The post From Reactive to Resilient – Inside the Preventative Security Architecture™ appeared first on IGEL.
]]> (PSM) — IGEL’s strategic framework for aligning endpoint, security, and application strategies across the modern enterprise. But strategy without execution is just ambition.
(PSM) — IGEL’s strategic framework for aligning endpoint, security, and application strategies across the modern enterprise. But strategy without execution is just ambition.
That’s where IGEL’s Preventative Security Architecture comes in.
Beyond “Monitor, Detect, Remediate”
Traditional endpoints were designed for general-purpose use—built to accommodate consumers, gamers, and enterprises alike—not to meet the specific demands of secure enterprise environments. Today’s standard endpoint stack is designed to detect, monitor, and remediate threats — assuming that compromise is inevitable.
IGEL turns that assumption on its head.
The Preventative Security Architecture takes a fundamentally different approach — one that prioritizes designing out risk through immutability, minimalism, and policy enforcement at every layer of the endpoint experience.
This isn’t just a better way to secure IGEL OS. It’s a blueprint for customers to establish their own preventative security architecture — one that aligns with their Zero Trust journey, compliance goals, and operational realities.
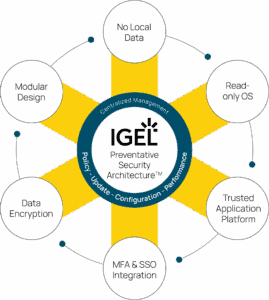
The Core Principles of Preventative Security Architecture
The architecture rests on five pillars:
- Immutable OS State: IGEL OS is locked down at the system level. Unauthorized changes simply can’t persist — or even run.
- Zero Local Data: No data lives on the endpoint. IGEL endpoints are stateless — there’s nothing to exfiltrate or encrypt.
- Secure Boot and Trusted Application Platform: Boot-time chain-of-trust backed by UEFI and TPM ensures only validated components load.
- Minimal Attack Surface: A 2GB core footprint, with optional modules added only as needed — reducing vulnerability density.
- Centralized, Granular Policy Control via UMS: Over 9,000 configurable settings. Enforce consistency without needing endpoint agents.
This is what “secure by design” looks like in practice — not theoretical protections, but tangible barriers that eliminate the opportunity for exploitation.
Your Preventative Security Architecture
This isn’t about locking customers into IGEL’s view of security. It’s about giving them a foundation to build their own preventative strategy — a Preventative Security Architecture that scales with their policies, their risks, and their compliance mandates.
Whether it’s:
- Rolling out a Zero Trust initiative,
- Aligning SOC frameworks such as NIST CSF or ISO 27001,
- Responding to rising ransomware threats
- Transitioning from Windows to a hybrid DaaS model,
IGEL’s architecture supports that journey. Not by dictating it — but by enabling it.
IGEL Ready – The Ecosystem That Powers It
Every strong architecture needs strong integrations. These are provided by the IGEL Ready program.
Through our expansive partner ecosystem, organizations can integrate leading Zero Trust, SSE/SASE, IAM, UEM and compliance solutions into the IGEL experience — natively. Partners like:
- Zscaler, Palo Alto, Netskope (for secure access)
- Microsoft Entra ID, Workspace ONE Access, Imprivata and Okta (for identity and conditional access)
- Island and Microsoft Edge (for browser-based workspaces)
- HP, LG, Lenovo (for secure and sustainable hardware endpoints)
These aren’t bolt-ons. They’re validated. Secure. Orchestrated. And ready to scale.
The Payoff – Simpler, Safer, Resilient
By adopting a preventative security architecture, enterprises can:
- Reduce risk – by removing attack vectors before they can be exploited.
- Reduce cost – by eliminating layers of endpoint agents and streamlining patch cycles.
- Reduce noise – by minimizing alerts and avoiding alert fatigue.
- Improve compliance – through posture-based access and centralized controls.
This is the architecture for the next generation of secure work — and it’s not just IGEL’s. It’s yours.
In Part 3, we’ll tie it all together with the Adaptive Secure Desktop — a dynamic, context-aware workspace delivery model that puts this architecture into motion for every user, device, and role.
— a dynamic, context-aware workspace delivery model that puts this architecture into motion for every user, device, and role.
The post From Reactive to Resilient – Inside the Preventative Security Architecture™ appeared first on IGEL.
]]>The post Rethinking Endpoint Strategy with IGEL appeared first on IGEL.
]]>
This needs to be the era of designing for failsafe.
Instead of relying on detection and remediation, the endpoint must be built to resist compromise — integrated, intelligent, and inherently resilient. IGEL’s Preventative Security Model is the strategic foundation for that shift.
is the strategic foundation for that shift.
This blog series unpacks the full scope of IGEL’s security and workspace transformation strategy in three parts:
- Preventative Security Model
 – IGEL’s unifying framework that aligns application access, security, and hardware strategy.
– IGEL’s unifying framework that aligns application access, security, and hardware strategy. - Preventative Security Architecture
 – The enforcement layer that operationalizes failsafe and becomes your organizations Preventative Security Architecture.
– The enforcement layer that operationalizes failsafe and becomes your organizations Preventative Security Architecture. - Adaptive Secure Desktop
 – A curated on-demand workspace that meets every user, role, and risk profile.
– A curated on-demand workspace that meets every user, role, and risk profile.
The Preventative Security Model
The Preventative Security Model (PSM) is IGEL’s approach to unifying modern endpoint strategies. It’s not an agent. It’s not a policy engine. It’s a philosophy — one that repositions the endpoint from a reactive risk surface to a strategic control layer.
And it’s built for a world that looks very different than it did five years ago.
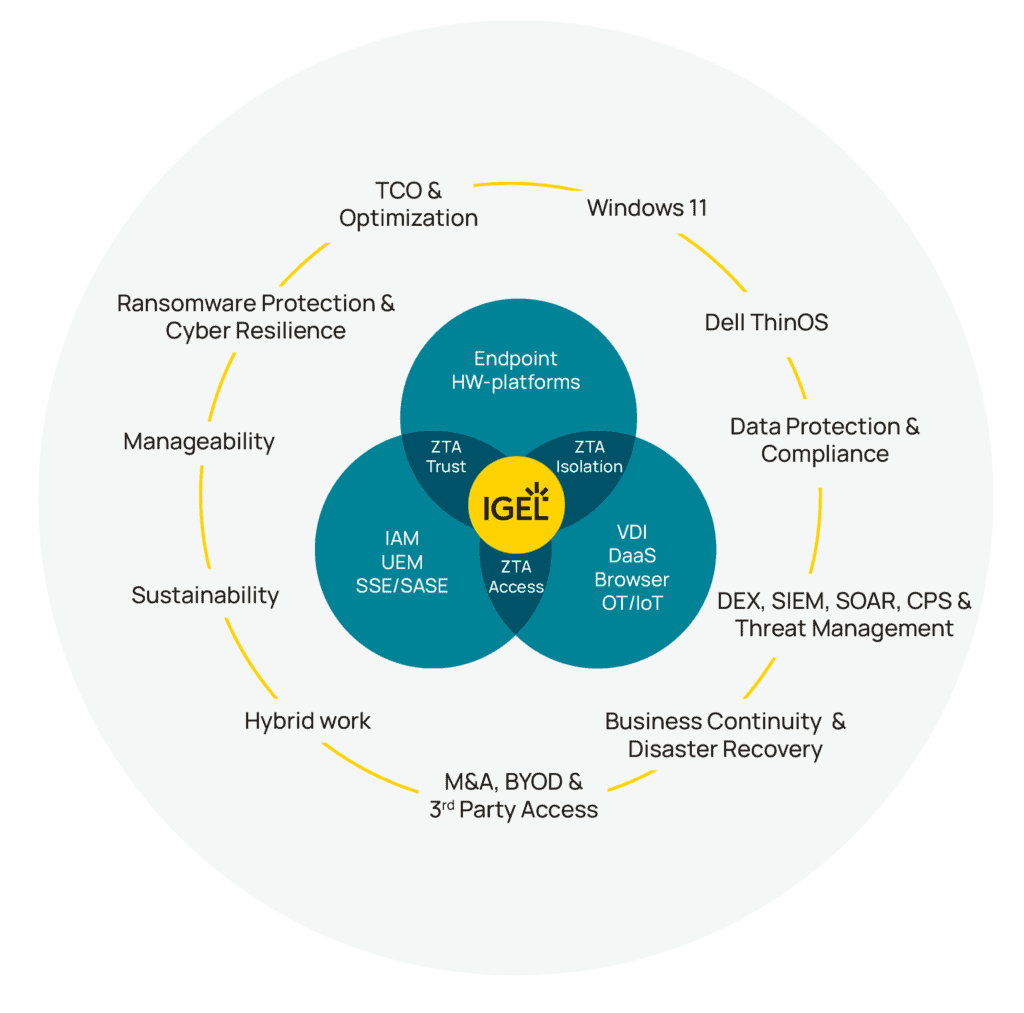
The Endpoint Has Shifted — So Must Our Strategy
Enterprise computing has moved. Workloads have left the endpoint. SaaS, DaaS, and enterprise browsers now carry the weight of productivity. Users roam. Devices are fluid. Data must stay protected — without relying on where it physically lives.
IGEL is the constant in that transition. Both now and next.
The Preventative Security Model provides the framework that connects:
- Application access: Whether delivering full desktops, browser-based tools, native Linux apps, Progressive Web Apps, hybrid SaaS, or even Windows workloads, PSM enables five flexible delivery models — each tailored to user’s needs and risk posture.
- Zero Trust strategy: Zero Trust is a security model that assumes no user or device is inherently trusted and requires continuous verification of identity, context, and access for every interaction within a network. Zero Trust isn’t a product. You don’t buy Zero Trust from a single company. PSM integrates deeply with leading IAM, UEM, SASE, and SaaS vendors to enforce Zero Trust principles from the device outward for secure information access.
- Endpoint sustainability: With endpoints no longer requiring three-to-five-year hardware refreshes due to the simplified workloads, PSM supports long-term device reuse — particularly relevant as organizations scramble to meet Windows 10 EOL activities and deadlines, the EU’s Corporate Sustainability Reporting Directive(CSRD), and Environmental, Social and Governance targets (ESG)
- Operational flexibility: From remote onboarding to rapid reconfiguration during M&A, PSM provides the consistency needed to adapt at speed.
IGEL Ready – The Force Multiplier for the Preventative Security Model
PSM is powered by the IGEL Ready ecosystem — a diverse and growing network of partners across security, identity, peripherals, communications, and hardware. These aren’t just integrations. They’re certified relationships that extend IGEL’s strategy into enterprise environments at scale.
Through IGEL Ready, PSM supports:
- HP, LG, Lenovo, and other leading OEMs to ensure secure, performant hardware compatibility.
- Identity platforms like Microsoft’s EntraID, Omnissa Workspace ONE Access, Imprivata, Okta and Ping for integrated SSO and MFA.
- Security vendors including Zscaler, Palo Alto Networks, and Netskope for Zero Trust and SSE enforcement.
- Peripheral support for clinical, financial, manufacturing, government and retail workflows — including smartcards, speech mics, OT equipment, barcode scanners, document scanners and signature pads to name only a few.
Together, this ecosystem ensures that IGEL endpoints can sit at the centre of a modern, multi-vendor Zero Trust strategy — without friction, without fragility.
Strategic Outcomes Delivered
The Preventative Security Model is not just about securing endpoints. It’s about enabling enterprise transformation. Across industries, PSM is already delivering impact:
- Business Continuity: Fast recovery of compromised traditional endpoints utilizing the in-place hardware
- M&A acceleration: Standardize and secure diverse endpoint fleets across acquired orgs without rip-and-replace.
- Windows 11 readiness: Shift Windows to the cloud, maintain existing hardware, and simplify support.
- Sustainability, CSRD and ESG: Extend endpoint lifespan, reduce e-waste, and align IT with carbon reduction targets.
- Zero Trust execution: Connect policy enforcement from identity to device, in real time, at scale.
Where traditional endpoint stacks are reactive and bloated, PSM is lightweight, adaptive, and policy-aligned — a failsafe foundation for the cloud-first enterprise.
Next up: Preventative Security Architecture, where we explore how IGEL OS eliminates attack vectors and enforces failsafe security by design.
The post Rethinking Endpoint Strategy with IGEL appeared first on IGEL.
]]>The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The new research from Gartner, “Improve Business Continuity Using Desktop as a Service” is striking a similar chord with me. If the enterprise desktop place that we are living in today is so vulnerable, why don’t we just move to the place that is safer?
Stay with me..
The July 2024 CrowdStrike agent failure was a powerful example of the operational exposure most organizations still face. Gartner’s research “Improve Business Continuity Using Desktop as a Service” which references this incident, highlights the strategic role of Desktop as a Service (DaaS) and cloud-hosted virtual desktops in minimizing downtime, and also the use, of what Gartner term a “thin client operating system”. But in doing so, it also highlights a prevailing mindset: **that we are designing the endpoint for failover, rather than designing for failsafe.**
Lets quickly tackle that term – “thin client operating system”. Now I’m looking at this it deserves its own blog, but – The term “thin client” is inextricably linked to the hardware. Search on the term “thin client” and what do you see? A page full of hardware. Wikipedia even states “a simple (low-performance) computer”. Ask an AI engine what the benefits of a thin client are and you’ll find improved security, lower TCO, improved reliability and uptime. Lets take those benefits (often, but not always, delivered by or enabled by the software – IGEL) and lets run them on any device,not just “thin clients”.
At IGEL, we believe in a more targeted, fit for purpose strategy: Yes, have a plan. Yes, embrace VDI, DaaS and browser. But first, ask: what if your endpoint was designed to minimize the risk of failure in the first place?
The Recovery Assumption: The Traditional Endpoint as the Failure Point
Gartner is right to emphasize preparedness. Failures—from agent misfires to ransomware—do happen. But implicit in the recovery model is the assumption that a traditional, built for every eventuality, writeable endpoint is the default (specifically calling out resetting it). And that means layering on security agents, patching, backups, and more.
IGEL, see the endpoint differently: not as something to defend with layers, but something to simplify and harden by design.
Security by Design: The Preventative Security Model
IGEL’s Preventative Security Model shifts endpoint thinking from detection and remediation to proactive prevention and simplification.
- Immutable, Read-Only OS: Stops tampering and malware persistence.
- No Local Data: Removes exfiltration and encryption targets.
- Cryptographically Verified Boot: Ensures the system starts in a known-good state.
- Minimized Attack Surface: Only the necessary components are delivered to the device.
This is not about claiming unbreakable software. IGEL OS is software after all. But it’s software architected with the principles of Zero Trust and attack surface minimization at its core.
Workloads no longer run at the endpoint
With applications increasingly moving away from the endpoint and into the cloud, and Gartner themselves predicting that by 2030 Secure Enterprise Browsers will be a central component of application access strategies, isn’t it time to rethink the endpoint? Isn’t this a point in time to redefine the enterprise endpoint – just like the Enterprise Browser is being redefined?
Business Continuity Begins with Fewer Incidents
Gartner is right: you need a business continuity plan. Virtual desktops and cloud scaling are essential. But we believe true endpoint resilience starts before recovery:
- Design devices that are difficult to compromise
- Limit what runs locally and how it’s accessed
- Deliver workspaces adaptively, based on user role and risk
Case in Point: Dual-Layer Resilience in Action
During the July 2024 CrowdStrike incident, IGEL endpoints remained operational and unaffected. Azure Virtual Desktops could be reset in minutes, as shared by Microsoft’s Scott Manchester—showcasing the agility of modern cloud workspaces. This isn’t applicable to AVD, but all DaaS providers. This combination—IGEL at the endpoint and workloads (DaaS, Enterprise Browser) in the cloud—represents a blueprint for secure, scalable, and resilient desktop delivery.
So (and you’ve been patient) if our destination, in the event of a compromise or failure, is a more resilient infrastructure, powered by a more resilient endpoint operating system and VDI, DaaS, or enterprise browser – rather than go on holiday there, why don’t we just live there?
The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The post How to deploy a VM with IGEL Managed Hypervisor in four simple steps appeared first on IGEL.
]]>If you are interested as to why we are releasing a Hypervisor, I recommend you read this Blog post: https://www.igel.com/blog/igel-managed-hypervisor-secure-your-legacy-workloads/
Let’s get started!
What you will need
- IGEL Universal Management Server (UMS) v 12.07.100 or later
- IGEL OS12.6.1 or later
- IGEL Managed Hypervisor App (releasing in Q2 2025)
- WebDAV server to store and deploy the disk images (I used IIS on my UMS server for this in a LAB environment)
The process is very simple; create a VM on an OS12.6.1 or later endpoint, capture the disk image, create a profile in UMS to deploy the disk image to a target OS12.6.1 or later endpoint, then you can remotely manage OS12 and the VM from UMS.
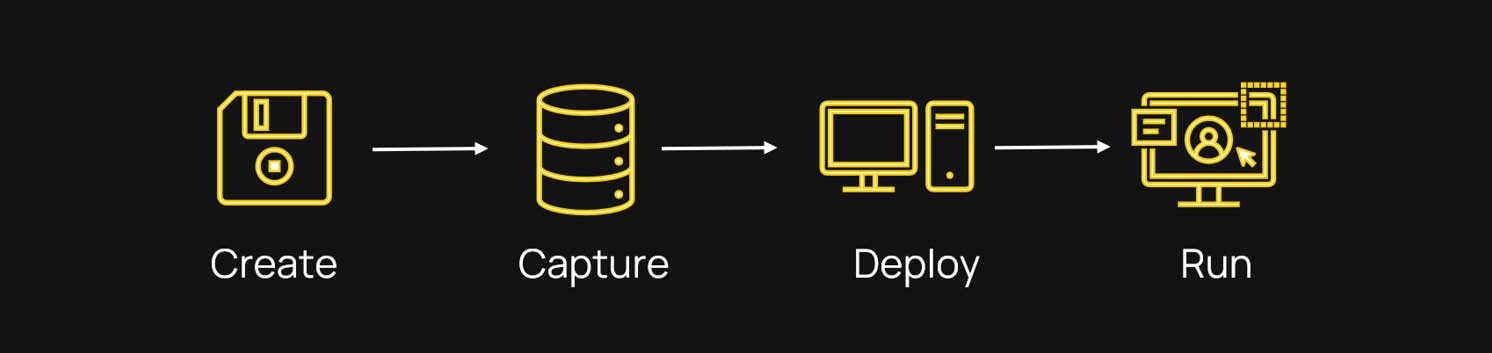
Create
The first step is to create your own ‘Golden Image’. Open the Virtual Machine Manager, click File, New Virtual Machine.
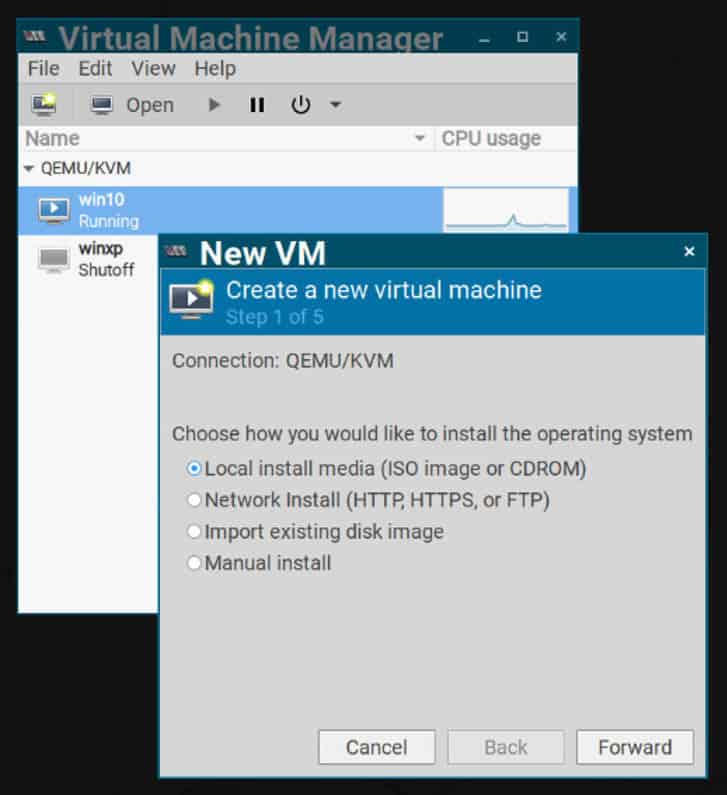
This starts with a wizard which will take you through the steps to create the virtual machine. From selecting the operating system, the storage, CPU and memory to the attached peripherals. In my case I used
a USB storage device with Windows10 and Windows XP ISO files.
Install your selected OS and configure as required.
Capture
Now you have your ‘Golden Image’ we can capture the image and get it ready for deployment. Part of the IGEL Managed Hypervisor app is an export utility called IMH Exporter. To export the VM image to the WebDAV server simply open the IMH Exporter, enter the URL to the WebDAV server and select the VM name you want to export.
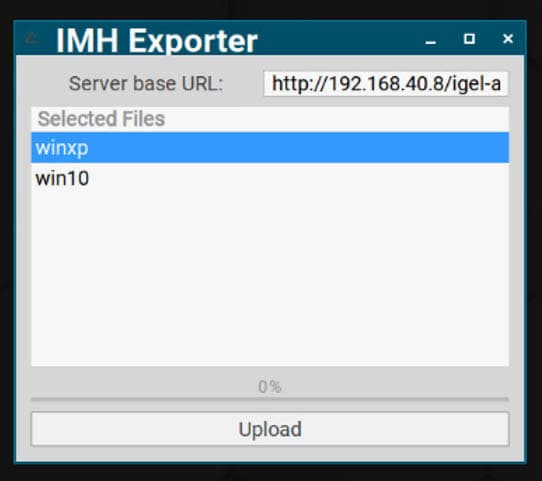
The IMH Exporter will then create two files on the WebDAV server: %vm_name%.img and %vm_name%.xml. The .img file is the disk image (this will be a large file, you will need to consider the storage size and network when exporting) the .xml file is a configuration file detailing all the component the VM needs, such as network, memory, CPU etc.
Deploy
Now we have the Image and the config file we can create a UMS Profile to deploy the Image to a target device (Tip: make sure you don’t send the VM to the device you used to create it on as you will get inconsistent results, if you need to use the same device remove the golden image first)
There are two sections in the IMH App Profile, IGEL Hypervisor Domains and IGEL Hypervisor viewer sessions.
IGEL Hypervisor Domains is used for image deployment. (a domain in this case is the name of the VM). Fill out the details for your VM and the URL to the XML file on the WebDAV server.
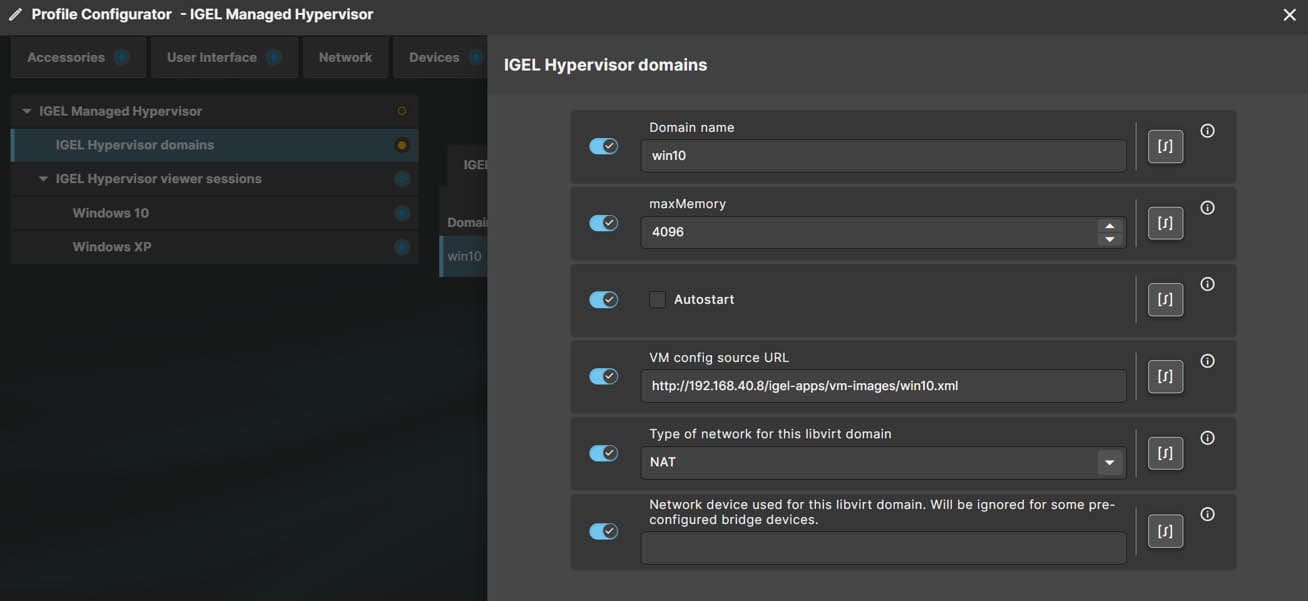
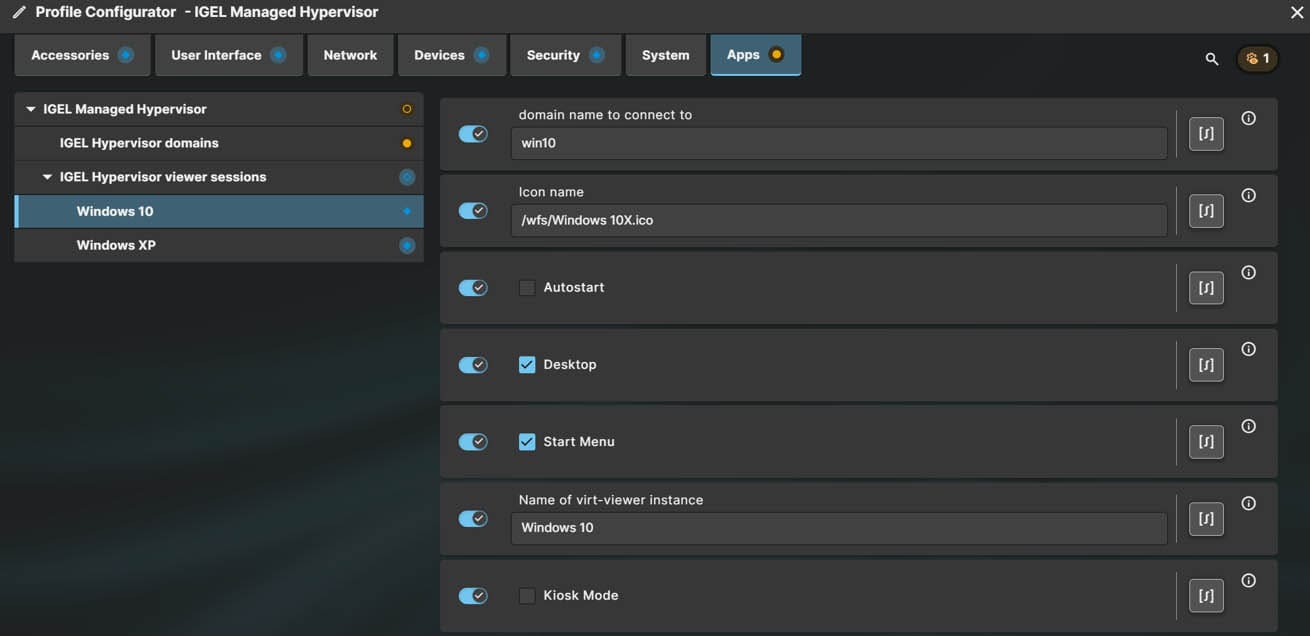
IGEL Hypervisor viewer sessions are used to create an icon which will start a VM viewer on IGEL OS allowing you to see the VM screen, select if you want the VM to auto-start, where the icon will be displayed and if you want the VM to run in kiosk mode.
Apply the profile settings and assign it to a target device.
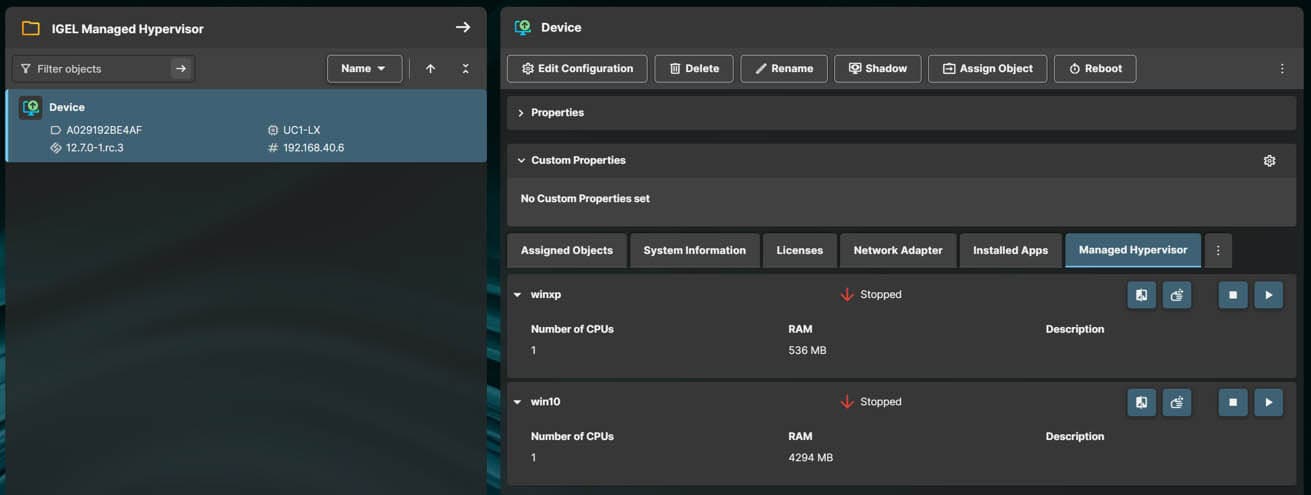
Manage
If all has gone well, you will now have a VM successfully deployed and running. To manage the VM navigate to the OS12 device in UMS, there will be a new TAB called Managed Hypervisor, click this and you will see the VM’s installed on the device and their status. From here you can perform various management tasks, such as, Start, Stop, Delete and re-image.
There we have it, four simple steps to getting your first IGEL Managed Hypervisor VM up and running.
If you would like to learn more about the IGEL Managed Hypervisor I will be running Webinars on Wednesday 14th May 2025 diving further into the details, discussing where IMH fits and running through setting everything up.
Registration links below:
10:00am BST | 10:00am ET | 16:00pm AEST
The post How to deploy a VM with IGEL Managed Hypervisor in four simple steps appeared first on IGEL.
]]>The post A New Era for OT Security and Endpoint Management as IT and OT Converge appeared first on IGEL.
]]>As alarming as this statistic is, it is not surprising as the fact remains that many industries run critical systems on outdated, unsupported versions of Windows XP or Windows 7 on legacy devices.
Join the upcoming webinar to learn how to secure legacy systems and achieve modern efficiency to protect OT systems from ransomware and IT outages with IGEL Managed Hypervisor. During the session, IGEL experts will show you how you can achieve:
Prevent exploitation of OS vulnerabilities
Isolate legacy operating systems in a secure, virtualized environment, preventing unauthorized access and exploitation of OS vulnerabilities
Reduce attack surface on the endpoint
Integrate network segmentation, firewalls, and zero trust architectures to reduce attack surfaces and enforce strict access controls, offering advanced protection against ransomware, malware, and data breaches.
Enhance operational resilience
Centrally manage multiple virtual machines with a secure endpoint virtualization platform designed for preventative security with remote troubleshooting, secure updates, and high availability.
IGEL is tackling the challenges of IT/OT convergence head-on with its latest innovation: IGEL Managed Hypervisor, a virtualization platform designed for preventative security to bridge the gap between legacy operational technology (OT) systems and the security demands of modern hardware, enterprise networks, and the cloud. Announced at the IGEL Now & Next event in Miami in March, the IGEL Managed Hypervisor will be available in IGEL App Portal in May 2025.
Join us on Thursday, May 14, 2025. During this session, you will learn about the advantages of the IGEL Managed Hypervisor and how it positions IGEL as a leader in the emerging convergence of IT and OT security.
Two separate webinars will be held. For the EMEA webinar, register here, and for North America, register here.
Read the Blog Securing Biomedical Devices in Healthcare with IGEL Managed Hypervisor
The post A New Era for OT Security and Endpoint Management as IT and OT Converge appeared first on IGEL.
]]>The post Securing Biomedical Devices in Healthcare with IGEL Managed Hypervisor appeared first on IGEL.
]]>Healthcare organizations face an escalating cybersecurity risk as biomedical teams continue running critical medical devices on older versions of Windows. These legacy systems, often essential for imaging machines, meds dispensing, and diagnostic tools, remain unpatched and vulnerable due to vendor restrictions, operational dependencies, or the excessive costs associated with replacing medical hardware. Not only does this create a security issue, but it also creates an operational issue in finding hardware for these critical controllers to run on as new hardware – think TPM2 chips – does not support the outdated version of Windows.
According to a Help Net Security report, 70 percent of medical devices in hospitals run outdated operating systems, making them prime targets for cyberattacks. Meanwhile, research from Claroty’s Team82 found that 63 percent of known vulnerabilities tracked by CISA exist within healthcare networks, due to aging infrastructure and the inability to update Windows-based systems.
The need for a secure, efficient, and cost-effective way to continue operating these devices, using new endpoint hardware, without exposing hospitals to cybersecurity threats is more urgent than ever. This is where IGEL Managed Hypervisor comes in.
How IGEL Managed Hypervisor Strengthens Security for Biomedical Devices
Isolating Vulnerable Windows Instances
IGEL Managed Hypervisor allows biomedical teams to run legacy Windows-based applications securely within a controlled virtualized environment. Instead of running outdated Windows versions directly on endpoint hardware, the IGEL OS acts as a separation layer between the hardware and the Windows instance running inside a managed hypervisor. This approach eliminates persistent malware risk by ensuring a fresh Windows session at every reboot, and provides a read-only, tamper-proof operating environment.
Extending Medical Device Lifecycles with IGEL Managed Hypervisor
Many medical devices rely on outdated versions of Windows, which are incompatible with modern hardware. This forces healthcare organizations to source and maintain aging systems—an expensive and unsustainable approach. IGEL Managed Hypervisor solves this by decoupling software from hardware, enabling legacy Windows-based medical applications to run securely on modern devices. This eliminates the need for outdated equipment, reduces maintenance costs, and enhances security, allowing hospitals to extend the lifecycle of critical medical devices without compromise.
Meeting Compliance and Zero Trust Security Requirements
Regulatory bodies like HIPAA, FDA, and NIST emphasize cybersecurity in medical technology, yet legacy Windows systems often lack built-in Zero Trust protections. IGEL Managed Hypervisor, built on the Preventative Security Model, provides a secure-by-design endpoint foundation that integrates with leading Zero Trust Architecture (ZTA) solutions. It adds an additional firewalling layer to prevent malicious activity and works alongside network segmentation tools to contain threats. By enabling IT to create an immutable, rollback-ready Windows environment, IGEL ensures medical systems can be restarted in a known-good state—much like a non-persistent VDI desktop—supporting the uptime and availability critical for patient care.
Seamless Integration with Existing IT Infrastructure
Healthcare IT teams are stretched thin, managing both modern and legacy environments. IGEL Managed Hypervisor is managed from the IGEL UMS simplifying endpoint management by allowing centralized policy enforcement across all devices, enabling remote updates and patches without disrupting workflows, and supporting Browsers, SaaS, DaaS and VDI integrations
Why IGEL is the Right Fit for Healthcare Biomedical Teams
Hospitals need a pragmatic security approach that works within existing constraints. IGEL Managed Hypervisor offers a security-first design that minimizes attack surfaces by isolating legacy Windows environments, removes the issue of maintaining old hardware, reduces hardware refresh cycles and extends device lifespans, and works across distributed healthcare environments with zero-trust-ready architecture.
In a time where cyber threats to medical infrastructure are escalating, IGEL provides a proven, scalable, and secure way to modernize healthcare IT without disruption.
Want to Learn More?
If your biomedical team is managing legacy Windows devices, IGEL Managed Hypervisor can help secure your infrastructure without sacrificing operational efficiency. Contact us today to discuss how we can help your healthcare organization stay protected.
Learn more about IGEL Managed Hypervisor
View the Demo Video
The post Securing Biomedical Devices in Healthcare with IGEL Managed Hypervisor appeared first on IGEL.
]]>The post FIDO2 Authentication to Azure Virtual Desktop and Windows 365 appeared first on IGEL.
]]>For my fellow tech enthusiasts, this blog offers my insights into this solution.
FIDO2 authentication is frequently asked for and can be seen as an evolution or replacement for the ‘legacy’ smart card secure authentication. FIDO2 improves authentication speeds, and the security sticks are in a user-friendly format.
Connecting to AVD and W365
Connecting to AVD and W365 is a three-step process (simplified), first you authenticate to EntraID web pages, then you authenticate to the Azure Gateways, and finally you Authenticate to the VM you want to remote. With the previous versions of the Microsoft RDClientSDK, the three steps were only possible using credential stuffing – capturing the username and password from the user, and then in a secure manner provide the captured credentials in the connection process.
A Game Changer
To enable FIDO2 authentication, IGEL implemented support for RDSAADAUTH enabled in the RDClientSDK. Simplified, it gives the user the possibility to Authenticate to EntraID, to retrieve a token, RDSAADAUTH then takes this token and presents it to the Azure Gateways and the VM. This is the preferred way of modern Entra Authentication. RDClientSDK version 3, which is the foundation of the IGEL AVD App 1.3.x where the 3 stands for the SDK version that the App is based on gave IGEL access to Microsoft Authentication Library (MSAL) and RDSAADAUTH.
When IGEL built out the configuration to benefit from RDSAADAUTH, the next step was to build the FIDO2 integration. When a user has Security Key authentication method enabled, and Entra calls for a security pin and to prove presence, we needed to add a code to catch that event and provide what Entra requires.
Watch the demo video.
Stay tune to IGEL for the IGEL AVD App 1.3.2 on IGEL App Portal in the next weeks.
More Choice for Users
IGEL will now be able to provide you a choice to access your AVD or Windows365 workloads using the following authentication methods:
- Username/Password + MFA
- Certificate Based Authentication using smart cards
- Certificate Based Authentication using YubiKey PIV
- FIDO2 authentication
- Imprivata Tap-and–Go
That with the many options of customizing the user interface, everything from a clean Kiosk interface ‘Boot to AVD/Windows365’ providing a very simple access stations, to any type of desktop integration, and customization of the user experience with customized graphics, IGEL address any use case so you are not locking yourself into one single service.
I hope you found this useful!
/Fred
Stay tuned to the upcoming blogs on Tips & Tricks with Fred Brattstig.
Related Blogs
For the smart card authentication, MSAL was the key, as it embeds the smart card authentication.
Read the PIV Blog CAC/PIV smart cards, YubiKey and more. Insider Tips on how IGEL OS use both
I have been playing with specifically YubiKeys, and they come in multiple variants, where I like the YubiKey 5c Nano, in the one user – one device. But for the multi-user – one device I like the YubiKey 5 and 5c better (comes with either USB-A or USB-C interface).
The post FIDO2 Authentication to Azure Virtual Desktop and Windows 365 appeared first on IGEL.
]]>The post Enhance EHR with AWS Isolated Recovery Environment and IGEL appeared first on IGEL.
]]>IGEL Preventative Security Model & AWS Isolated Recovery Environment
The IGEL Preventative Security Model and AWS Isolated Recovery Environment combined form a multi-layered defense strategy that helps provide security from endpoint to cloud recovery. IGEL PSM ensures that endpoints remain a trusted, compliant, and non-persistent access point for AWS-hosted EHR environments, even in the face of sophisticated cyber threats.
- Read-Only OS: IGEL OS runs in a locked-down state, preventing malware installation, unauthorized software execution, and persistent threats.
- No Local Data Storage: All data remains centralized within AWS IRE, eliminating the risk of endpoint data exposure due to device loss, theft, or compromise.
- Trusted Boot Process: IGEL’s chain-of-trust architecture verifies the integrity of every OS component at boot time, ensuring the endpoint has not been tampered with.
- Secure Application Execution: Only pre-approved applications and virtual workspace connections (ex: Amazon WorkSpaces, AppStream 2.0, or Microsoft Edge) are allowed, reducing potential attack vectors from rogue applications.
- Centralized Endpoint Management: IGEL Universal Management Suite (UMS) provides real-time policy enforcement, configuration lockdowns, and automated endpoint recovery, ensuring rapid response to security threats or environmental changes.
Securing Critical Workloads in the Cloud with AWS Isolated Recovery Environment
AWS IRE is a highly secure, logically separated recovery architecture designed to protect EHR workloads from ransomware, data corruption, and unauthorized access.
- Logically Separated Data Storage: EHR workloads are stored in logically separated AWS accounts, ensuring isolation from the primary production environment.
- Immutable Snapshots & Encryption: AWS Backup, AWS Snapshot Manager, and S3 Object Lock provide protected copies of EHR environments, preventing unauthorized modifications.
- Automated Recovery Orchestration: AWS CloudFormation and AWS Lambda enable rapid, automated environment restoration with minimal manual intervention, reducing downtime during recovery.
- Advanced Threat Detection & Monitoring: AWS GuardDuty, Security Hub, and IAM policies enforce continuous threat detection, anomaly monitoring, and strict access controls, ensuring only authorized recovery actions occur.
- Zero Trust Access Control: AWS IRE leverages IAM policies, AWS Organizations, and AWS Control Tower to segment access permissions, restrict lateral movement, and enforce least-privilege principles.
By combining IGEL’s endpoint security with AWS’s isolated, fully automated recovery environment, EHR customers achieve seamless, policy-driven access to their recovery systems while maintaining compliance with HIPAA, HITRUST, and NIST cybersecurity standards.
IGEL and AWS IRE Strengthen Electronic Healthcare Record Security
- AWS Solution with Secure Endpoints: IGEL OS is part of a recovery architecture, ensuring secure, policy-driven endpoint access to EHR environments.
- End-to-End Cyber Resilience: AWS IRE isolates EHR workloads, and IGEL ensures trusted access with a read-only, stateless OS.
- Zero Trust and Compliance-Ready: Supports organization in meeting HIPAA, HITRUST, and NIST standards, securing healthcare operations from endpoint to cloud recovery.
- Seamless Recovery Access: IGEL endpoints ensure clinicians and staff can instantly access AWS-hosted EHR environments in a disaster scenario.
IGEL and AWS are delivering a fully validated, end-to-end IRE solution for EHR customers. By combining IGEL’s secure, policy-enforced endpoints with AWS’s isolated recovery architecture, healthcare organizations can achieve enhanced cyber resilience ensures , secure patient data, and maintain uninterrupted operations.
Key Takeaways
- Validated AWS IRE Solution: IGEL endpoints ensure compliant, trusted access to recovered EHR environments.
- Seamless Disaster Recovery: Rapid failover with pre-configured, policy-enforced IGEL devices.
- Zero Trust Security: Endpoint-to-cloud protection ensures resiliency against ransomware and cyberattacks.
Would you like to explore how IGEL OS and AWS Isolated Recovery Environment can support your EHR security strategy?
Contact us today to learn more.
The post Enhance EHR with AWS Isolated Recovery Environment and IGEL appeared first on IGEL.
]]>The post Expand App Access on IGEL OS with Progressive Web Apps appeared first on IGEL.
]]>Why Progressive Web Apps Matter
PWAs bridge the gap between web and native applications, delivering an app-like experience while remaining lightweight and browser-based. They bring several benefits, including:
- Offline Support – PWAs can function even when connectivity is limited.
- Push Notifications & Background Sync – Improves engagement and real-time updates.
- Cross-Platform Compatibility – Works seamlessly across devices and operating systems.
- Centralized Deployment – IGEL administrators can deploy PWAs to IGEL OS desktops, allowing users to access them just like any other application, with a seamless launch experience.
For IGEL OS users, this means another secure and efficient way to access enterprise applications while maintaining IT control and minimizing overhead.
Expanding Application Delivery: PWAs & Beyond
PWAs complement the existing application delivery methods IGEL already provides:
- Virtual Apps & Desktops via DaaS & VDI – With Omnissa, Microsoft AVD/Windows 365, and Citrix, organizations can virtualize applications securely without endpoint dependencies.
- Enterprise Browsers – IGEL OS natively supports Edge, Firefox, and Island, providing secure, direct access to web applications.
- IGEL Managed Hypervisor (IMH) – When Windows is required at the endpoint, IMH delivers an immutable, rollback-ready Windows instance for critical environments.
- Additional PWAs – expanding the number of PWA’s available from the IGEL App Portal now including Microsoft Office apps like Teams, Outlook, Word, Excel, PowerPoint, and Copilot, and Google Gmail, centrally managed and deployed for seamless access.
A Secure Foundation with the Preventative Security Model
Like all IGEL innovations, PWA support is built on the foundation of the Preventative Security Model (PSM), ensuring:
- A secure-by-design approach that eliminates attack vectors rather than reacting to them.
- Integration with IGEL’s security ecosystem, including authentication, encryption, and Zero Trust principles.
- Simplified management and control—centralizing security and access policies while reducing endpoint complexity.
A Unified Approach to Secure Application Access
With expanded PWA support, IGEL OS offers an even broader application access strategy that meets organizations where they are—whether through DaaS, VDI, enterprise browsers, hypervisor-based Windows, or IGEL native apps. By enabling centralized deployment of PWAs, IGEL ensures users experience them just like traditional applications, while IT maintains full control over security, configuration, and access policies.
Ready to Leverage PWAs on IGEL OS?
If your organization is looking for a modern, secure, and cost-effective way to deploy applications, PWAs on IGEL OS are an excellent option. Combined with our robust ecosystem of application delivery methods, IGEL provides the ultimate flexibility for secure enterprise access.
Would you like to explore how IGEL OS can support your digital workspace strategy?
View the IGEL PWA demo video
Contact us today to learn more.
View the Microsoft Teams PWA on IGEL App Portal
The post Expand App Access on IGEL OS with Progressive Web Apps appeared first on IGEL.
]]>The post Enhancing Zero Trust Authentication with IGEL and 90Meter for Federal and Enterprise Security appeared first on IGEL.
]]>Security and compliance are critical for federal agencies and enterprises operating in highly regulated environments. As cyber threats evolve, organizations must adopt Zero Trust authentication strategies to safeguard sensitive data and prevent unauthorized access.
IGEL, a leader in endpoint security and management, has expanded its partnership with 90Meter, a leading USA-based smartcard software vendor, to enhance support for Zero Trust authentication and endpoint security within IGEL OS 12. This collaboration extends native support for the 90Meter PKCS#11 smart card library to now include NIPRNet, while also updating existing SIPRNet PKCS#11 support. By integrating 90Meter’s PKCS#11 smartcard library, this collaboration delivers seamless and secure identity verification for Virtual Desktop Infrastructure (VDI) deployments and browser-based access.
The IGEL + 90Meter Solution: A Zero Trust Approach
The IGEL and 90Meter integration enables strong identity and credential access management (ICAM) by offering:
- Seamless Smartcard Authentication – Secure authentication for virtual desktops and applications using 90Meter’s PKCS#11 smartcard library.
- Zero Trust Endpoint Security – IGEL OS 12 operates under a Preventative Security Model (PSM), ensuring only verified and policy-controlled devices gain access.
- Regulatory Compliance – Meets DoD, NIST, and FIPS security standards for federal agencies and enterprises.
- Cross-Platform Compatibility – Supports Citrix, Omnissa Horizon, and Azure Virtual Desktop (AVD) for multi-cloud and hybrid environments.
- Browser-Based Access – Enables secure authentication via Microsoft Edge, Chromium, and Firefox, ensuring flexible and user-friendly access.
Preventative Security Model: Fortifying Endpoints
IGEL OS 12 is designed with a Preventative Security Model (PSM) that enforces strict security controls, reducing the risk of cyber threats. Key security features include:
- Read-Only OS – Prevents malware installation and unauthorized modifications.
- No Local Data Storage – Ensures authentication credentials and sensitive information remain protected.
- Trusted Boot & Chain of Trust – Validates OS integrity at startup to prevent unauthorized changes.
- Centralized Security Management – IGEL’s Universal Management Suite (UMS) enforces security policies for controlled access to 90Meter-enabled VDI environments.
Key Benefits for Federal and Enterprise Environments
- Enhanced Security & Compliance
- Prevents unauthorized access with Zero Trust smartcard authentication.
- Supports government-mandated security standards, including DoD, NIST, and FIPS.
- Eliminates endpoint attack vectors with IGEL’s secure OS model.
- Streamlined Authentication & User Experience
- Simplifies smartcard-based authentication for virtual and browser-based applications.
- Reduces authentication friction while maintaining robust security controls.
- Provides a seamless user experience with flexible access options.
- Scalability & Future-Proofing
- Adapts to cloud, hybrid, and on-prem authentication models.
- Supports multi-site authentication policies for enterprise-wide security.
- Future-ready for evolving cybersecurity regulations.
Achieve Zero Trust Security with IGEL and 90Meter
The IGEL + 90Meter solution empowers federal agencies and enterprises to achieve secure, scalable, and compliant authentication. By integrating IGEL OS 12 with 90Meter’s PKCS#11 Library, organizations can strengthen Zero Trust security while ensuring seamless user access across virtual and browser-based platforms.
For organizations seeking to enhance endpoint security, IGEL and 90Meter provide a proven, policy-driven authentication framework tailored to today’s evolving cybersecurity landscape.
Learn more about IGEL and 90Meter’s Zero Trust authentication solution today.
Contact us to learn more usfedsales@igel.com
The post Enhancing Zero Trust Authentication with IGEL and 90Meter for Federal and Enterprise Security appeared first on IGEL.
]]>