The post One Workspace, Every User – The Power of the Adaptive Secure Desktop™ appeared first on IGEL.
]]>- The Preventative Security Model
 – IGEL’s strategic framework aligning endpoint, security, and operational strategies.
– IGEL’s strategic framework aligning endpoint, security, and operational strategies. - The Preventative Security Architecture
 – The hardened design foundation that removes attack vectors by default.
– The hardened design foundation that removes attack vectors by default.
Now, in Part 3, we turn to how these ideas come alive at the edge — with the Adaptive Secure Desktop .
.
This isn’t a desktop in the traditional sense. It’s a role-based workspace delivery model — one that flexes to meet the needs of every user, while enforcing the principles of failsafe security.
It’s where strategy and execution meet the end user.
A Workspace That Adapts to Context
Modern work is dynamic. Users aren’t always in the office. Roles change. Risk levels shift. Yet most organizations still deliver the same desktop to everyone — and secure it the same way, too.
The Adaptive Secure Desktop flips that.
Instead of a one-size-fits-all OS, it delivers a context-aware workspace.
- Clinician in a hospital? Instant badge-tap access to virtual desktops with no local data.
- Retail associate at a kiosk? Locked-down browser mode tied to a single SaaS platform.
- Remote knowledge worker? Full desktop experience via DaaS, with security layered in via SASE and IAM controls.
- Contractor or M&A user? Temporary, policy-bound workspace spun up with limited permissions and app access.
The workspace changes based on who the user is, where they are, what device they’re using, and what risk profile applies — all orchestrated through IGEL OS and UMS.
Enforced by Architecture, Not Just Policy
What makes the Adaptive Secure Desktop different from traditional workspace delivery?
It’s not just a VDI session. It’s not just app publishing. It’s a security-first execution model, enforced at the OS level:
- Read-only system image: No tampering, no malware persistence.
- No local data: All access is to virtual or cloud-hosted resources.
- Hardware-rooted trust: Every boot verified, every component signed.
- USB controls and isolation: Based on role and context — not static policies.
- Dynamic access methods: Delivered based on persona — DaaS, SaaS, local apps, browsers.
And all of this is centrally managed through IGEL Universal Management Suite, giving IT full control without needing to touch the endpoint directly.
Zero Trust, Realized at the Edge
The Adaptive Secure Desktop is where IGEL’s Preventative Security Model meets Zero Trust execution.
- Every session is authenticated
- Every endpoint is validated
- Every action is governed by context
It allows customers to enforce their own Zero Trust policies — not just by integrating with IAM and SASE platforms, but by ensuring that every endpoint behaves as if it can’t be trusted until proven otherwise.
Consistency Without Complexity
From a single platform, organizations can:
- Support frontline, knowledge, and temporary users with precision.
- Deliver fast, reliable access to virtual or cloud apps — without compromising security.
- Scale globally with consistent policies, minimal overhead, and no reliance on constant patching or imaging.
It’s a future-proof foundation — built not just for what users need today, but for how work will evolve next.
The Takeaway
The Adaptive Secure Desktop is the practical delivery layer of IGEL’s Preventative Security vision. It translates strategic alignment and hardened architecture into a secure, streamlined, and personalized user experience.
This is where compliance, control, and creativity coexist. And it’s available now — through IGEL, through our ecosystem of IGEL Ready partners, and most importantly, through your own enterprise security and workspace vision.
Because transformation isn’t something you wait for. It’s something you deliver — securely, simply, and at scale.
For more information on the Preventative Security Architecture, the Preventative Security Model, and the Adaptive Secure Desktop, please submit the form below.
The post One Workspace, Every User – The Power of the Adaptive Secure Desktop™ appeared first on IGEL.
]]>The post From Reactive to Resilient – Inside the Preventative Security Architecture™ appeared first on IGEL.
]]> (PSM) — IGEL’s strategic framework for aligning endpoint, security, and application strategies across the modern enterprise. But strategy without execution is just ambition.
(PSM) — IGEL’s strategic framework for aligning endpoint, security, and application strategies across the modern enterprise. But strategy without execution is just ambition.
That’s where IGEL’s Preventative Security Architecture comes in.
Beyond “Monitor, Detect, Remediate”
Traditional endpoints were designed for general-purpose use—built to accommodate consumers, gamers, and enterprises alike—not to meet the specific demands of secure enterprise environments. Today’s standard endpoint stack is designed to detect, monitor, and remediate threats — assuming that compromise is inevitable.
IGEL turns that assumption on its head.
The Preventative Security Architecture takes a fundamentally different approach — one that prioritizes designing out risk through immutability, minimalism, and policy enforcement at every layer of the endpoint experience.
This isn’t just a better way to secure IGEL OS. It’s a blueprint for customers to establish their own preventative security architecture — one that aligns with their Zero Trust journey, compliance goals, and operational realities.
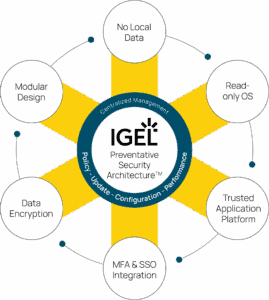
The Core Principles of Preventative Security Architecture
The architecture rests on five pillars:
- Immutable OS State: IGEL OS is locked down at the system level. Unauthorized changes simply can’t persist — or even run.
- Zero Local Data: No data lives on the endpoint. IGEL endpoints are stateless — there’s nothing to exfiltrate or encrypt.
- Secure Boot and Trusted Application Platform: Boot-time chain-of-trust backed by UEFI and TPM ensures only validated components load.
- Minimal Attack Surface: A 2GB core footprint, with optional modules added only as needed — reducing vulnerability density.
- Centralized, Granular Policy Control via UMS: Over 9,000 configurable settings. Enforce consistency without needing endpoint agents.
This is what “secure by design” looks like in practice — not theoretical protections, but tangible barriers that eliminate the opportunity for exploitation.
Your Preventative Security Architecture
This isn’t about locking customers into IGEL’s view of security. It’s about giving them a foundation to build their own preventative strategy — a Preventative Security Architecture that scales with their policies, their risks, and their compliance mandates.
Whether it’s:
- Rolling out a Zero Trust initiative,
- Aligning SOC frameworks such as NIST CSF or ISO 27001,
- Responding to rising ransomware threats
- Transitioning from Windows to a hybrid DaaS model,
IGEL’s architecture supports that journey. Not by dictating it — but by enabling it.
IGEL Ready – The Ecosystem That Powers It
Every strong architecture needs strong integrations. These are provided by the IGEL Ready program.
Through our expansive partner ecosystem, organizations can integrate leading Zero Trust, SSE/SASE, IAM, UEM and compliance solutions into the IGEL experience — natively. Partners like:
- Zscaler, Palo Alto, Netskope (for secure access)
- Microsoft Entra ID, Workspace ONE Access, Imprivata and Okta (for identity and conditional access)
- Island and Microsoft Edge (for browser-based workspaces)
- HP, LG, Lenovo (for secure and sustainable hardware endpoints)
These aren’t bolt-ons. They’re validated. Secure. Orchestrated. And ready to scale.
The Payoff – Simpler, Safer, Resilient
By adopting a preventative security architecture, enterprises can:
- Reduce risk – by removing attack vectors before they can be exploited.
- Reduce cost – by eliminating layers of endpoint agents and streamlining patch cycles.
- Reduce noise – by minimizing alerts and avoiding alert fatigue.
- Improve compliance – through posture-based access and centralized controls.
This is the architecture for the next generation of secure work — and it’s not just IGEL’s. It’s yours.
In Part 3, we’ll tie it all together with the Adaptive Secure Desktop — a dynamic, context-aware workspace delivery model that puts this architecture into motion for every user, device, and role.
— a dynamic, context-aware workspace delivery model that puts this architecture into motion for every user, device, and role.
The post From Reactive to Resilient – Inside the Preventative Security Architecture™ appeared first on IGEL.
]]>The post Rethinking Endpoint Strategy with IGEL appeared first on IGEL.
]]>
This needs to be the era of designing for failsafe.
Instead of relying on detection and remediation, the endpoint must be built to resist compromise — integrated, intelligent, and inherently resilient. IGEL’s Preventative Security Model is the strategic foundation for that shift.
is the strategic foundation for that shift.
This blog series unpacks the full scope of IGEL’s security and workspace transformation strategy in three parts:
- Preventative Security Model
 – IGEL’s unifying framework that aligns application access, security, and hardware strategy.
– IGEL’s unifying framework that aligns application access, security, and hardware strategy. - Preventative Security Architecture
 – The enforcement layer that operationalizes failsafe and becomes your organizations Preventative Security Architecture.
– The enforcement layer that operationalizes failsafe and becomes your organizations Preventative Security Architecture. - Adaptive Secure Desktop
 – A curated on-demand workspace that meets every user, role, and risk profile.
– A curated on-demand workspace that meets every user, role, and risk profile.
The Preventative Security Model
The Preventative Security Model (PSM) is IGEL’s approach to unifying modern endpoint strategies. It’s not an agent. It’s not a policy engine. It’s a philosophy — one that repositions the endpoint from a reactive risk surface to a strategic control layer.
And it’s built for a world that looks very different than it did five years ago.
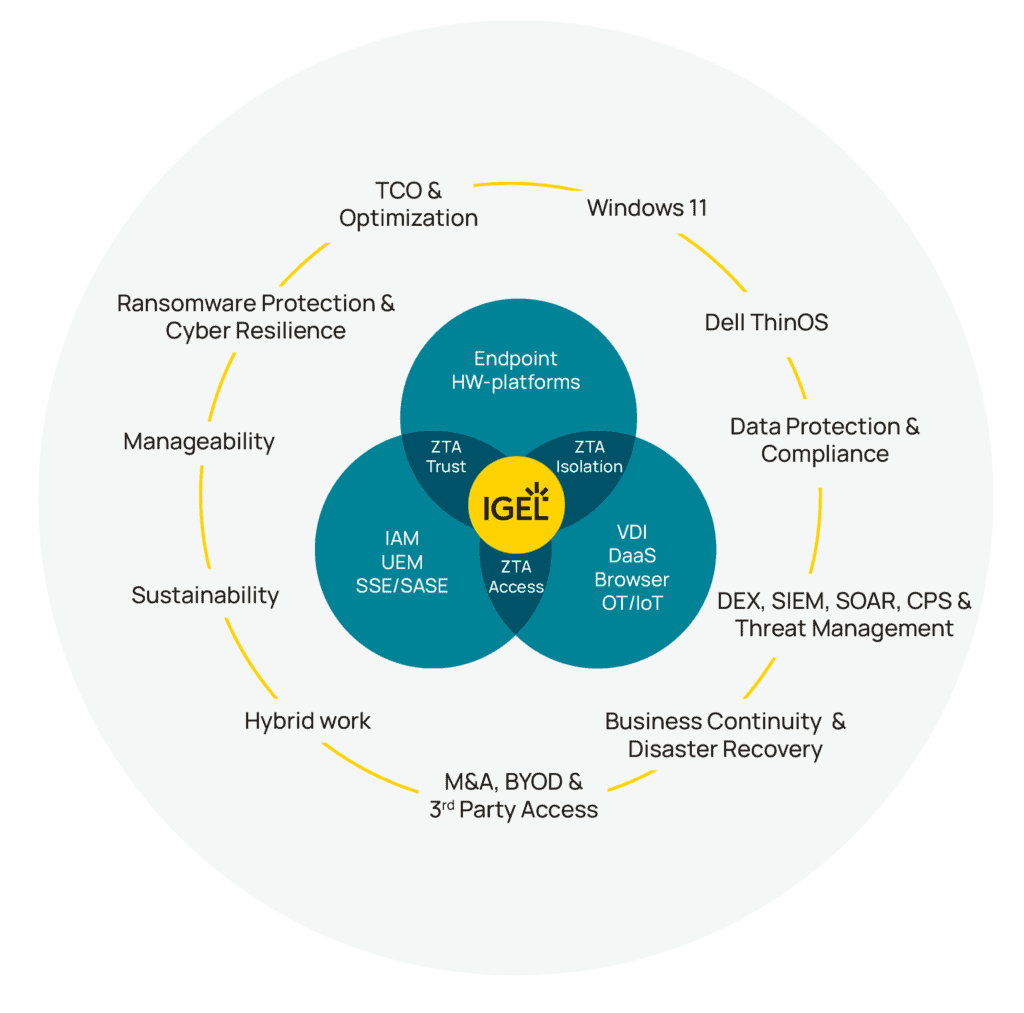
The Endpoint Has Shifted — So Must Our Strategy
Enterprise computing has moved. Workloads have left the endpoint. SaaS, DaaS, and enterprise browsers now carry the weight of productivity. Users roam. Devices are fluid. Data must stay protected — without relying on where it physically lives.
IGEL is the constant in that transition. Both now and next.
The Preventative Security Model provides the framework that connects:
- Application access: Whether delivering full desktops, browser-based tools, native Linux apps, Progressive Web Apps, hybrid SaaS, or even Windows workloads, PSM enables five flexible delivery models — each tailored to user’s needs and risk posture.
- Zero Trust strategy: Zero Trust is a security model that assumes no user or device is inherently trusted and requires continuous verification of identity, context, and access for every interaction within a network. Zero Trust isn’t a product. You don’t buy Zero Trust from a single company. PSM integrates deeply with leading IAM, UEM, SASE, and SaaS vendors to enforce Zero Trust principles from the device outward for secure information access.
- Endpoint sustainability: With endpoints no longer requiring three-to-five-year hardware refreshes due to the simplified workloads, PSM supports long-term device reuse — particularly relevant as organizations scramble to meet Windows 10 EOL activities and deadlines, the EU’s Corporate Sustainability Reporting Directive(CSRD), and Environmental, Social and Governance targets (ESG)
- Operational flexibility: From remote onboarding to rapid reconfiguration during M&A, PSM provides the consistency needed to adapt at speed.
IGEL Ready – The Force Multiplier for the Preventative Security Model
PSM is powered by the IGEL Ready ecosystem — a diverse and growing network of partners across security, identity, peripherals, communications, and hardware. These aren’t just integrations. They’re certified relationships that extend IGEL’s strategy into enterprise environments at scale.
Through IGEL Ready, PSM supports:
- HP, LG, Lenovo, and other leading OEMs to ensure secure, performant hardware compatibility.
- Identity platforms like Microsoft’s EntraID, Omnissa Workspace ONE Access, Imprivata, Okta and Ping for integrated SSO and MFA.
- Security vendors including Zscaler, Palo Alto Networks, and Netskope for Zero Trust and SSE enforcement.
- Peripheral support for clinical, financial, manufacturing, government and retail workflows — including smartcards, speech mics, OT equipment, barcode scanners, document scanners and signature pads to name only a few.
Together, this ecosystem ensures that IGEL endpoints can sit at the centre of a modern, multi-vendor Zero Trust strategy — without friction, without fragility.
Strategic Outcomes Delivered
The Preventative Security Model is not just about securing endpoints. It’s about enabling enterprise transformation. Across industries, PSM is already delivering impact:
- Business Continuity: Fast recovery of compromised traditional endpoints utilizing the in-place hardware
- M&A acceleration: Standardize and secure diverse endpoint fleets across acquired orgs without rip-and-replace.
- Windows 11 readiness: Shift Windows to the cloud, maintain existing hardware, and simplify support.
- Sustainability, CSRD and ESG: Extend endpoint lifespan, reduce e-waste, and align IT with carbon reduction targets.
- Zero Trust execution: Connect policy enforcement from identity to device, in real time, at scale.
Where traditional endpoint stacks are reactive and bloated, PSM is lightweight, adaptive, and policy-aligned — a failsafe foundation for the cloud-first enterprise.
Next up: Preventative Security Architecture, where we explore how IGEL OS eliminates attack vectors and enforces failsafe security by design.
The post Rethinking Endpoint Strategy with IGEL appeared first on IGEL.
]]>The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The retail sector continues to experience an increase in cyber threats, driven by outdated infrastructure, distributed environments, and expanding attack surfaces. Recent data breaches involving well-known brands such as Harrods, Marks & Spencer, Cartier, The North Face, and Victoria’s Secret have brought this issue to light. These events underscore the dynamic and complex threat environment that retailers face today. They also emphasize that retail is a key target for well-resourced and opportunistic threat actors.
In the last two years, the retail sector has experienced a substantial increase in cybersecurity vulnerabilities and breaches, leading to serious operational and financial ramifications. In 2024, 80% of retailers reported being targets of cyberattacks, with over half admitting a growing sense of vulnerability to these threats[1]. The frequency and severity of these incidents are increasing: retail data breaches grew by 18% year-over-year in 2024, with the average breach now costing $2.96 million[2].
Ransomware continues to pose a sizable threat, with the retail industry being the second most targeted sector for ransomware attacks in 2023 and the first half of 2024. In this timeframe, the U.S. retail sector reported 256 ransomware incidents in 2024, an increase from 206 incidents reported in the first three quarters of 2023[3].
Understaffed IT teams, high turnover, and a lack of cybersecurity training, particularly for temporary and seasonal staff, have heightened vulnerabilities. The repercussions of these breaches go well beyond immediate financial impacts. Business disruptions and the damage to their reputation can be considerable and profound.
Notably, 33% of retailers have faced regulatory action due to inadequate protection of customer data[4].
What is especially concerning about these incidents is their tendency to exploit vulnerabilities that could be addressed with effective preventive security measures. This highlights the urgent need for a more comprehensive and strategic approach to cybersecurity.
Traditional cybersecurity measures aren’t keeping pace
The retail sector’s IT infrastructure is inherently vulnerable. The attack surface is wide with thousands of distributed locations, outdated systems that are challenging to update, third-party connections, and the need for constant uptime. Additionally, the rise of e-commerce has turned retail into a 24/7/365 operation, placing additional strain on IT resources and creating more potential vulnerabilities. Furthermore, risks extend beyond retail stores—logistics, inventory management, transportation, and backend systems all present possible attack access points.
Traditional security tools have not kept pace with the evolving landscape of cyber threats. Many of these solutions were originally designed for static and centralized environments, making them increasingly inadequate in the face of fast-moving threats that can easily exploit vulnerabilities across distributed and diverse endpoints such as laptops, smartphones, and cloud services, which often fall outside the direct control of traditional security measures.
Once attackers access a network, they can move laterally within the system, navigating various connected devices and systems. This lateral movement can occur alarmingly quickly, often within just a few minutes, enabling them to disable critical services and infrastructure before a retailer realizes it has been compromised.
Preventative Security as a Strategic Shift
Today’s retailers require lightweight, efficient, and functional security within limited infrastructure. More importantly, they need systems that stop breaches before they escalate.
This necessitates a strategic shift from reacting to preventing threats, and one way in which retailers can improve endpoint security is by adopting IGEL’s Preventative Security Model .
.
For retailers, IGEL OS, the Secure Endpoint OS for Now & Next:
- Immutable, read-only OS: Reduces exploitability and eliminates persistence of malware.
- Centralized configuration management: Via IGEL UMS, enabling rapid policy deployment across distributed fleets.
- Boot chain of trust: UEFI Secure Boot through to application launch, validating integrity at every step.
- PCI-DSS alignment: Designed to protect PII and cardholder data, reducing compliance burden.
- Single sign-on integration: With platforms like Okta, Entra ID, and Ping Identity to enforce identity-driven access control.
- Peripheral and protocol compatibility: Ensures business continuity without compromising usability.
- Ransomware mitigation: Architectural safeguards lower both the probability and the impact of endpoint compromise.
Rethinking Endpoint Recovery for Business Continuity
For organizations still relying on traditional endpoints, recovery from a security event often translates to logistical disruption. Device reimaging, hardware replacement, and manual reconfiguration introduce significant delays—especially in distributed retail environments with limited IT presence. When laptops are compromised or encrypted by ransomware, recovery can require full device replacement, resulting in downtime, shipping delays, and high support overhead.
IGEL OS can be used to return services utilizing the compromised endpoint hardware in place. IGEL OS runs from a read-only partition with no local data persistence. Compromised endpoints can be quickly restored using IGEL USB Boot, Dual Boot, or managed hypervisor fallback methods. This eliminates the need for physical device swaps or complex reimaging workflows.
The result is a business continuity model that is immediate, scalable, and resilient—even in environments with constrained IT support. IGEL allows organizations to return to a known-good state in minutes, not days, reducing operational disruption and breach containment costs. When combined with centralized policy enforcement via IGEL UMS, this architecture ensures security and continuity across the entire endpoint estate—without increasing complexity.
Final Thoughts
Retail security leaders are no longer measured solely by breach prevention—but by how effectively they limit operational impact when threats materialize. The endpoint remains one of the most exposed surfaces in this equation. IGEL offers an architecture that reduces the likelihood of compromise and provides rapid continuity for traditional endpoints. For CISOs, adopting a preventative, resilient endpoint strategy is not just a security imperative—it’s a business enabler.
To learn more about IGEL’s Preventative Security Model and IGEL OS: The Secure Endpoint OS for Retail, click here.
[1] https://www.vikingcloud.com/blog/retail-cybersecurity-stats-threats-and-solutions
[2] https://www.nccgroup.com/us/is-your-retail-business-prepared-for-cyber-threats-this-2024-holiday-season/
[3] https://cyberint.com/blog/other/retail-threat-landscape-2024/
The post Redefining Resilience in Retail IT appeared first on IGEL.
]]>The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The new research from Gartner, “Improve Business Continuity Using Desktop as a Service” is striking a similar chord with me. If the enterprise desktop place that we are living in today is so vulnerable, why don’t we just move to the place that is safer?
Stay with me..
The July 2024 CrowdStrike agent failure was a powerful example of the operational exposure most organizations still face. Gartner’s research “Improve Business Continuity Using Desktop as a Service” which references this incident, highlights the strategic role of Desktop as a Service (DaaS) and cloud-hosted virtual desktops in minimizing downtime, and also the use, of what Gartner term a “thin client operating system”. But in doing so, it also highlights a prevailing mindset: **that we are designing the endpoint for failover, rather than designing for failsafe.**
Lets quickly tackle that term – “thin client operating system”. Now I’m looking at this it deserves its own blog, but – The term “thin client” is inextricably linked to the hardware. Search on the term “thin client” and what do you see? A page full of hardware. Wikipedia even states “a simple (low-performance) computer”. Ask an AI engine what the benefits of a thin client are and you’ll find improved security, lower TCO, improved reliability and uptime. Lets take those benefits (often, but not always, delivered by or enabled by the software – IGEL) and lets run them on any device,not just “thin clients”.
At IGEL, we believe in a more targeted, fit for purpose strategy: Yes, have a plan. Yes, embrace VDI, DaaS and browser. But first, ask: what if your endpoint was designed to minimize the risk of failure in the first place?
The Recovery Assumption: The Traditional Endpoint as the Failure Point
Gartner is right to emphasize preparedness. Failures—from agent misfires to ransomware—do happen. But implicit in the recovery model is the assumption that a traditional, built for every eventuality, writeable endpoint is the default (specifically calling out resetting it). And that means layering on security agents, patching, backups, and more.
IGEL, see the endpoint differently: not as something to defend with layers, but something to simplify and harden by design.
Security by Design: The Preventative Security Model
IGEL’s Preventative Security Model shifts endpoint thinking from detection and remediation to proactive prevention and simplification.
- Immutable, Read-Only OS: Stops tampering and malware persistence.
- No Local Data: Removes exfiltration and encryption targets.
- Cryptographically Verified Boot: Ensures the system starts in a known-good state.
- Minimized Attack Surface: Only the necessary components are delivered to the device.
This is not about claiming unbreakable software. IGEL OS is software after all. But it’s software architected with the principles of Zero Trust and attack surface minimization at its core.
Workloads no longer run at the endpoint
With applications increasingly moving away from the endpoint and into the cloud, and Gartner themselves predicting that by 2030 Secure Enterprise Browsers will be a central component of application access strategies, isn’t it time to rethink the endpoint? Isn’t this a point in time to redefine the enterprise endpoint – just like the Enterprise Browser is being redefined?
Business Continuity Begins with Fewer Incidents
Gartner is right: you need a business continuity plan. Virtual desktops and cloud scaling are essential. But we believe true endpoint resilience starts before recovery:
- Design devices that are difficult to compromise
- Limit what runs locally and how it’s accessed
- Deliver workspaces adaptively, based on user role and risk
Case in Point: Dual-Layer Resilience in Action
During the July 2024 CrowdStrike incident, IGEL endpoints remained operational and unaffected. Azure Virtual Desktops could be reset in minutes, as shared by Microsoft’s Scott Manchester—showcasing the agility of modern cloud workspaces. This isn’t applicable to AVD, but all DaaS providers. This combination—IGEL at the endpoint and workloads (DaaS, Enterprise Browser) in the cloud—represents a blueprint for secure, scalable, and resilient desktop delivery.
So (and you’ve been patient) if our destination, in the event of a compromise or failure, is a more resilient infrastructure, powered by a more resilient endpoint operating system and VDI, DaaS, or enterprise browser – rather than go on holiday there, why don’t we just live there?
The post From Recovery to Resilience: Rethinking Endpoint Continuity in a Zero Trust World appeared first on IGEL.
]]>The post Securing Biomedical Devices in Healthcare with IGEL Managed Hypervisor appeared first on IGEL.
]]>Healthcare organizations face an escalating cybersecurity risk as biomedical teams continue running critical medical devices on older versions of Windows. These legacy systems, often essential for imaging machines, meds dispensing, and diagnostic tools, remain unpatched and vulnerable due to vendor restrictions, operational dependencies, or the excessive costs associated with replacing medical hardware. Not only does this create a security issue, but it also creates an operational issue in finding hardware for these critical controllers to run on as new hardware – think TPM2 chips – does not support the outdated version of Windows.
According to a Help Net Security report, 70 percent of medical devices in hospitals run outdated operating systems, making them prime targets for cyberattacks. Meanwhile, research from Claroty’s Team82 found that 63 percent of known vulnerabilities tracked by CISA exist within healthcare networks, due to aging infrastructure and the inability to update Windows-based systems.
The need for a secure, efficient, and cost-effective way to continue operating these devices, using new endpoint hardware, without exposing hospitals to cybersecurity threats is more urgent than ever. This is where IGEL Managed Hypervisor comes in.
How IGEL Managed Hypervisor Strengthens Security for Biomedical Devices
Isolating Vulnerable Windows Instances
IGEL Managed Hypervisor allows biomedical teams to run legacy Windows-based applications securely within a controlled virtualized environment. Instead of running outdated Windows versions directly on endpoint hardware, the IGEL OS acts as a separation layer between the hardware and the Windows instance running inside a managed hypervisor. This approach eliminates persistent malware risk by ensuring a fresh Windows session at every reboot, and provides a read-only, tamper-proof operating environment.
Extending Medical Device Lifecycles with IGEL Managed Hypervisor
Many medical devices rely on outdated versions of Windows, which are incompatible with modern hardware. This forces healthcare organizations to source and maintain aging systems—an expensive and unsustainable approach. IGEL Managed Hypervisor solves this by decoupling software from hardware, enabling legacy Windows-based medical applications to run securely on modern devices. This eliminates the need for outdated equipment, reduces maintenance costs, and enhances security, allowing hospitals to extend the lifecycle of critical medical devices without compromise.
Meeting Compliance and Zero Trust Security Requirements
Regulatory bodies like HIPAA, FDA, and NIST emphasize cybersecurity in medical technology, yet legacy Windows systems often lack built-in Zero Trust protections. IGEL Managed Hypervisor, built on the Preventative Security Model, provides a secure-by-design endpoint foundation that integrates with leading Zero Trust Architecture (ZTA) solutions. It adds an additional firewalling layer to prevent malicious activity and works alongside network segmentation tools to contain threats. By enabling IT to create an immutable, rollback-ready Windows environment, IGEL ensures medical systems can be restarted in a known-good state—much like a non-persistent VDI desktop—supporting the uptime and availability critical for patient care.
Seamless Integration with Existing IT Infrastructure
Healthcare IT teams are stretched thin, managing both modern and legacy environments. IGEL Managed Hypervisor is managed from the IGEL UMS simplifying endpoint management by allowing centralized policy enforcement across all devices, enabling remote updates and patches without disrupting workflows, and supporting Browsers, SaaS, DaaS and VDI integrations
Why IGEL is the Right Fit for Healthcare Biomedical Teams
Hospitals need a pragmatic security approach that works within existing constraints. IGEL Managed Hypervisor offers a security-first design that minimizes attack surfaces by isolating legacy Windows environments, removes the issue of maintaining old hardware, reduces hardware refresh cycles and extends device lifespans, and works across distributed healthcare environments with zero-trust-ready architecture.
In a time where cyber threats to medical infrastructure are escalating, IGEL provides a proven, scalable, and secure way to modernize healthcare IT without disruption.
Want to Learn More?
If your biomedical team is managing legacy Windows devices, IGEL Managed Hypervisor can help secure your infrastructure without sacrificing operational efficiency. Contact us today to discuss how we can help your healthcare organization stay protected.
Learn more about IGEL Managed Hypervisor
View the Demo Video
The post Securing Biomedical Devices in Healthcare with IGEL Managed Hypervisor appeared first on IGEL.
]]>The post IGEL Insights to Deliver Unified Endpoint Telemetry & Management Data appeared first on IGEL.
]]>Gaining visibility into endpoint performance, security, and user experience has long been a challenge. Many monitoring and analytics tools require custom-built agents or complex integrations, adding operational overhead while increasing security risks. IGEL Insights eliminates these barriers, delivering real-time telemetry and data management through a new API and an integrated IGEL UMS dashboard.
This enables IT teams, security analysts, and technology partners to access critical endpoint data without the need for custom IGEL agent applications. By integrating IGEL Insights with DEX, SIEM, SOAR, Threat Management, and Cyber-Physical System Monitoring solutions, organizations can reduce downtime, enhance security, and optimize endpoint performance.
What IGEL Insights Will Deliver
IGEL Insights will provide two key access points for understanding and managing IGEL OS endpoints:
IGEL UMS Dashboard: Real-Time Performance Data for IT Administrators
- A built-in dashboard within IGEL Universal Management Suite (UMS) will provide key performance and system health metrics for IGEL administrators.
- IT teams will be able to monitor endpoint activity, identify performance issues, and optimize operations without the need for external integrations.
- Designed for day-to-day management, the UMS dashboard will present a curated set of essential data while maintaining a simple and intuitive interface.
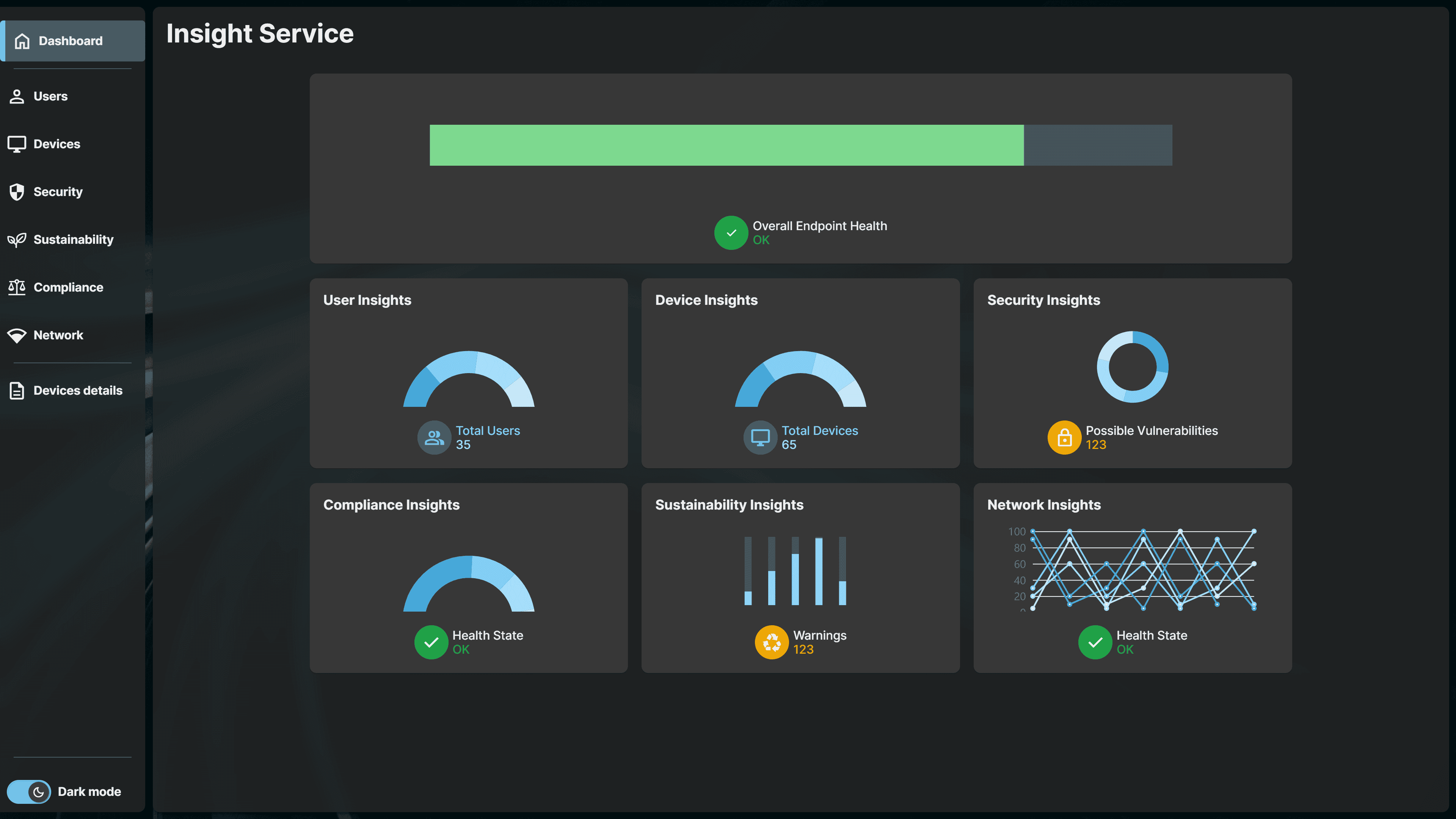 IGEL Insight Service Dashboard. Click image to view the demo video.
IGEL Insight Service Dashboard. Click image to view the demo video.
IGEL Insights API: Deep Endpoint Intelligence for Partners & Security Teams
- The IGEL Insights API will expose 100% of the captured telemetry and management data for integration with DEX, SIEM, SOAR, Threat Management, and Cyber-Physical System Monitoring solutions.
- Partners and IT teams will be able to correlate IGEL OS telemetry with other IT and security data for root cause analysis, compliance enforcement, and proactive threat detection.
- Removes the need for custom IGEL agent applications, allowing direct agentless access to data for real-time monitoring and automation.
Transforming Endpoint Monitoring and Security
By leveraging IGEL Insights, organizations will gain a new level of visibility into endpoint behavior while enhancing their existing monitoring and security platforms.
- IT administrators will benefit from integrated performance monitoring through IGEL UMS, ensuring high availability and uptime.
- Technology partners and security teams will gain deep telemetry data via API, enabling them to improve root cause analysis and incident response.
- Enterprise IT teams will be able to reduce support costs, optimize remote work environments, and improve compliance through enhanced endpoint intelligence.
With the first partner API expected at the end of Q2, IGEL is expanding how organizations access and leverage IGEL OS data to support security, compliance, and performance initiatives.
Enhancing IT & Security Through Seamless Data Integration
By making real-time telemetry and management data more accessible, IGEL Insights will empower organizations to take a proactive approach to endpoint security and performance. Whether through the integrated IGEL UMS dashboard or the comprehensive IGEL Insights API, IT teams and security partners will be able to act faster, reduce risk, and optimize user experience—without unnecessary complexity.
Want to learn more?
Stay tuned for upcoming announcements and prepare to integrate IGEL Insights into your security and IT operations strategy.
View the Demo Video
The post IGEL Insights to Deliver Unified Endpoint Telemetry & Management Data appeared first on IGEL.
]]>The post Expand App Access on IGEL OS with Progressive Web Apps appeared first on IGEL.
]]>Why Progressive Web Apps Matter
PWAs bridge the gap between web and native applications, delivering an app-like experience while remaining lightweight and browser-based. They bring several benefits, including:
- Offline Support – PWAs can function even when connectivity is limited.
- Push Notifications & Background Sync – Improves engagement and real-time updates.
- Cross-Platform Compatibility – Works seamlessly across devices and operating systems.
- Centralized Deployment – IGEL administrators can deploy PWAs to IGEL OS desktops, allowing users to access them just like any other application, with a seamless launch experience.
For IGEL OS users, this means another secure and efficient way to access enterprise applications while maintaining IT control and minimizing overhead.
Expanding Application Delivery: PWAs & Beyond
PWAs complement the existing application delivery methods IGEL already provides:
- Virtual Apps & Desktops via DaaS & VDI – With Omnissa, Microsoft AVD/Windows 365, and Citrix, organizations can virtualize applications securely without endpoint dependencies.
- Enterprise Browsers – IGEL OS natively supports Edge, Firefox, and Island, providing secure, direct access to web applications.
- IGEL Managed Hypervisor (IMH) – When Windows is required at the endpoint, IMH delivers an immutable, rollback-ready Windows instance for critical environments.
- Additional PWAs – expanding the number of PWA’s available from the IGEL App Portal now including Microsoft Office apps like Teams, Outlook, Word, Excel, PowerPoint, and Copilot, and Google Gmail, centrally managed and deployed for seamless access.
A Secure Foundation with the Preventative Security Model
Like all IGEL innovations, PWA support is built on the foundation of the Preventative Security Model (PSM), ensuring:
- A secure-by-design approach that eliminates attack vectors rather than reacting to them.
- Integration with IGEL’s security ecosystem, including authentication, encryption, and Zero Trust principles.
- Simplified management and control—centralizing security and access policies while reducing endpoint complexity.
A Unified Approach to Secure Application Access
With expanded PWA support, IGEL OS offers an even broader application access strategy that meets organizations where they are—whether through DaaS, VDI, enterprise browsers, hypervisor-based Windows, or IGEL native apps. By enabling centralized deployment of PWAs, IGEL ensures users experience them just like traditional applications, while IT maintains full control over security, configuration, and access policies.
Ready to Leverage PWAs on IGEL OS?
If your organization is looking for a modern, secure, and cost-effective way to deploy applications, PWAs on IGEL OS are an excellent option. Combined with our robust ecosystem of application delivery methods, IGEL provides the ultimate flexibility for secure enterprise access.
Would you like to explore how IGEL OS can support your digital workspace strategy?
View the IGEL PWA demo video
Contact us today to learn more.
View the Microsoft Teams PWA on IGEL App Portal
The post Expand App Access on IGEL OS with Progressive Web Apps appeared first on IGEL.
]]>The post It’s in the data. Security needs a rethink in 2025 appeared first on IGEL.
]]>Low confidence, large investment?
Among the baffling findings of the study is the fact that even organizations that hadn’t been hit by a ransomware attack had low confidence that endpoint security tools would intercept an attack – only 25%. A statistic unfortunately born out by the attack success rates.
A patchwork of solutions – hope vs strategy
The article highlights that 23% of organizations are running more than five tools and agents on their endpoints which “they do not see as ideal”. This complexity at the endpoint only drives up the OpEx costs of managing and maintaining the endpoint estate, consuming the resources of IT and putting focus on keeping the lights on rather than innovation. And with the actual effectiveness, and confidence in these solutions already at a low, is this really the right strategy?
New year – new you!
Increasingly, applications are not actually being run at the endpoint. For an ever increasing percentage of users, they are using SaaS apps or virtualized apps. Research from ESG highlighted that just 5% of organizations surveyed are delivering virtual desktops and applications to more than 75% of their users, which I’d expect, virtualization has often been a specific tool for specific use cases rather than a blanket approach, but this number is forecasted to grow to a whopping 38% of respondents in just two to three years! So if you aren’t deploying a traditional endpoint approach, why are you still deploying a traditional endpoint and all of its, erm, nuances… Maybe a new year’s resolution should be to ask whether previous assumptions and approaches are the right assumptions and approaches for the modernizing end user computing arena.
A Preventative Security Model
Rather than continuing to patch over the cracks with additional tools, enterprises must rethink endpoint security from the ground up. A Preventative Security Model emphasizes building a foundation where endpoints are inherently secure. This means adopting solutions that are purpose-built for secure operations, reducing the attack surface rather than simply detecting and responding to threats after they’ve breached defenses. Designed with Zero Trust principles and integrated into other Zero Trust technologies, IGEL OS provides a lightweight, Linux-based operating system optimized for endpoints in SaaS and virtualized environments. IGEL minimizes vulnerabilities by operating within a locked-down framework, ensuring that endpoints are inherently secure.
Eliminating complexity
One major advantage of adopting a secure-by-design endpoint is the simplification of endpoint management. Instead of running multiple security tools that create complexity, highlighted earlier as a concern, organizations can eliminate endpoint security tools from both their CapEx and OpEx freeing funds for further EUC modernization or Zero Trust security based projects.
Proven effectiveness in enterprise environments
The real-world efficacy of IGEL’s model is evident across industries like healthcare, manufacturing, and government. These sectors, often targeted in ransomware attacks, have found success in deploying IGEL as part of a zero-trust framework. By reducing reliance on traditional endpoint security platforms and focusing on prevention, these organizations have achieved greater resilience against modern cyber threats.
Shifting the paradigm
The 451 Research study underscores a critical need for a paradigm shift in how we approach endpoint security. The current patchwork of tools and reactive investments isn’t sustainable in the face of evolving ransomware strategies. Instead, enterprises must adopt preventative models that reduce the likelihood of breaches and simplify security architectures.
Conclusion: Prevention is the future
The data is clear: endpoint security as it exists today isn’t working. Enterprises must stop relying on reactive measures and instead invest in technologies that are secure by design. IGEL’s preventative approach offers a proven path forward, enabling organizations to protect their endpoints effectively without the complexity of traditional tools. The time to rethink endpoint security is now—because the cost of inaction is far too high.
The post It’s in the data. Security needs a rethink in 2025 appeared first on IGEL.
]]>The post Preparing for DORA: Strengthening Your Operational Resilience with IGEL appeared first on IGEL.
]]>The Digital Operational Resilience Act (DORA) is a legislative initiative established to support the European Digital Finance Strategy, which encourages innovation while ensuring strong security and protection for consumers and businesses. It requires financial entities to enhance their ICT risk management, incident response, and third-party risk management strategies, ensuring the resilience of services critical to the financial system.
The act will go into effect across the European Union (EU) on January 17, 2025, marking a major milestone in financial regulation. Due to technology’s global impact on the financial services sector, CISOs, compliance officers, and risk management teams outside the EU must prepare now for DORA’s implementation.
IGEL’s Preventative Security Model and DORA
and DORA
At IGEL, we recognize the significance of DORA and its influence on our partners and customers. The IGEL Preventative Security Model supports DORA’s operational resiliency requirements. It helps financial institutions comply with the legislation across several key areas, from ICT risk management to incident response, through its key components that include:
- IGEL OS, a Linux-based secure operating system designed to deliver critical business applications across diverse environments, including Enterprise Browsers, SaaS, DaaS, and VDI.
- IGEL OS removes the vulnerabilities targeted by bad actors through the Preventative Security Model core, these include:
- A Read-only OS that cannot be altered by malware
- No local data storage prevents leaks generated from lost or stolen devices
- Trusted application platform ensures the integrity of the endpoint OS through UEFI secure boot, enabling fast recovery from attempted cyber-attacks.
- Identity and Access Management (IAM), Unified Endpoint Management (UEM), Single Sign-On (SSO), Security Service Edge (SSE), and Secure Access Service Edge (SASE) are enhanced through partnerships with leading vendors, including Citrix, Imprivata, Microsoft, Okta, Ping Identity, and Omnissa. This approach ensures that security is applied consistently across all endpoints and supports essential elements of the Zero Trust framework, including users, devices, applications, workloads, networks, and visibility and analytics.
- A modular design and a much smaller attack surface than a traditional endpoint OS ensure that the end user has only what they need to be productive.
- Partnerships with HP, LG, and Lenovo enable IGEL to deliver IGEL OS on factory-shipped devices that are secure out-of-the-box and promote operational resilience and compliance with Zero Trust architecture.
- Integration with enterprise SaaS and DaaS solutions, including Citrix, Microsoft and Omnissa, ensures end-to-end security for third-party applications. This helps financial institutions mitigate third-party ICT risks as required by DORA and achieve compliance across complex IT environments
- IGEL’s Business Continuity service offers a robust recovery option for devices that must run on Windows, ensuring operational resilience during incidents. This ensures that financial institutions can meet DORA’s demand for continuous service availability, even in environments where IGEL OS may not be used on every device.
- Disaster recovery licensing provides a clean boot into IGEL OS via an external UD Pocket or second partition, allowing financial institutions to recover compromised Windows devices rapidly. This solution is critical for meeting DORA’s requirements for timely response and recovery from ICT incidents
- Operational Resilience Testing helps organizations comply with DORA’s requirements for regular testing of ICT systems and recovery plans. This service ensures that financial institutions are fully prepared to handle potential disruptions.
- ISO27001 Certification provides a layer of assurance for financial institutions by adhering to internationally recognized standards for information security management, helping financial organizations demonstrate compliance with DORA’s stringent requirements for third-party risk management.
Upcoming event showcases how to reduce risk and comply with DORA
Because DORA places significant demands on financial institutions to strengthen ICT risk management, enhance incident response, and ensure third-party service providers maintain the same level of operational resilience, IGEL is teaming with Amulet Hotkey and Island – The Enterprise Browser to present “EUC Endpoint Security Showcase for Financial Services.”
During the event, which will be held November 14 in Manchester, UK, attendees will learn how their organization can reduce risk, enhance its cybersecurity posture, and comply with DORA by diversifying away from a single endpoint OS strategy, thus avoiding a single point of failure across the estate.
Space is limited, so register today by clicking here. For more information on IGEL for Business Continuity, click here.
The post Preparing for DORA: Strengthening Your Operational Resilience with IGEL appeared first on IGEL.
]]>