corporate Identity to your devices, no longer do you need to create multiple UMS Profiles or type in URL’s, UNC paths, usernames and password to gain access to your Corporate Identity Images and icons. If you still require these features, they are still available to you!
What can Corporate Identity Customizations (CIC) customize?
Screensaver | Wallpaper | Start Menu | Taskbar Background | Bootsplash | Start Button
Looking good!
I know this is a Blog post and not an in depth ‘How to’ guide but this new feature is so cool (and simple) I thought I’d show you how to configure it and get it running.
How do I use CIC?
There are three things you need to enable CIC:
- Import your images
- Create a CIC Object
- Apply to your IGEL OS11 & OS12 devices.
The CIC Configuration is super simple!
Firstly, we’ll upload your images into the UMS WEB App.
Open the UMS WEB App and select Configuration
The default URL is: https://%yourservername%:8443/webapp/#/home
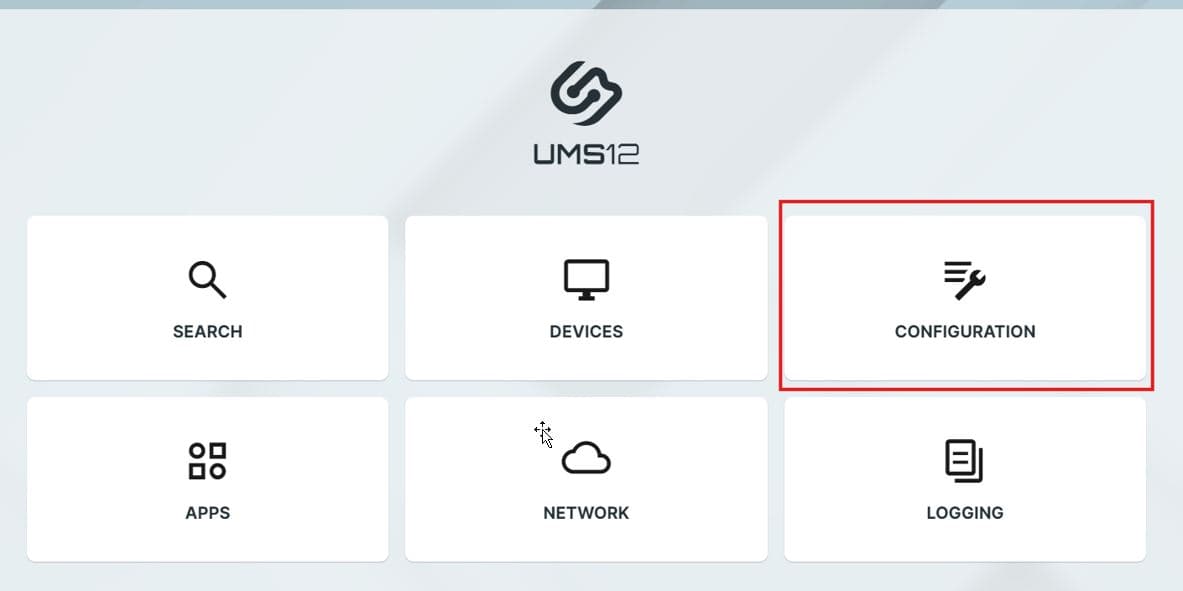
Select Files and import your images
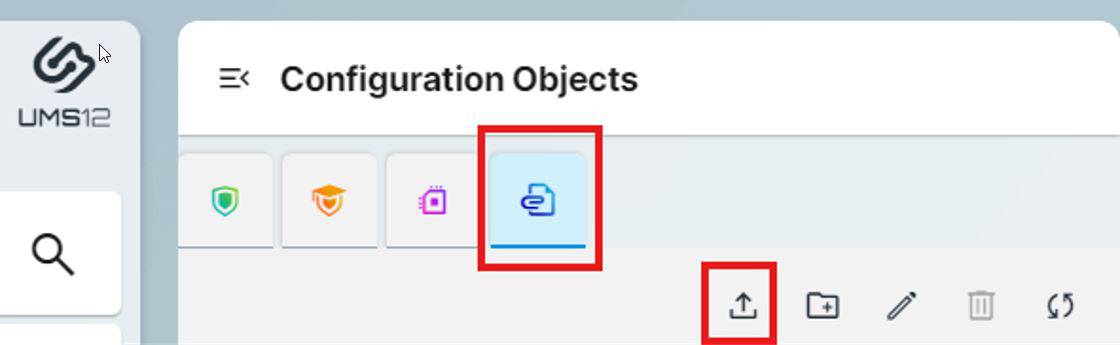
Supported Image Types
CIC supports multiple image file types depending on what you are trying to customize.
The Bootspalsh, Wallpaper, Screensaver and Start Menu supports: .jpg .jpeg .bmp .png .svg .gif and .tiff
The Start Button supports .png and .ico
Taskbar Background supports .ico
Once you have imported your files select Corporate Identity Customizations and click Create New
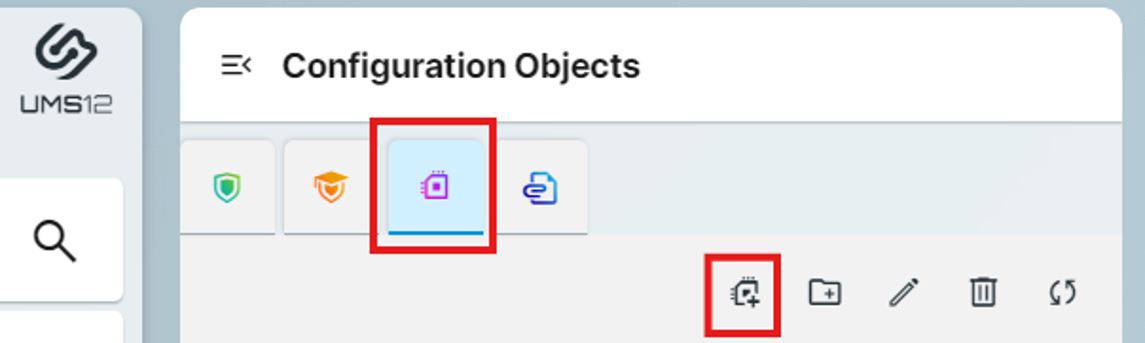
This is where the magic happens, here you can Enter a custom name and select what you would like to customize, depending on your selection the system will only show you what you need to configure. In this example I’ve selected Wallpaper and Bootsplash
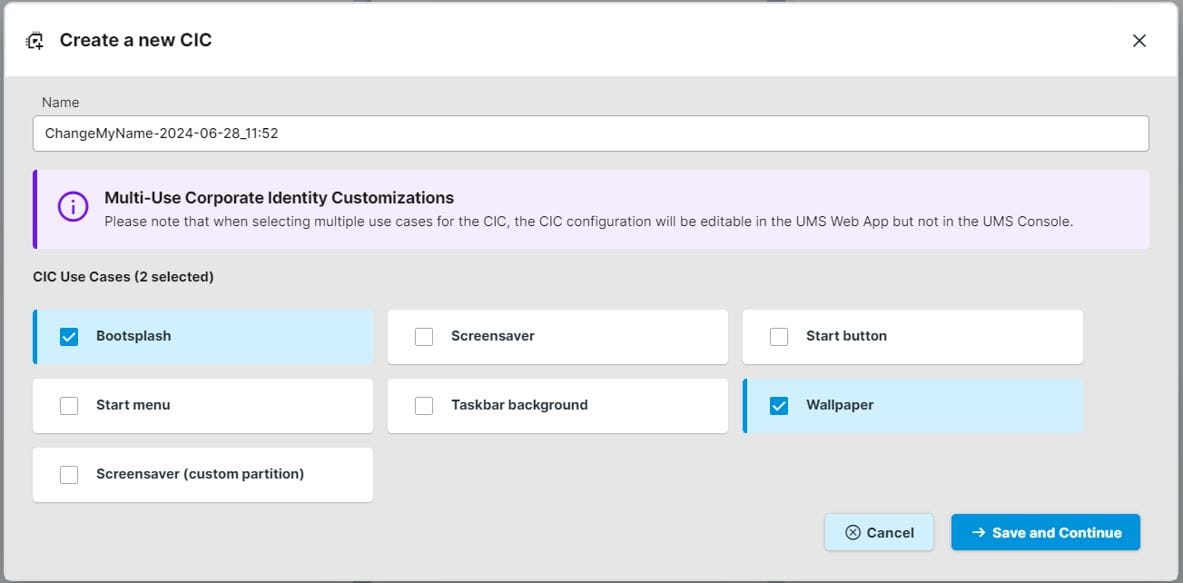
Note: If you make multiple selections, you can only edit this in the UMS WEB App and only view and assign in the UMS Console.
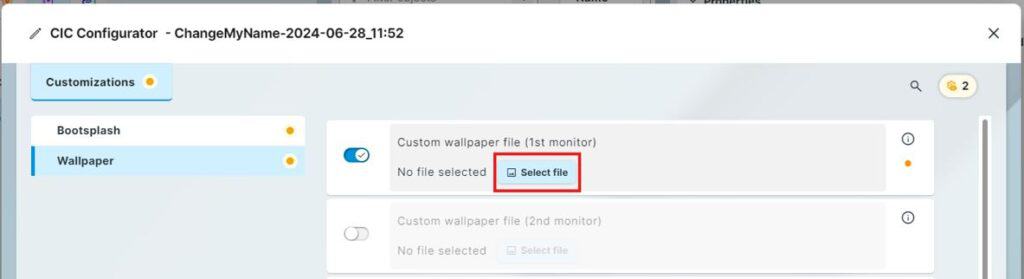
Clicking Save and Continue will take you to the CIC Configurator allowing you to assign the previously uploaded images.
Select the required images and Confirm,
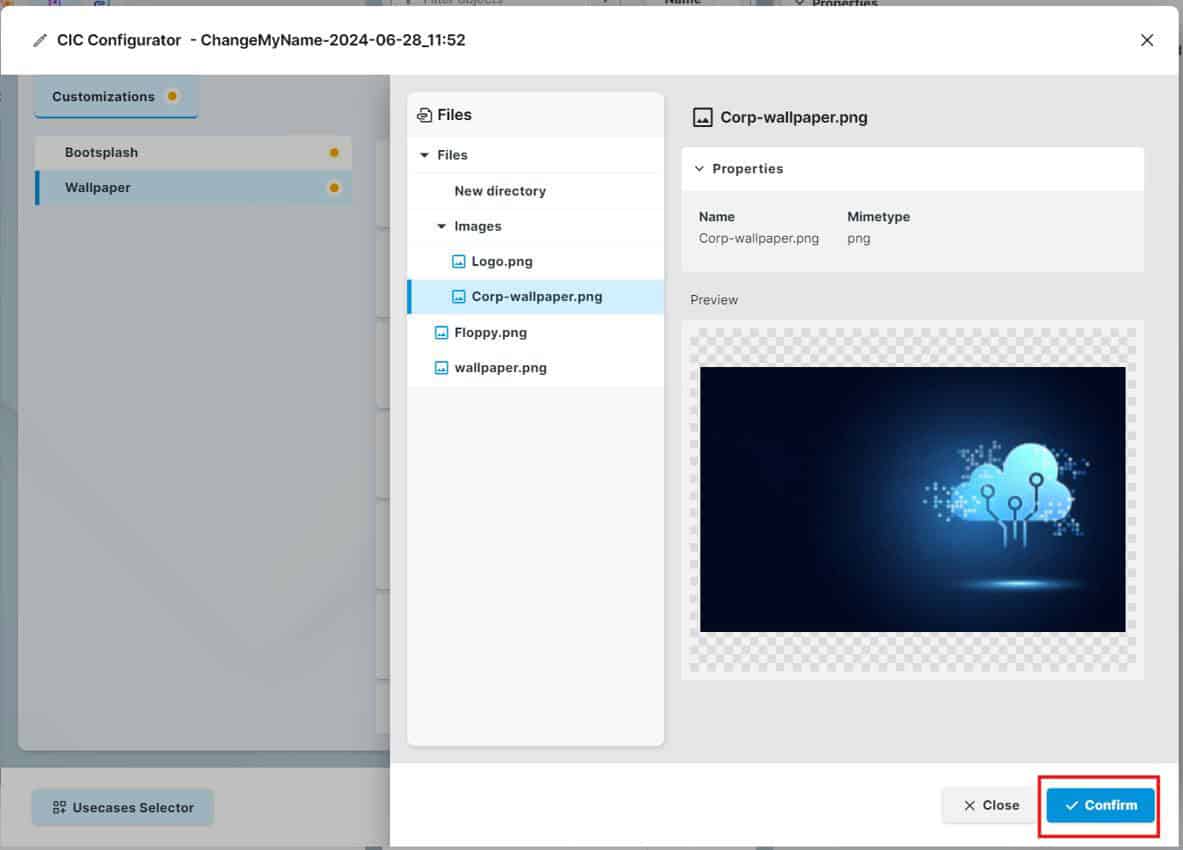
Once all images are selected simply Save and Close
You now have CIC Use Case configured, now we apply it to a device, this is done in a similar way to applying a Profile.
Select the CIC Use Case go to Assigned Devices and assign it to a device or Folder
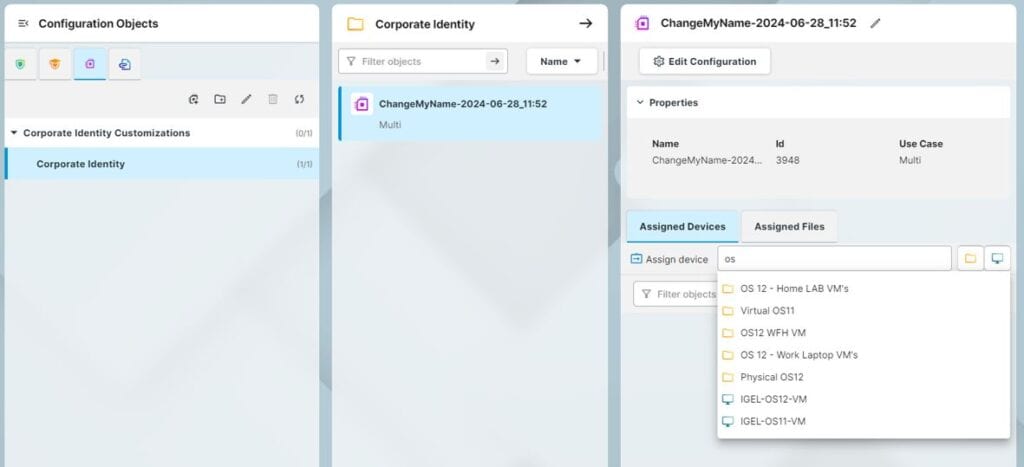
Once assigned, select if you’d like to apply these settings on reboot or immediately.

Done! As you can see applying your Corporate Identity to IGEL OS is a breeze!
If you’d like to read more about the Corporate Identity Customizations and the latest release of UMS 12.05.100, please visit the IGEL knowledgebase: https://kb.igel.com/
Peace out.
/A
The post Included in the latest release of UMS 12.05.100 IGEL is pleased to announce a new (and much requested) WEB App feature: Corporate Identity Customizations! appeared first on IGEL.
]]>The post How Do We Provide A Poor User Experience? appeared first on IGEL.
]]>Innovation in user experience often focuses on achieving success; however, an equally valuable approach is learning how to avoid failure. James Clear brought the Mental Model of Inversion to my intention in a recent 3-2-1 Atomic Habits newsletter, and it led me to read a book about Mental Models.
By asking “How do we fail at this” allows us to focus on avoiding failure as opposed to plotting the journey to reach for a particular goal. This is the Mental Model of Inversion. We can use Inversion in any aspect of life – business, art, career development, personal relationships.
So why don’t we have a go at applying it to End-user experience?
Hardware – Hardware is expensive, and therefore restricts budgets. So end-users will typically be trying to run a modern OS on less-than-ideal hardware. It’ll be stretched, the user will think it is “slow” which will impact productivity and user acceptance.
Operating System – The Operating System needs to be large and complicated. It needs to contain a myriad of notifications and it needs to be complex to navigate.
Local Agents – We’ll make sure we have local agents for VPN, Anti-Virus, n Security Tool that will be managed centrally through YAMS (Yet Another Management Solution), that itself require specialist staff to design, manage and maintain.
Local Applications – We should have the ability for end-users to install their own applications, regardless of where they have come from to be installed on the OS. We shall include a larger number of applications and code in the OS for apps that the users will probably never use. We’ll make sure these all need patching on a regular basis. We’ll deliver some applications from an application management solution(s) centrally. We’ll make sure this process is particularly cumbersome and offer many different options and third-party vendors to help out.
Virtual Applications/DaaS/SaaS – Despite deploying expensive hardware for our large complicated Operating System, what we’ll do is virtualise our large complex OS and deliver apps from a data center or adopt SaaS applications – and use our large complex OS to access them.
Management Tools – For each of these, we’ll ensure that there is an underpinning management solution that needs designing, implementing and its policies maintaining. This will further degrade the user experience in favour of security.
The mental model of inversion posits that in order to achieve success, we should avoid failure, so if we apply this to our question of “How do we provide a poor user experience?” then we need to avoid making these mistakes. I am obviously taking a rather tongue-in-cheek approach with all this – however, the fact does remain, that we’ve tended to always do what we’ve done. When we virtualised our applications or implemented a DaaS solution, or adopted a SaaS approach – we still deployed the same large operating system on the same expensive hardware for end-users to access their apps.
At IGEL, we believe there is a different way. When we’re modernising application delivery – whether through SaaS or virtualisation technologies, what we do on the end-point matters. It’s the entry to our end-user’s daily life at work. It’s the barrier between getting work done, and then getting home to the family.
The experience of work needs to be above all consistent, reliable, and secure. IGEL provide this through what we call our Preventative Security Model.
A small-factor OS, typically 2Gb in size is simple to deploy and manage from a single management console.
As a secure by design operating system, the requirement for n Agents is not there – IGEL Secure OS has never been a victim of a cyber-attack. IGEL OS is read only and there is a chain of trust right from when the device is turned on.
The applications that that user has access to are relevant to them and accessed through a familiar desktop experience – there’s no clutter or unwanted distractions.
Access to virtual applications and desktops is simple. IT can even configure “Boot to X” if the use-case suits. Access to SaaS applications can be done directly from the endpoint, no need to use complex virtualisation resources in deploying Microsoft Edge or Google Chrome. Users can even collaborate using Teams and Zoom in a simple, secure and reliable way.
To put it simply, the user experience is straightforward and does what I believe users want – to get their jobs done.
The post How Do We Provide A Poor User Experience? appeared first on IGEL.
]]>The post Fast Onboarding to Citrix Desktops with IGEL OS – Better together! appeared first on IGEL.
]]>Have you ever been in a situation where you have a user with brand new endpoints out in the field, at home, or elsewhere, and you need to guide them to be able to access your Citrix published Desktops and/or Apps environment? Has there at any time been any problems when onboarding users, making them install the right components and configure their machines in the correct way?
IGEL has been working hard to make onboarding IGEL OS users in the field very easy. With the release of the IGEL Cloud Gateway (ICG), this has already been a reality for many years. Let me explain to you what is needed to make a very smooth onboarding of remote users and actually get them productive within minutes from the first power on of their IGEL OS endpoint.

The goal is to have a brand new IGEL OS endpoint be onboarded by a non-technical user and have that user not have to understand the technology or install any software – just follow a simple guide, fill out the information that the user knows, and get going!
The minimum requirement will be to have the user select the language of the operating system, set what keyboard layout to use, then connect to a wireless network if that is needed, and finally use their email address to tie the IGEL OS endpoint to the secured IGEL OS management infrastructure. This is almost what is needed, but there is actually a technical thing necessary, that is to fulfill the security aspect, so you will need to have a deployment key distributed to the user, to ensure that only authorized users can enroll devices. The deployment key can be issued in either Single Use mode or Mass deployment
– Single Use = you will send a unique key to each user. When the key is used, it can’t be used again
– Mass Deployment = You will send a generic key to your users that can be used over and over again (until you disable that key)
Prerequisites
- IGEL Universal Management Suite – Installation instructions: UMS Installation and Update (igel.com)
- IGEL Cloud Gateway – Installation instrucktions: Installation and Setup (igel.com)
- Brand new IGEL OS endpoint, or an IGEL UD Pocket
As a baseline for this article, I’m currently using a IGEL UMS and IGEL ICG that’s running in my Azure Tenant at the Sweden Central location. I have my Citrix Cloud hosted in European Union (I assume that is located in the Azure WestEU datacenter), and I have my Citrix Desktop delivered from virtual machines in Sweden Central. My IGEL OS endpoint that you see in the video at the end of the article is in my home office on the west coast of Sweden.
Here Is How You Do It, Let’s Get Started!
I will assume that you already have an IGEL Universal Management Suite (UMS) installed together with an externally (from the internet) reachable ICG Cloud Gateway (ICG). The further below steps are what is needed to be done to get the simple onboarding to be a reality.
Add The DNS TXT Record
IGEL UMS and ICG leverage the DNS TXT records to find the correct ICG server to connect to, when you have set up the TXT record in your public DNS, the ICG agent on IGEL OS will be able to resolve the ICG address based on the email address that the user provides, which makes the onboarding. An example could be that the ICG is having a DNS name that is icg.azure.virtualbrat.com while the user email address will be user1@virtualbrat.com, the DNS TXT record resolves @virtualbrat.com part (domain name) of the email address to icg.azure.virtualbrat.com.
If you have a running UMS + ICG environment already, but don’t use the TXT record resolving yet, you simply need to login to your DNS provider and add the TXT record.
Set the TXT ‘Node Name’ to igel-cloud-gateway and value to https://your.icg.fqdn:yourport/usg/endpoint like in the below screenshot:

Set Up Your Default Directory Rules
The whole idea of Fast onboarding is to make the process super easy for a user in the field to gain access to the corporate desktop or published resources, so be it in the cloud or on-premises. The IGEL Universal Management Suite (UMS) has a nice feature called Default Directory rules, giving the opportunity to push distinguished configurations based on the container (or folder) that the IGEL OS endpoint belongs to. IGEL UMS can automatically place an IGEL OS endpoint in a specific container based on certain criteria. This complete ruleset can be extended in very advanced ways, it is all about thinking of what use case you want to fulfill, finding the correct criteria to apply the default directory rules to and the rest will be handled by the IGEL UMS! As a matter of fact, there is a default directory rule that I will use that is very simple –
- Create a new Default Directory Rule
- Select the “IGEL Cloud Gateway” criterion, click Next
- Select “Last Boot via ICG”, click Next
- Select “Choose target directory”, click Next
- Select your appointed target directory in the tree view, and check “Overrides existing directory membership” plus “Apply when device boots”
- Click “Finish”
You have now created a Default Directory Rule that will place ALL IGEL OS endpoints connecting from remote through the IGEL Cloud Gateway to be placed in the selected directory.

Automatic IGEL OS License Deployment Of Brand New IGEL OS Endpoints In The Field
The IGEL UMS can automatically assign licenses to the newly configured IGEL OS endpoint no matter if they are on-premises or out in the field. First off you will of course need to have new IGEL OS licenses available. When this prerequisite is met, you can assign a license deployment rule to the container of your field IGEL OS endpoints.

Create The Set Of Profiles And Assign Them To Your IGEL OS Remote Endpoints
I will do this very simple, and just create one IGEL UMS profile pointing the Citrix Workspace App to my Citrix Cloud Workspace connection address (This could be the Citrix ADC gateway address for on-premise scenarios) and some administrative settings, like setting an NTP time server sync, etc. Plus I will create an IGEL OS Firmware Customization to set a specific wallpaper and some other customizations to modify the user interface on IGEL OS. I will then assign the profile and firmware customization to my container of remote IGEL OS endpoints. The ultimate goal when I configure my IGEL UMS profiles in my scenario will be an auto-launching Citrix Workspace App connecting to my Citrix cloud environment and asking for user credentials, this will be the default behavior every time all my IGEL OS endpoints start’s up to provide a simple and consistent user experience.

That’s it! By following this guide from start to end you will enable simple enrollment of IGEL OS endpoints in the field, leaving your Users to have a very simple onboarding experience. What’s extra nice about this is that the time it took for you to read this article, actually in practice is only a few minutes of configuration to be done when you know what to configure, and how. In the video below you have the end result, showing the user experience of onboarding an IGEL OS 11 endpoint and enabling the user to be productive within minutes.
The post Fast Onboarding to Citrix Desktops with IGEL OS – Better together! appeared first on IGEL.
]]>The post Life on the Edge Season 2 Episode 2: Sustainability appeared first on IGEL.
]]>In episode I talk to Ewen Anderson who is the CIO of PX3.
Ewen starts with an overview of his career in which he has been working in IT for 30 years including some time as an IGEL partner. Four years ago, Ewen and his co-founder Justin Sutton Parker founded PX3 to address a gap they saw in the IT industry around independent science-based information on sustainability and IT.
We then look at what is sustainability and why it has become so important to companies. In fact, most companies annual reports now include sustainability as a strategic business objective.
We look at the pandemic and the impact it is had on the environment and how remote working is a key driver in reducing emissions.
We also investigate how EUC has a major impact on emissions and is responsible for 1% of Global emissions which is on a par with the airline industry which I thought was a shocking statistic.
We discuss the partnership with PX3 the work with one of IGEL’s customers and the environmental and cost savings they made by extending the life of existing devices and also how it saved the resources because 3,120 new devices were not manufactured.
We review how efficient the hyperscale data centres are and how from an environmental perspective it makes sense to move your local workloads from your own “Data Centre” to the cloud. In fact, running those workloads in the cloud can be 7 times more efficient than running locally.
To quote Ewen Green IT can be Great IT!
To conclude we look at companies’ sustainability goals and how Ewen would like to see net zero embedded into all companies as a strategy.
We need to make the consumption of excess electricity and disposable of devices as socially unacceptable as smoking has become.
You can see further information on sustainability and the details of the report at: IGEL Sustainability – Join the Revolution – IGEL
Watch the Life on the Edge Podcast Season 2 Episode 2
UPCOMING ON LIFE ON THE EDGE PODCAST
Stay tuned for our next Life on the Edge podcasts we have lots lined up for 2022!
Subscribe today to IGEL’s channel on YouTube so you don’t miss any of our upcoming episodes. You’ll find the latest and all previous episodes on under the Life on the Edge video podcast playlist. When you subscribe, be sure to enable notifications so you know as soon as a new episode is posted. As always, we aim to deliver the valuable content that will make your Life on the Edge an amazing experience.
For all of those who like to listen to podcasts on the go Life on the Edge is now available as on Spotify, Apple Podcasts and Stitcher.
Thanks for listening and I hope you enjoy the episode.
The post Life on the Edge Season 2 Episode 2: Sustainability appeared first on IGEL.
]]>The post “The Attic” Video Podcast Episode 8: How EUC is well positioned in the hybrid world with Tarkan Maner appeared first on IGEL.
]]>Tarkan began innovating new products and apps at the age of 15 when he and his friends developed the first pre-online version of what would be a combination of Google maps and Trip Advisor today. They sold the map to Istanbul restaurants and hotels to businesses who could put their logo on them, and Tarkan’s entrepreneurial journey began. Born in Ankara, Turkey, he spent part of his youth in Germany due to his dad’s electrical engineering career. Fluent in Turkish, German, French and English, he earned degrees in industrial engineering management, an M.B.A., as well as credentials from Harvard’s advanced management program.
He joined Computer Associates, taking on a number of roles for founder Charles Wang, and then CEO Sanjay Kumar, developing expertise in product management and business development. While representing the company in Asia he met the founders of Wyse. The company at the time was in financial distress. Tarkan moved to Wyse and was instrumental in turning the company around and rebuilding its business. In 2012 Dell completed its acquisition of Wyse, renaming the company Dell Wyse.
Tarkan and IGEL agree that the hybrid environment opens up new opportunities for EUC innovation, and that Nutanix’s approach to closer collaboration with cloud providers is the right strategy for companies wanting to increase market opportunities in the EUC, VDI and cloud space.
Tune in and hear Tarkan talk about where Microsoft and IGEL fit in the hybrid environment of the future. And you’ll never guess what Tarkan did to earn money as a student when he first came to the U.S.!
On Wyse Zero Clients. “Cheaper was not the differentiator. It was complete control and secure computing, that you can control and manage users…and provide ultimate security with no attack surface.”
On Recruiting Talent. “To attract people, you need to give them the autonomy, the environment where they can learn and excel…we treat every employee as a partner and CEO in their own right.”
On Product Management. “Companies sometimes fail because they don’t pay attention to product management. Great engineers cannot achieve great goals unless the right product management is established….Product managers run a business.”
On the Channel. “There is a myth that the channel is dead…it is never going to be dead because we cannot do this alone as vendors…the key differentiator to succeed in the channel is to be authentic…to walk the walk.”
On EUC’s Future. “EUC and EUC as a service in a hybrid world is going to be a bigger opportunity…The pandemic showed us you need to be careful about security control and remote life.”
Watch Episode 8 Here:
Thanks for stopping by The Attic. Some of our upcoming guests include Scott Manchester, Director of Program Management for Windows 365, and ‘godfather’ of the Azure Virtual Desktop (AVD) product.
Exciting news: “The Attic” is now available across all major podcast stations, including Google Podcasts, Spotify, iHeartRadio, Amazon Music and more. New episodes are added to The Attic every month. Don’t miss a single episode! Tune in to The Attic by subscribing to the IGEL YouTube Channel or visit The Attic on PodBean for direct links to all of the ways to listen in on your preferred podcast platform.
The post “The Attic” Video Podcast Episode 8: How EUC is well positioned in the hybrid world with Tarkan Maner appeared first on IGEL.
]]>The post Ransomware Endpoint Threats: How to Fight Back appeared first on IGEL.
]]>Malware is also becoming an increasingly simple endeavor for cybercriminals, even those who are new to the space. “With tools like PowerSploit, PowerWare and Cobalt Strike, even low-skilled attackers can take everyday malware payloads and execute them using sophisticated memory injection techniques to evade detection,” the report said. Similarly, ransomware-as-a-service is helping escalate ransomware attacks. “Would-be criminals no longer need coding skills to carry out devastating attacks against organizations thanks to commoditized offerings available on the dark web and underground forums,” WatchGuard noted.
Combatting these escalated threats at the endpoint requires organizations to look at all the ways threats could succeed and tighten up controls in each element: User activity, the operating system itself, policy and access controls, antivirus software, suspect or abnormal byte sequence detection, a chain of trust, virtualization and cloud-based computing. This defense-in-depth strategy is a multi-layered approach that uses physical, technical and administrative controls to safeguard an organization against ransomware threats.
Be Security Agnostic
We need to extend our thinking beyond just being device agnostic to being entirely security agnostic; recognizing that a hybrid workforce will introduce rogue devices at some point. IT security should focus on practices that reduce risk regardless of where or what device(s) an individual is using at the time. Being security agnostic is the answer to another hybrid workforce trend: Hoteling— which is now gaining steam in 2022 as businesses rethink the expensive office space they probably still have. Just like hotel reservations, workers can reserve office space or just a desk to work on-site as needed. They may or may not bring a device with them, so security protocols must be agnostic, or at least standardized across devices, to support what is becoming a permanently fluid style of working.
Leverage Virtualization and Inherently Secure Operating Systems
Moving Windows to the data center or cloud and using a lean, inherently secure operating system (OS) can enable more secure access to apps and data. For example, moving Windows off the endpoint is the logical strategy as cloud-based applications like Azure Virtual Desktop with Windows 365 and those from VMware and Citrix are now the virtualization standard for end-user computing. This also helps consume less staff time since it streamlines patching and other security updates across the entire endpoint environment; also greatly reducing risk at the endpoint. A user, whether remote or on-site, can open up their device, access data and apps in the cloud and minimize the chances of introducing a threat.
For optimal success, a Linux-based OS built for VDI, DaaS and digital workspaces can be structured as a modular, read-only and tamper-proof firmware base. This base won’t hold any business data for hackers to target as all data is stored in the cloud. A broad array of security-focused features in the OS can be designed to minimize exposure and deter attackers from infiltrating an organization through the endpoint.
Control Access to Endpoint Devices
Giving users what they need to be productive and controlling access to non-relevant apps will further limit the number of cyberattack vectors. IT teams can set policy controls retrievable from Microsoft Active Directory, for example, and also use OS access controls via a selection of integrated PKCS11 libraries that support multifactor authentication. This adds another layer of security to protect the enterprise, even in the event of loss or theft of the endpoint device.
Add Chain-of-Trust Processes
Chain-of-trust adds the next dimension to threat protection—a sequence of cryptographic signature verifications that ensure end-to-end integrity. It extends from the endpoint device to the digital workspace VDI host or cloud. In practice, every time a device boots, chain-of-trust ensures that none of the firmware and software in the startup sequence have been altered. If it detects a failure condition at any step, the end-user is alerted and IT can take appropriate action.
Stay Vigilant
IT teams face another year of security challenges via endpoint devices. By taking a multi-layered approach to endpoint security, businesses can add to their threat defense and simultaneously reduce their overall attack surface. Using a lean, lightweight operating system that is inherently secure by design and moving Windows to the data center or cloud will go a long way toward stepping up security. Adding access controls, chain-of-trust verification and multifactor end-user authentication further reduces threats. These steps also reduce the amount of time and energy expended by IT to secure endpoints in the first place. We know 2022 will bring new attacks. This defense-in-depth strategy can help stop criminals at the endpoint source before attacks occur.
This article was written by Dan O’Farrell, Sr. Director of Product Marketing for IGEL, and first published in Security Boulevard.
The post Ransomware Endpoint Threats: How to Fight Back appeared first on IGEL.
]]>The post Secure, Productive Hybrid Working From Any Endpoint Device With Citrix and IGEL appeared first on IGEL.
]]>82% of company leaders plan to continue offering hybrid work models (Gartner) and 73% of workers want them to continue. Source: Microsoft 2021 Work Trend Index
Virtual Apps, desktops and digital workspaces are core elements to enabling a secure and productive hybrid work model. At IGEL, our focus is to provide a secure and consistently compatible workspace on a familiar graphical user interface making it easier for people to navigate across various devices and work sources from any location.
Citrix Workspace simplifies the job of managing apps, devices, users, and networks. It gives people a unified view of all their documents and applications, and protects company data with industry-leading security, activity monitoring, and analytics. IGEL OS on the endpoint device delivers a compatible and intelligent solution for fast, frictionless, and secure access to Citrix Workspace.
With over two decades of experience and a dedicated team of developers with a steadfast focus on the customer’s needs, IGEL OS is purpose-built for streamlined access to virtual desktops at scale in enterprise environments. It can run on any compatible x86-64 device, and is validated on HP thin clients, LG All-in-One, and Lenovo devices. The unified endpoint management and control solution allows IT admins to deploy and manage hundreds of thousands of IGEL OS endpoints from a single console without a VPN.
As a longstanding Citrix Ready partner, IGEL stays in lockstep with the latest version of Citrix Workspace and Citrix Workspace app. The Citrix Ready team, along with Citrix and IGEL product teams, work closely to plan, integrate, test, and validate the required functionality and criteria to achieve the Endpoint Premium and Cloud levels of partnership.
Eagle-Eyed Visibility – Simplify Management and Increase IT Agility Across Your Organization
Identify the status of and manage each workspace with Citrix and IGEL through unified endpoint management and control. The IGEL Universal Management Suite (UMS) enables IT to easily configure, deploy and update up to 300,000 IGEL OS-powered endpoint devices from a single console. With IGEL Cloud Gateway, you can manage remote “off network” endpoints without requiring a VPN.
Quickly and easily access Citrix Workspace on IGEL OS endpoint devices through an embedded browser for Citrix Workspace app. Regardless of whether the workspace is deployed across a VDI or cloud (on-prem, public cloud, private cloud, or hybrid cloud), the Citrix Cloud platform hosts and administers Citrix services. It helps IT admins extend existing on-premises software deployments by connecting to resources on any cloud or infrastructure. It allows IT to create, deploy, and manage secure digital workspaces with apps and data to end-users from a single console.
Simply Connect, Communicate, and Collaborate
Citrix and IGEL deliver an immersive and high-fidelity unified communications and multimedia user experience within VDI or cloud workspace environments, providing Microsoft Teams and Zoom as a Citrix App client with HDX optimization. IGEL OS supports offloading much of the multimedia processing to the local operating system, while running critical real-time communications components on the device.
IGEL’s ecosystem of over 120 integrated technologies validated as IGEL Ready provides seamless integration with enterprise software and peripherals.
From the Edge to the Cloud — Protect System Integrity
Citrix in the cloud, enterprise-level security, and IGEL’s unique “chain of trust” help boost end-to-end security. Moving Windows from endpoints to the cloud provides immediate security benefits by eliminating the burden of remote Windows patching. As a modular, read-only operating system, IGEL OS presents a much smaller attack surface on the endpoint. It also features a unique chain of trust architecture that validates every step of endpoint execution – from the endpoint device to the cloud –cryptographically.
IGEL’s management console monitors every workspace in real-time and automatically pushes security updates and firmware patches, helping to mitigate fraudulent access and breaches on the endpoint.
The Citrix Zero Trust Approach equips organizations with end-to-end solutions for realizing a zero trust architecture that defends protected surfaces. From Citrix Analytics for Security to Citrix Gateway, organizations are able to implement all mission-critical components of a zero trust architecture—all in one secure digital workspace solution.
As the IT industry still faces extended delivery lead times, optimizing the hardware and resources available is the best solution for your budget, and can support you in achieving your sustainability goals. Citrix and IGEL are focused on supporting the broadest choice of apps, cloud services, and endpoint devices for our customers. Providing a secure and consistently compatible workspace on a familiar graphical user interface makes it easier for people to navigate across various devices from any location.
Watch the video on how Citrix and IGEL offer an unbeatable combination for virtual desktops
Try it out with a free demo of IGEL OS with Citrix Workspace.
The post Secure, Productive Hybrid Working From Any Endpoint Device With Citrix and IGEL appeared first on IGEL.
]]>The post Why Virtual Learning Environments Matter for Student Success appeared first on IGEL.
]]>The pandemic shone a spotlight on the importance for universities and colleges to have a virtual education continuity plan in place. Establishing a consistent hybrid learning space is emerging as the norm rather than the exception to enable students to securely access applications and resources whether on-campus, at their home, or in their dorm room. Equipping faculty and staff with reliable lecturing, tutorial, and administrative capabilities from a remote location play a crucial part in this space.
‘The pandemic shone a spotlight on the importance for universities and colleges to have an education continuity plan in place.’
Empower faculty and students with a collaborative and secure learning space on any device in a hybrid university campus. Sounds easy enough right? Below, I’ll highlight some ways you can streamline and mobilize your university’s learning environments and set yourself up for success.
Hybrid Learning and UYOD
As hybrid learning plans continue to be put in place, more higher learning establishments are relying on “Use Your Own Device” or “UYOD” policies. As universities continue to prioritize hybrid and remote learning options, it is becoming a necessity for students and faculty to have access to their own device. Before the pandemic, when universities were almost 100% in-person, computer labs and campus resources were heavily promoted as services for students. Now that hybrid learning is here, seemingly to stay, universities should continue to utilize UYOD policies. By equipping them, and their personal devices, with the technology (software, platforms, internet, what have you) that they need to success, you can allow your students and staff to continue their work wherever they go.
While these devices and environments may not need to be as strictly secure as they might for some companies, they still need to protect your university’s (as well as student’s) information and data. Consider all of the options before just allowing, or even asking, anyone to endanger their privacy. Make sure whatever environment you choose has the capabilities needed to provide security. These capabilities may include, but not be limited to, profile-based end-user access control, multi-factor authentication, single sign-on, and encryption.
Be Ahead of the Curve
Gone are the days of paper report cards and printed lectures. Prepare your staff for the possibility of full remote learning by offering them the resources they might need. This could be training for your university’s new virtual workspaces, or even lessons on virtual lecture best practices. Whatever it is, make sure your staff is equipped with whatever they might need to continue educating regardless of what unforeseen disruptions may occur. The same goes for your students. As your university continues to utilize hybrid learning, and continues to adopt various forms of a UYOD policy, consider what your student’s need to know, or need in general, to be as successful as possible.
Provide additional resources online as well. Students and faculty will need access to certain programs, secure testing environments, and even virtual labs. Rather than stress about moving everything online, choose services that help provide these needs.
Consider Costs
University needs are expensive – save yours and your student’s money by thinking ahead and working to move your learning environment to the cloud. This can be a stressful process, so you will want to choose technologies and structures that work with you, rather than simply sell to you. Consider options that are sustainable and flexible as well. By reusing existing hardware, as well as having your students and staff use their own devices , you can offset, or at the very lease delay, any investments in new hardware. This can in turn help you save capital expenses and reduce emissions and energy consumption incurred by the production and procurement of new devices.
Streamline solutions for your university by planning ahead, putting policies in place for remote or hybrid learning, and considering the tech needed to make those policies succeed. Highlight productivity and security, and empower your distributed faculty and students to connect, communicate, and collaborate through virtual workspaces.
This article was written by Dan O’Farrell, Sr. Director of Product Marketing for IGEL, and first published in Ed Tech Digest.
The post Why Virtual Learning Environments Matter for Student Success appeared first on IGEL.
]]>