The post How IGEL and Omnissa Deliver Secure and Efficient User Desktop and Application Solutions appeared first on IGEL.
]]>To begin to understand the impact of these two companies’ solutions, imagine a self-service approach to onboarding and accessing corporate computing resources. Simply adding users to an organization domain, the when, where, and how an end user sets up his or her workstation and gains secure access to applications is a completely automated process requiring no operational support from IT.
In this article, we will explore how these two companies work together to ensure flexible, scalable, secure, and cost-efficient access to virtual desktops and applications while delivering:
- End-to-End Security
- Service Continuity
- Enhanced User Experience
- Cost Savings
Meeting In the Middle
IGEL and Omnissa each provide separate halves of the desktop and application delivery solution stack. Omnissa manages the secure delivery of desktops and applications, and IGEL securely connects users to their desktop and application resources.
IGEL – The Endpoint Device Solution
The IGEL solution begins with the IGEL Secure Endpoint OS (aka IGEL OS). IGEL OS is a highly secure, fully encrypted, lightweight operating system designed specifically for accessing desktops and applications delivered by Omnissa. It provides unparalleled endpoint security through IGEL’s Preventative Security Model to ensure device integrity and improve stability while reducing its attack surface, which minimizes the risk of cyber threats like malware, ransomware, and other vulnerabilities.
to ensure device integrity and improve stability while reducing its attack surface, which minimizes the risk of cyber threats like malware, ransomware, and other vulnerabilities.
IGEL includes unified management that offers centralized control of all IGEL OS-powered devices. This is achieved through a next-generation cloud platform called IGEL Cloud Services that includes the IGEL App Portal, the IGEL Onboarding Service, Licensing, and Insights.
This combination of IGEL OS and IGEL Cloud Services provides device deployment and configuration, control over local applications, and secure access to computing resources delivered by Omnissa.
Omnissa – The Desktop and Application Service Solution
Omnissa Horizon 8 enables the creation and management of virtual desktops and applications, and it also incorporates security features like multi-factor authentication (MFA), support for smart cards, and secure tunneling through the Unified Access Gateway.
To reduce the time and complexity of desktop management and application updates, Omnissa provides streamlined deployment and automation through technologies such as Instant Clones, which enable rapid provisioning of desktops, and App Volumes, for on-demand delivery of applications.
Omnissa Workspace ONE is a support platform that integrates device management, application management, access control, and more into a unified solution. It includes Identity and Access Management to provide secure single sign-on (SSO) and multi-factor authentication (MFA), ensuring secure access to applications. Workspace ONE also incorporates robust security features such as conditional access policies, data loss prevention, and real-time security monitoring.
Finally, through the Workspace ONE Intelligent Hub running on an IGEL edge device, IT administrators can view and control devices in the Workspace ONE UEM Console and proactively monitor users’ workplace experience using DEX.
Putting Everything Together
With IGEL and Omnissa fully in place, a user’s initial deployment of a workstation and connection to his or her computing resources works as follows:
- Powers up the workstation device running IGEL OS.
- Configures the network connection, wired or wireless as required
- Authenticates against IGEL Onboarding Service using domain credentials
- IGEL Onboarding Services connects to Omnissa Identity Service
- Multi-factor Authentication is used when required
- The IGEL device is configured, updated, and the requisite applications (e.g. Omnissa Horizon Client, Omnissa Intelligent Hub, Zoom VDI Plugin, etc.) are automatically installed.
- User is prompted to register the IGEL device with Workspace ONE UEM.
- The IGEL device presents the user with Omnissa Access Login screen.
- User logs into Omnissa Access portal using MFA as required.
- User is automatically connected using SSO (access tokens) to Horizon Desktop using Horizon Blast protocol
- Desktop is automatically provisioned by Horizon management plane
- User applications are delivered on-demand using Horizon App Volumes
After initial deployment of the workstation, future connections to the Horizon desktop and application resources begin with the Omnissa Access Login screen (Step #6 above).
Conclusion
The combination of the IGEL Secure Endpoint OS, IGEL Cloud Services, and Omnissa Horizon backed by Workspace ONE represents a powerful, cost-effective, and secure solution for delivering virtual desktops and applications. IGEL transforms everyday hardware into secure and efficient endpoints, while Omnissa provides the robust Horizon platform for accessing corporate resources from anywhere, anytime. Together, they offer enterprises a secure, manageable, and scalable VDI environment that meets the demands of a modern workforce.
To learn more about IGEL and Omnissa, visit the IGEL Omnissa Partner web page or complete the online webform to test IGEL OS with Omnissa Horizon and Workspace ONE.
The post How IGEL and Omnissa Deliver Secure and Efficient User Desktop and Application Solutions appeared first on IGEL.
]]>The post IGEL and Workspace ONE Up the Ante When It Comes to Workspace and Endpoint Security appeared first on IGEL.
]]>IGEL Technology has been a bastion of secure endpoints for over two decades. In the Spring of 2023, the company introduced IGEL OS 12, it is the first modular endpoint operating system designed for accessing desktops and applications running in the cloud.
Every aspect of IGEL OS 12 was built and runs with security first. From the boot process to application authentication, the IGEL Preventative Security Model ensures that devices running IGEL OS 12 are secure and have not been compromised.
ensures that devices running IGEL OS 12 are secure and have not been compromised.
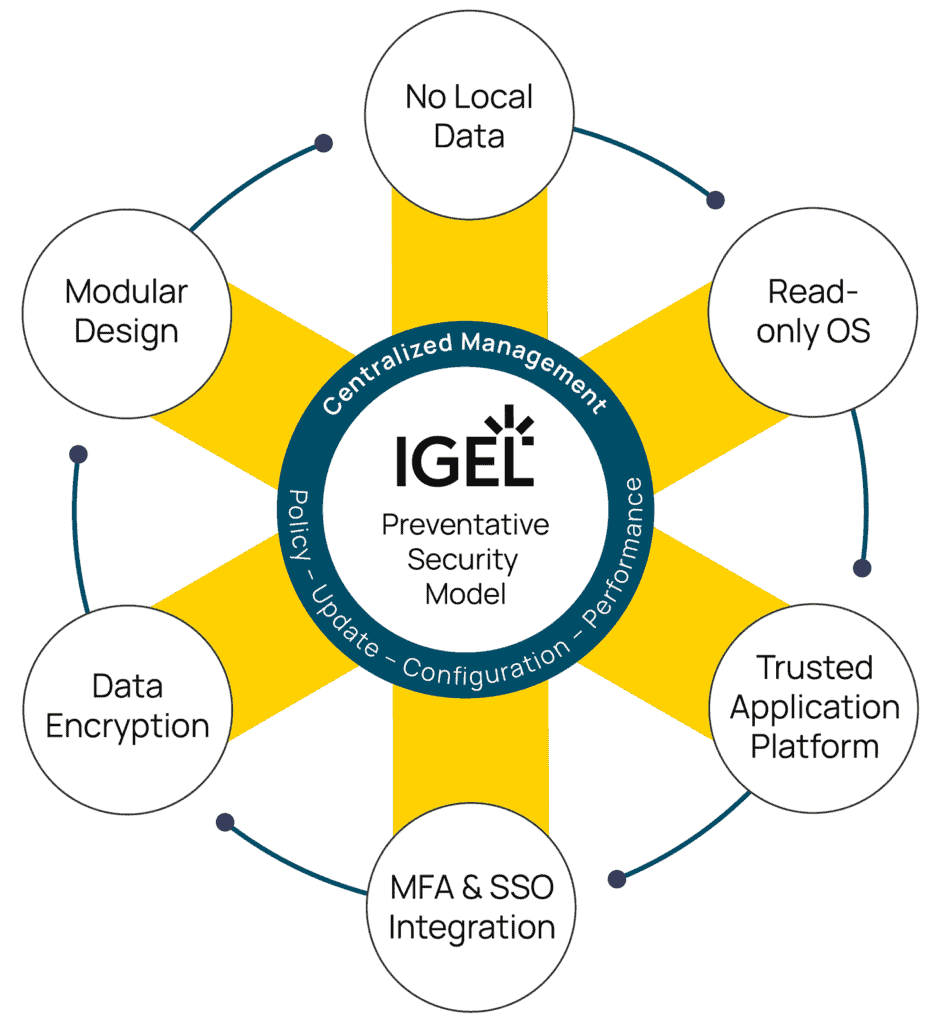
Years ago, IGEL recognized that the move to a cloud-first approach applications and workloads was accelerating. Desktops, applications, data, and identity would live in the cloud… or at the very least, be accessible through the cloud. Working securely in this new world would require an endpoint device designed to fit this purpose, and IGEL is delivering through its state-of-the-art OS that is filled with security features.
Integration with Workspace ONE Access
One of these features is IGEL Single Sign-On. Integration with Workspace ONE Access delivers a seamless user experience whereby a device running IGEL OS is configured to authenticate users directly against their organizations Workspace ONE Access identity provider. The IGEL OS device boots directly to the organization’s Workspace ONE Access login screen and is not usable for any purpose until a valid user is authenticated and authorized.

An IGEL OS 12 device configured to use Workspace ONE Access will be familiar to the user, displaying the Workspace ONE Access login screen. Once authentication is complete, the user enters the IGEL desktop, and an OAuth 2 access token is created for connecting the user to applications.
From the IGEL desktop, the user is authenticated by any application that supports OAuth 2 provided the application is a registered client in Workspace ONE Access. Most often, the IGEL application running locally is a browser that connects to the Workspace ONE Access Catalog. Any application launched from the Catalog will use the same OAuth 2 authorization code flow that was initiated when the user was first authenticated using IGEL Single Sign-On. Of course, when the user is done working and logs off the IGEL desktop, all OAuth 2 tokens are destroyed. It is a beautiful thing!
IGEL and Workspace ONE will be introducing more integrations throughout 2024 to further enhance secure access to applications and data, including working with Workspace ONE UEM to support conditional access, advanced application access through the Horizon Cloud Services next-gen platform, and support for industry-specific workflows like those in healthcare and financial services. So, keep an eye out for new feature announcements by IGEL and Workspace ONE.
Visit IGEL at HIMSS 24 in booth #4362 on March 11 – 15 in Orlando.
The post IGEL and Workspace ONE Up the Ante When It Comes to Workspace and Endpoint Security appeared first on IGEL.
]]>The post Getting even more out of Amazon WorkSpaces with IGEL and Tehama appeared first on IGEL.
]]>
In 2019, IGEL — a world leader in software-defined endpoint optimization and control for the secure enterprise — announced an alliance with Tehama to provide Amazon WorkSpaces via Teradici PCoIP® Software Client for Linux. IGEL Technology Evangelist Jeff Kalberg,recently sat down with Jaymes Davis, Tehama’s Head of Customer Success, to talk about the collaboration.
Jeff: Can you start by telling a little about Tehama and what you do?
Jaymes: Sure thing. We provide a Software as a Service (SaaS) solution that gives organizations controlled and monitored virtual workspaces for geographically dispersed teams that need secure access to corporate assets. Our platform has a pretty rich toolkit to support this secure access, including controls, policies, and secure vaults.
Jeff: What inspired Tehama to develop its solution?
Jaymes: The idea came out of our experience in IT contracting. You see a lot of outsourcing in IT — workers literally all over the world accessing corporate assets, often in not very secure ways. With workforce trends going even more in that direction, beyond IT, we realized this is something enterprises urgently need to access the right skills and talent without putting their corporate data and systems at risk.
Jeff: Do you have an Amazon WorkSpaces strategy as part of your approach?
Jaymes: We do. Amazon WorkSpaces provides a secure desktop but requires additional infrastructure management to enable end-to-end datacenter and cloud connectivity. We close the gap by providing the infrastructure that organizations require to provision their desktops. With Tehama, you can get customers connected in less than an hour, and you can implement multiple strategies for Amazon WorkSpaces with tools to improve productivity and collaboration. Thanks to our partnership with IGEL, we can give near-instant access to ‘ready-to-work’ Tehama Secure Rooms for simple, secure collaboration between remote employees while ensuring regulatory compliance.
Jeff: Let’s talk about that for a moment — why did you want to partner with IGEL?
Jaymes: Why wouldn’t we! Seriously, we’re thrilled to be teaming with IGEL, because the combination of our workspace delivery solutions with IGEL’s software-defined endpoints makes ready-to-work secure rooms possible. The IGEL UD Pocket is absolutely key: an end user can walk up to any 64-bit x86 device, plug the UD Pocket into an available USB port, boot from USB using Secure Boot, and get near-instant access to a Tehama Secure Room.
Jeff: How does the Room concept work?
Jaymes: Amazon WorkSpaces provides secure virtual desktops. Our additional AWS infrastructure services and endpoint software let you create a secure perimeter around those desktops. Rooms live insidethat secure perimeter. They encompass a set of cloud-based tools to help customers speed up and simplify the design, deployment and management of secure workspaces in any on-premises or cloud environment. Rooms leverage automation and deliver proactive cost control through on-demand scaling and support a whole range of functions including file encryption, forensic analysis, auditing and collaboration. Because Tehama is SOC 2 Type II certified, our Rooms ensure data is encrypted at rest and in transit. This kind of security would be really tough for organizations to build on their own because it requires multiple disciplines and both human and technology resources. Tehama provides a readymade solution.
Jeff: Do you use Amazon WorkSpaces for existing IT resources or BYOD?
Jaymes: The key thing always is that you want to make sure sensitive data can’t be left on an endpoint. That means anyendpoint: corporate or BYOD. So we cover both. Amazon WorkSpaces allows for additional services to track and enforce the auditing of endpoint devices to ensure only assigned vendors are using them. Again, IGEL is a crucial partner for creating a trusted endpoint on BYOD solutions with the IGEL UD Pocket.
Jeff: How do you handle scalability in Amazon WorkSpaces?
Jaymes: This is one of the ways we make life even easier for enterprises. With Amazon WorkSpaces, you have your virtual desktops, but provisioning is still manual. The desktops themselves must be either pre-allocated or else you pay up front to grow “on-demand”. Tehama allows for true on-demand configuration and automates the allocation of IT resources, so you’re growing or contracting dynamically in line with what the organization needs. This improves business scalability and eliminates wasteful spending.
Jeff: What about controlling Amazon WorkSpaces sprawl?
Jaymes: When properly aligned with business outcomes, virtual desktops on Amazon WorkSpaces can see huge adoption curves. You can get into situations where the cost of desktops starts to exceed budget because demand is so high. WorkSpaces sprawl occurs when you end up with on-demand infrastructure resources that have been left on when they are not being used. Unless you can identify these systems, a process that can take hours, you’re stuck with unexpected expenses. We’ve designed our solution to reduce or even eliminate these costs. By controlling sprawl, and the related costs, we help eliminate the delays associated with designing and preparing proofs of concept, staging, and upgrades. This “velocity improvement” lets the enterprise serve internal and external line-of-business customers more quickly.
Jeff: How do you facilitate compliance for Amazon WorkSpaces deployments?
Jaymes: Tehama facilitates compliance and data sovereignty by letting customers locate workspaces and sensitive data in the Room or Rooms of their choice while managing multiple locations through a single pane of glass. That helps minimize total cost while meeting local, distributed security and compliance needs. Organizations can deploy our Tehama Gateway in required areas and control the corresponding data, applications and desktop images according to local or regional regulations, compliance specifications and data sovereignty rules. Our Rooms reduce the amount of regionally located management infrastructure, duplicate labor and overall complexity. So you get global assurance with local specificity.
Jeff: What’s your process for working with customers?
Jaymes: We start by asking about their business requirements. Why do they want to move desktops to the cloud? Are they looking to retire their existing virtual desktop infrastructure, or are they expanding for a burst? It’s all about what the business needs. I find some customers “guesstimate” when determining user consolidation ratios on servers or compute resources for AWS. Partners like Liquidware have analytics tools to gain insights into end users and existing desktops, and using tools like these before determining the hardware profile of an in-house solution or compute resources for a cloud solution like Amazon WorkSpaces is imperative.
Jeff: How do you prepare users to access their Amazon WorkSpaces?
Jaymes: The great thing about Amazon WorkSpaces is it provides access to the desktop from many different devices, and the client is deployable to multiple platforms. Configuring and connecting are pretty simple, but when you have various desktops, different authentication methods, and planning requirements, confusion can arise. Vendor and remote worker onboarding can take longer, which increases your time to value. With IGEL including the new Teradici client in their flagship operating system, IGEL OS, you have a terrific alternative for connecting to Amazon WorkSpaces. When combined with Tehama, you get a closed end-to-end system that supports a strong security posture that protects against misconfiguration, tampering via key loggers, and browser infection. And because Tehama has seamlessly integrated its WebUI with the Amazon WorkSpaces implementations of SAML and SCIM from vendors like OKTA, Ping, and Azure AD, we deliver a user experience that ensures effortless access through a secure perimeter from any device using two-factor authentication and one-time passwords.
Jeff: You mentioned time to value. How do you accelerate that?
Jaymes:Tehama with Amazon WorkSpaces improves time to value by about 10 times via easy B2B connectivity tools that ensure fast onboarding of remote workers or new workers, partners, and vendors using our WebUI. And then, as I mentioned, we centralize and optimize workflows across the IT lifecycle to simplify desktop and application delivery to Amazon WorkSpaces.
Jeff: That’s a great overview.Thanks for sitting down with me and talking all this through. I can tell you, everyone at IGEL is looking forward to collaborating on more Amazon WorkSpaces projects.
Jaymes: Thanks to you! We’re very excited about what we can accomplish together.
To learn more, check out our IGEL Community webinaror visit www.igel.com.
To learn more about Tehama, download our white paper.
The post Getting even more out of Amazon WorkSpaces with IGEL and Tehama appeared first on IGEL.
]]>The post Simplifying Unified Communications with IGEL appeared first on IGEL.
]]>Evolving from a single primary communication tool, the telephone, UC now entails a cornucopia of tools that serve to improve productivity. However, this bounty of options, combined with the drive toward virtualization, has brought several challenges to IT. For example, integrating UC in an environment where every user has a PC workstation confined to a private network has been relatively easy when compared to delivering a quality UC experience to an enterprise moving its users to a cloud-based workspace model.
Migrating desktops and applications to the cloud demands that IT adopt UC solutions that will work in a virtual world in which a millennial, mobile-driven workforce expects every device they use will be capable of accessing their suite of applications and data. At the same time, this next generation user will expect an extraordinary UC experience.
There are many components that are critical to delivering a hi-fidelity UC experience in a virtual world, including cloud/server platform, network, and choice of remoting tools. Equally important is identifying a consistent and manageable edge device on which to build the end-user experience.
Next-Gen Edge OS
IGEL OS, the next-gen Edge OS for Cloud Workspaces, once again proves to be the endpoint solution for this constantly evolving world of how we communicate and work. As cloud migration continues, IGEL Technology provides all organizations a path to a consistent, secure virtual desktop environment, one which now includes Unified Communication tools that are easy to use at the endpoint.
Backed by a comprehensive device management system that allows for extreme control over desktop and mobile workstations, IGEL OS endpoint devices provide for:
- Consistent user experience as employees access the applications and UC tools they require to do their job, regardless of device or location.
- Easy, secure access to virtual desktops, applications, UC tools, and content across devices and networks.
- Simplifying IT operations with device-focused centralized management, remoted session layering, and hybrid and multi-cloud management.
Specifically, devices running IGEL OS today work with the following UC tools: Microsoft Skype for Business, Avaya Equinox, Zoom Conferencing, and Cisco Jabber (with Cisco VXME).
Citrix and IGEL: A UC Collaboration
The Citrix Call Center in Fort Lauderdale recently deployed IGEL OS powered endpoints to solve a number of issues related to performance and UC: Citrix needed an intelligent, up-to-date, supported operating system to support Citrix Workspace and integrate with UC tools. Additionally, Citrix wanted to deploy IGEL OS to existing endpoints to extend the life of existing assets while improving security and providing a reliable, always-on experience for its inside sales representatives (or ISRs).
IGEL OS, in conjunction with Citrix Workspace, was deployed to give its ISRs consistent access to all the applications they need, regardless of which physical workspace they’re using. As an added benefit, Citrix road warriors are using the IGEL UD Pocket, connected to laptops and home PCs, to securely boot and remote their workspace, further preventing the potential for system exploits.
The issue of aging hardware was solved by converting existing endpoints into IGEL OS workstations, thus unifying all endpoints under the IGEL OS umbrella. Standardizing on the common read-only operating system has improved security and reliability for all Citrites accessing their mission critical applications.
Read the complete case study here.
IGEL and Citrix Future of Work Tour Moves to EMEA
If you’d like to learn more about how IGEL and Citrix collaborate to power the future of work, our Citrix Future of Work Tour moves to EMEA after a successful North American run. Visit the IGEL Events webpage for a full list of upcoming dates.
Plus, don’t forget that each of these Citrix Future of Work Tour events is eligible for the “I Challenge Everything” Porsche Taycan Giveaway Sweepstakes. Stop by the event to be entered to win an all-electric Taycan or case equivalent of $85,000. Visit here for more information.
The post Simplifying Unified Communications with IGEL appeared first on IGEL.
]]>The post How to Configure Amazon AppStream 2.0 on Your IGEL-Powered Endpoint appeared first on IGEL.
]]>Built on AWS, AppStream 2.0 leverages data center and network architecture designed for the most security-sensitive organizations. Users benefit from a fluid and responsive experience with their applications, including those pesky 3D design and engineering that are GPU-intensive. Furthermore,applications run on a virtual machines optimized for specific workloads and streaming sessions automatically adjust to network conditions.
AppStream 2.0 and IGEL
Did you know that you can use your IGEL-powered endpoint as an AppStream 2.0 ready workstation? It is fast and easy to configure. If you are a subscriber to AppStream 2.0 services, you can take the following steps to configure your IGEL edge device to automatically launch your AppStream 2.0 applications on startup. As always, it is best to create your sessions using IGEL Universal Management Suite (“UMS”) Profiles to do the job.
Create an IGEL UMS Session Profile for Amazon AppStream 2.0:
1) From the IGEL Universal Management Suite (“UMS”) Console, create a new profile based on a current firmware version. Under Sessions, navigate to the Browser section and add a Browser Session. Configure the desired start methods for your session. Because we’re creating an AppStream workstation, I would recommend setting the session to Autostart:
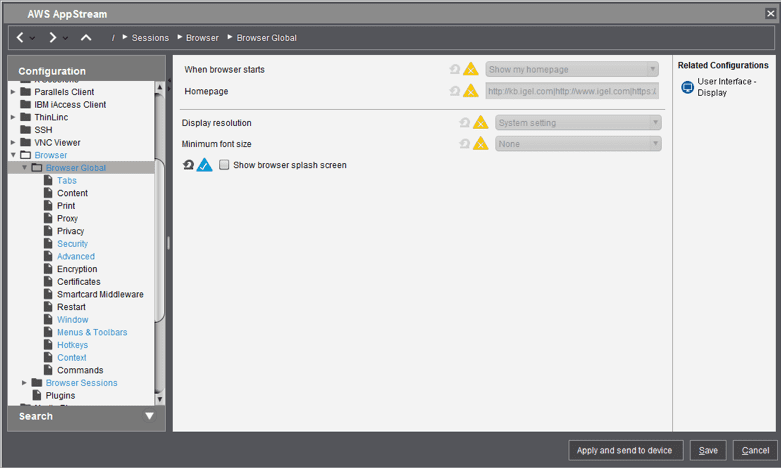
2) You want your session to land on your AppStream 2.0 logon page. So, under the “Settings” section of your session definition, you want to set the “When browser starts” option to “Show my homepage” and set the “Homepage” to the URL to point to your AppStream login page, which is usually your SSO portal. Set your “Start monitor” to whatever is appropriate for your use case, and check “Autostart” if the option is available for your firmware:
3) There are of global settings that you want to configure to “tighten up” the user experience. So, under Browser Global, you want to configure options in each of seven subsections: Tabs, Security, Advanced, Window, Menus & Toolbars, Hotkeys, and Context. You want to configure each of these subsections to match the screen shots below:
Browser Global
Explanation: We are disabling the intrusive Firefox splash screen because… it’s intrusive and we don’t care to see it.
Tabs
Explanation: We do not use tabs in our AppStream 2.0 workstation, so we are configuring the Firefox Browser to present everything in a single tab.
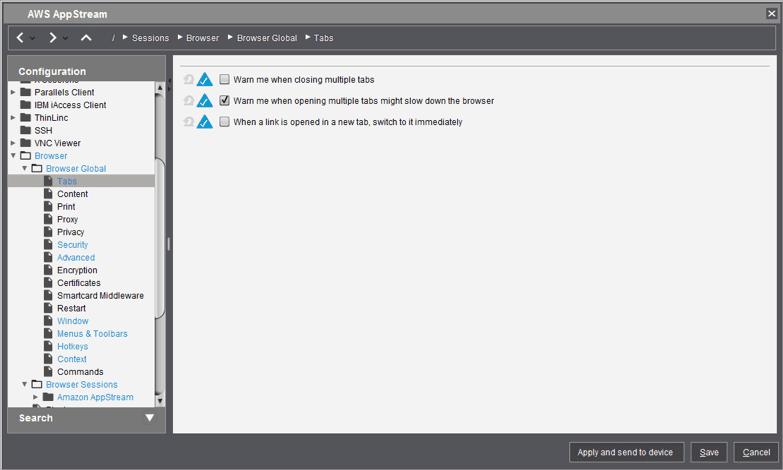
Security
Explanation: Since the Firefox Browser that is included with IGEL OS is being configured to connect only to your AppStream 2.0 portal, we are eliminating any chance to browse other websites, public or private. For the same reasons, we also can also turn off Firefox’s Safe Browsing and Malware Protection.
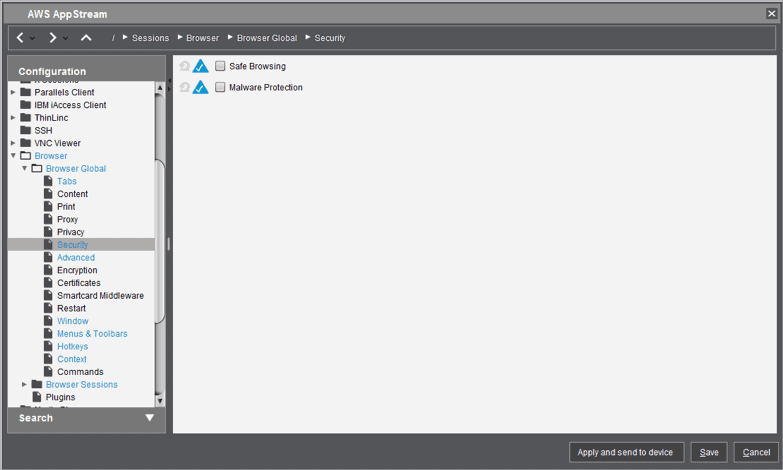
Window
Explanation: By starting the Firefox Browser in fullscreen, we are creating an application kiosk.
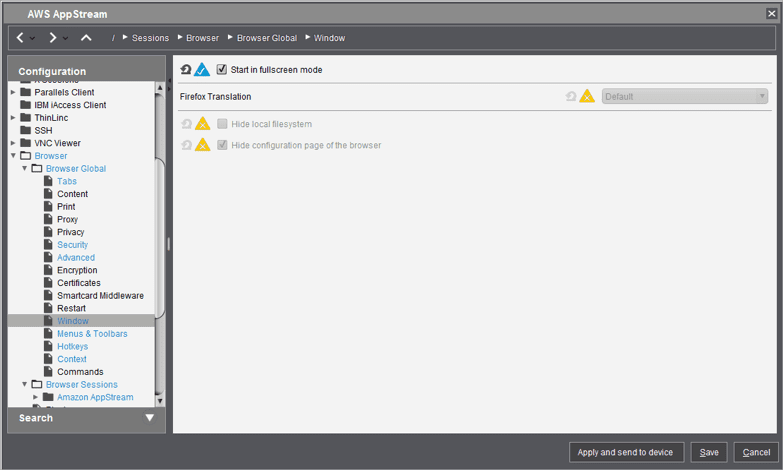
Menus & Toolbar
Explanation: By eliminating all menu bar, tabs, and navigations portion of Firefox, we are completing an application kiosk.
Hotkeys
Explanation: We do not want our users to be able to use Firefox hotkeys to perform various functions, so we are disabling all hotkeys.
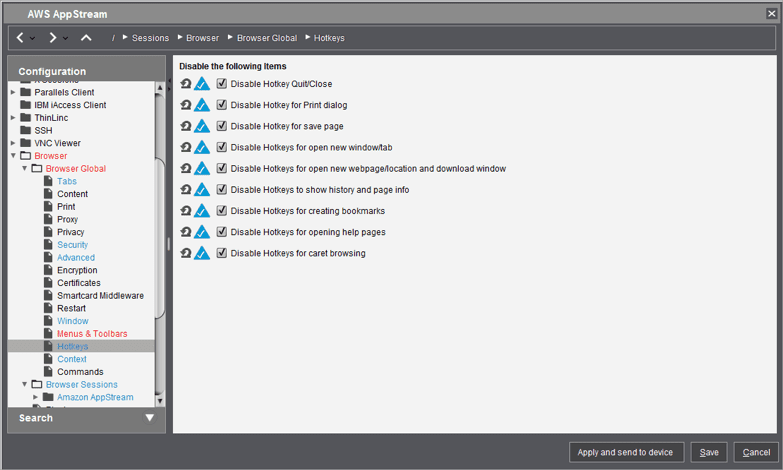
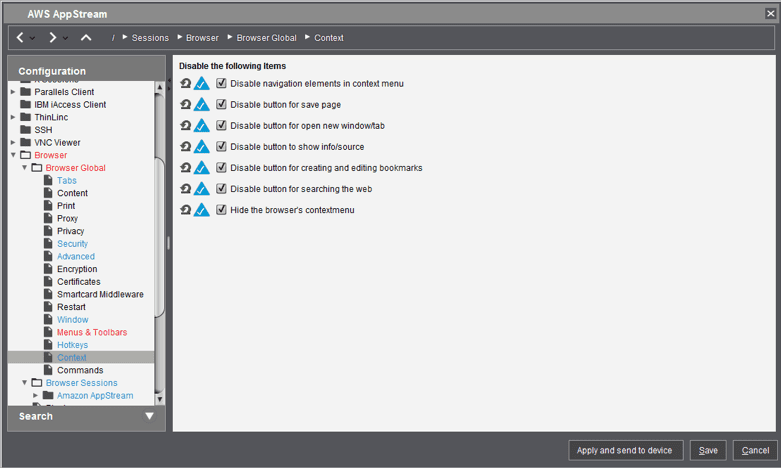
Context
Explanation: Since we don’t want users to access the context (or dropdown menu that appears when we Right-Click a webpage, we are disabling all context menu items and hiding the context menu completely.
Save your profile and apply it to your IGEL OS devices.
After your IGEL-powered endpoints have their IGEL AppStream Profile, the devices will automatically launch the Firefox Browser in a kiosk mode and connect to your SSO portal from which you can launch AppStream 2.0 streaming sessions. Here are some example of what you will see:
IGEL-powered endpoint booting up and browser launching as soon as the IGEL OS completes loading:

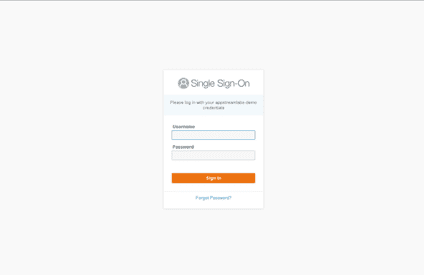
Login page to your intranet portal (AWS Single Sign-On shown):
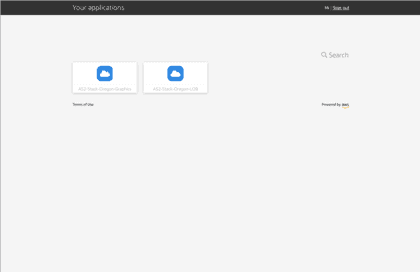
The AppStream 2.0 stacks the user is entitled to:
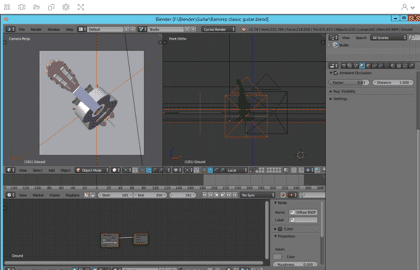
AppStream 2.0 streaming Blender, a free and open-source 3D graphics software used for creating animated films, visual effects, art, 3D printed models, interactive 3D applications, and video games, to the IGEL-powered endpoint:
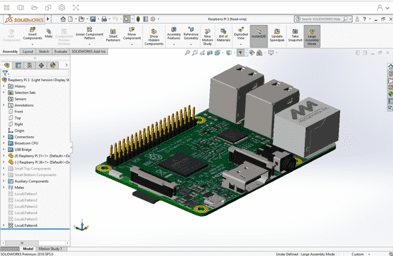
AppStream 2.0 streaming SOLIDWORKS, a computer-aided design and engineering computer program, to the IGEL-powered endpoint:
Use Cases
Use cases for AppStream 2.0 include enterprises, which can use it to simplify application delivery and complete their migration to the cloud; educational institutions which can provide every student access to the applications they need for class on any computer; and, and software vendors who can leverage AppStream 2.0 to deliver trials, demos, and training for their applications with no downloads or installations, or a full software-as-a-service (SaaS) solution without rewriting their application.
To Learn More
If you have AppStream 2.0 and are interested in learning more about how to configure the application streaming service on your IGEL-powered device, drop us a line at sales@igel.com.
The post How to Configure Amazon AppStream 2.0 on Your IGEL-Powered Endpoint appeared first on IGEL.
]]>The post Windows 10: The (Bad) Gift that Keeps on Giving appeared first on IGEL.
]]>It’s the latest in an approach that is the reverse of user-friendly. While 7GB may not have much impact on newer PCs that generally have a terabyte or more of storage, older PCs could feel the impact. More importantly, the average user no longer has free will! While the blog brings up the evergreen ‘optimization’ benefit, in reality, users are being told: you no longer have control over your own desktop/PC. Add to this the track record of Windows updates and it’s evident users are already suffering from update fatigue since some update rounds have had their share of glitches. Perhaps the most notable mishap was the October 2018 update that actually deleted user data; there were so many critical issues that Microsoft withdrew the update while they fixed the problems. The update was re-released in November, and today its adoption hovers only around the 20% adoption mark.
At IGEL we can’t resist gloating a little bit about this latest example of Windows 10’s update program and Microsoft’s dictatorial style in pushing out updates. We’ve been saying for some time that Windows 10 at the endpoint is getting more unmanageable and remains much more vulnerable to security threats. Our firm belief is that Windows belongs in the data center – not at the endpoint – where it can be better and more securely managed, with the proper hardware investment needed to perform well.
IGEL OS: The Answer at the Endpoint
Endpoints standardized on the Linux-based IGEL OS are the superior choice to serve users roaming on many devices at just as many locations for its manageability, stable operation, and ease of use. Putting Windows at the endpoint, in a VDI environment, is like towing a car to address a flat tire; a good spare is the better option. A well-designed, read-only Linux operating system is the spare tire, the safety net. IGEL OS is exceptionally light weight, seamlessly updated “over the air,” and has hardened security that is impermeable to cybersecurity threats.
Best of all, when we’re dealing with legacy investment, we can get off the Windows treadmill by using IGEL OS software to extend the life of our workstation assets and avoid without the high cost of a hardware refresh. We are then no longer tethered, at will, by Microsoft and its constant cycle of Windows updates and extended support programs.
As icing on the cake, IGEL OS is fully integrated into the IGEL Universal Management Suite (UMS) to give IT professionals a centralized device management system that is so efficient one person can manage tens of thousands of endpoints. Instead of having to find budget for the next hardware refresh, IT groups can provide users with the most customized, secure EUC experience available, via the Linux-based IGEL OS.
It’s time to get off the Windows treadmill. Learn more about the new IGEL Workspace Edition here.
The post Windows 10: The (Bad) Gift that Keeps on Giving appeared first on IGEL.
]]>The post Improving Endpoint Performance with Workspace Analytics appeared first on IGEL.
]]>Digital transformation continues its reign as the popular business topic of the day, competing with security for the amount of attention and anxious debate it provokes. A recent Gartner survey notes that 62% of respondents said they had a management initiative or transformation program in place to become a more digital business. A telling note is that 46% of those respondents said the objective of their digital initiative is optimization, which means a large number of all organizations are more focused on delivering a high-fidelity, end-user computing experience while minimizing costs, and on how they can monitor the metrics that impact the delivery of the end-user workspace experience.
Optimization means improving the performance of your human and technology resources while keeping a watchful eye. To accomplish this, we must have clear, crisp visibility into the metrics relevant to the delivery of workspace applications to your end users and to the devices – the endpoints – they use to be productive. This ability to monitor metrics has become even more important as enterprises evolve from traditional to virtualized desktop environments, and the quantity and variety of devices used by an organization’s employees continues to grow.
Workspace Analytics and Application Performance Management
To drive digital transformation – and optimization – one of the most important workspace analytics tools is application performance management which allows an organization to objectively monitor the user experience. By providing visibility into all of the components involved in remoting an application, these workspace analytics tools help organizations diagnose and proactively respond to user experience and performance issues before they become problems.
User experience metrics are a fundamental part of workspace analytics, but often the data collection process does not include the endpoint. Only when we link the client-side systems to the workspace analytics data collectors does an organization have a full understanding of application performance within virtualized environments. This richer detail gives IT the information it needs to improve endpoint performance and drive digital transformation.
Focus on Endpoint Performance
Optimization is a noble goal, one that nearly half of the Gartner respondents are treating as a priority. Understanding why the endpoint is such a focus promotes success in achieving optimization:
Many, many devices
End users are using as many as half a dozen devices in any one work week, running off a virtual environment, and often remotely. Workspace analytics can give visibility into all these moving parts, interrelating information to provide answers to problems in a timeframe and thoroughness that would be impossible without such a tool.
Hardware liberation
Moving the user application experience to a virtualized environment enables choice and the freedom to use different devices; however, with this choice comes an expectation that users will have the application performance necessary to do their job. End users like the option of varied devices if they work correctly and can deliver applications without headaches. When the virtual delivery fails, the reaction is to say “give me my PC. I have no time for devices that don’t perform!” Here workspace analytics is the preventive measure to head off user frustration.
Security and performance are one
With all this endpoint device flexibility comes the increased threats of rogue applications, users going off the corporate networks while processing sensitive data, or devices that are not equipped with adequate security controls. Workspace analytics can provide insight into what’s going on in the entire stack and can flag possible security issues. An exploit will impact performance; these tools are therefore valuable in risk containment.
Staff savings
Centralized endpoint security and optimization is critical to optimized performance when tens of thousands of endpoints may be in play. Also essential is managing IT staff time relating to endpoint troubleshooting issues. Analytics tools save IT time by providing detailed analysis of a single machine or user, and can help route trouble calls, including escalation where needed.
With Analytics comes Optimization
While improving their competitive edge is an often-talked about motivation for digital transformation, it’s encouraging to see businesses are realizing more often that a digital business must make optimization – performance – a priority as well. If “charity begins at home” then one can say optimization begins at each and every endpoint “home” where the end user’s productivity relies on IT’s clear understanding of how the endpoint is performing and the ability to remedy issues in a timely fashion.
The post Improving Endpoint Performance with Workspace Analytics appeared first on IGEL.
]]>The post Why End-User Computing Needs a Refresh appeared first on IGEL.
]]>
End-user computing (EUC) is experiencing a major shift in where people work, and the devices they use to do their job. A global survey just released shows that no less than 70% of respondents are working away from the office at least once a week, and 53% work remotely at least half time.
This shift from the traditional office and desktop work environment is disrupting not only how we think about our workday but what we expect from our organizations in terms of providing the device and application tools we need to fulfill our professional responsibilities.
Added to these stunning numbers of people working remotely are two other drivers changing how organizations deliver end-user computing. First is the proliferation of devices we use, and second is the user’s expectation that any device they use should deliver a consistent profile that is their own, fully populated with all the necessary applications.
Bringing EUC up to User Expectations
A widely reported statistic is that there will be over 50 billion connected devices by 2020. This anticipated proliferation of devices demands an innovative approach to managing, securing and delivering these endpoints and the applications that will run on them – to satisfy user expectations.
How can we make this happen? Here are some approaches that work:
- Embrace New Workspace Models. With literally billions of devices on their way, we need a new approach to managing endpoints. Adding teams of people to handle these large estates of endpoints is not economically viable for any organization. Consider a new model such as Desktop-as-a-Service (DaaS) to deliver the EUC experience via the cloud. A good DaaS example is Amazon WorkSpaces which enables organizations to provision virtual, cloud-based Microsoft Windows desktops for their users, giving them application access from any supported device. The pay-as-you go model lets organizations pay either monthly or hourly for the WorkSpaces they require.
Besides the user benefits and cost containment, a significant aspect is organizations are starting to realize they must have a highly flexible, nimble vision of delivering desktops to users now and in the future. Emerging models like DaaS present one attractive option for providing virtual desktops that are price-attractive and fulfill user demands.
The DaaS market is already seeing a number of players besides Amazon: VMware Horizon Air, Citrix XenDesktop, Cisco, and others. No doubt more players will enter as organizations see the service model as a compelling solution for delivering users what they need, regardless of device.
- Move from a Hardware to Software Mindset. Not only do your users expect all of the applications they need to be available on the device of their choosing, they expect any legacy hardware platform they may use to be equally proficient at running modern applications. But there is a major problem with the legacy hardware approach, and that is, it takes a boatload of money. The cost of a laptop or PC refresh can effectively be out of reach when a large estate of endpoints is in play.
An economically attractive and disruptive alternative to a hardware expenditure is the new wave of software-defined endpoint technology. Using a well-designed software approach enables any x86 device to be repurposed and transformed into a managed endpoint, and extends the useful life of existing assets. In a matter of minutes, organizations can convert any x86 device to a new OS, and fully replace aging and less secure operating systems with a hardened OS that connects the user to VDI solutions that can be more efficiently maintained.
- Improve Security on all Devices. We can all agree that giving employees the option to use a variety of devices helps productivity as we have enabled them to work any time and place. But this ability to choose devices, and ready access to an organization’s systems and data, poses a serious threat as ‘rogue’ endpoint devices outside of the confines of the secure corporate networks are a sterling invitation for cyber-attacks. Without management connectivity, these devices are without policy and controls. They are off the grid, so to speak, and are not accessible for patching and updating.
Verizon’s report on mobile security reveals organizations are aware of device threats but doing less than needed to improve security. Scarily, according to the survey, 32% admitted to sacrificing mobile security to improve business performance. At the same time, 93% of organizations agreed that mobile devices present a serious and growing threat, and 79% of the organizations fear that employee misuse, either accidentally or intentionally, is a significant concern.
The survey also indicates few organizations have implemented a strategy to mitigate device risk. Where do you start? A reliable and secure option is to move the employee’s workload to the data center using virtualization, and then remediate the employee devices’ operating system. By deploying a hardened Linux OS that is limited to remoting desktops and applications, you have implemented the best possible scenario for secure employee productivity. A properly designed device OS is resistant to viruses and malware, and is secured by an obfuscated read-only file system that employs methods like Secure Boot to insure the operating system is safe to load.
- Make Windows 10 more User Friendly. Windows for Desktops has become the operating system everyone loves to hate, and Windows 10, with its frequent and massively large updates, is no exception. In fact, Windows 10 seems to be defining a new level of frustration for IT organizations and their end users. Nevertheless, with a large number of user applications still relying on a desktop operating system, and with support for Windows 7 ending in a little over two years, deploying Windows 10 has become a necessary evil.
Fortunately, moving to Windows 10 does not have to be complicated and expensive. By virtualizing the Windows 10 desktop experience, we can make the migration as painless as possible. Plus, by adopting a virtualized desktop approach, we provide the average worker, who uses many devices, access in a way that does not sacrifice productivity, and helps to take some of the burden off IT.
Refreshing EUC: The Benefits are Limitless
With more than 50 billion connected devices heading our way against a backdrop of user devices and escalating security threats, it’s time to refresh our thinking about end-user computing. We need to embrace the new workspace delivery models that allow our valued associates to be more productive.
Over all of this, you need a unified management solution that can help streamline operations as the endpoint estate continues to grow. With robust unified management, tens of thousands of devices can be managed through a single console, extending the life of costly laptops and desktop systems, while ensuring consistent updates and a tight security posture.
A unified solution that is device and hardware agnostic, that can apply policy control and mitigate risk, will benefit all users and add business value. Refreshing your approach to end user computing will give your organization a stronger foundation from which to manage the next information technology challenge!
The post Why End-User Computing Needs a Refresh appeared first on IGEL.
]]>The post Raising Virtual Desktop Infrastructure (VDI) at the Endpoint | IGEL appeared first on IGEL.
]]>Delivering the best possible virtual desktop infrastructure (VDI) performance means taking a fresh look at what ‘desktop’ means today. The endpoint, or desktop, now can be a physical endpoint, a software-defined endpoint, a traditional laptop, a phone or tablet.
A recent story in APM Digest revealed the amount of operational waste enterprises are experiencing as IT devotes significantly more time to performance issues related to digital transformation initiatives. The research study detailed in the story finds that IT professionals are losing over 2 hours every business day, or 522 hours per year. Study respondents noted a more complex technology environment was a leading culprit in these performance issues.
Complex technology isn’t going away. In fact, more than likely, digital transformation will continue to add technical complexity. One area that enables enterprises to reduce complexity and streamline operations is their virtual desktop infrastructure. Virtualization is a linchpin of digital transformation and effectively optimizing an enterprise’s VDI is essential to moving forward with digital technologies.
To reduce operational waste and achieve better performance across the desktop environment, consider these five actions that can help IT deliver positive VDI performance for their users:
- Accommodating Self-Serve Access. Employees should be able to access certain applications without having to contact an IT help desk. Enabling ‘self-serve’ application access, as appropriate, allows employees to access their personal desktop workspaces, and needed applications, without using valuable IT time.However, there is a flip side to this: IT needs to control how far employees can take self-service. If employees are spending too much time onboarding more advanced applications, and less time being work-productive, then those applications may need to be controlled by IT and virtual desktop management.
- Paying Attention to the Edge. Using centralized management software, IT can control and manage edge devices’ use of applications residing in the data center. For example, software managing endpoints can retrieve a user profile and populate the endpoint with applications that a user needs to be productive. This centralized VDI approach can result in the economies of a single IT person managing as many as 30,000 endpoints – a great reduction in IT time and resources!
- Thinking Software, not Hardware. Enterprises are moving away from endpoint hardware investments to software that supports the pace of digital transformation. Improving endpoint performance means being able to quickly onboard new employees, deliver custom configurations to a remote workforce using a variety of devices, and to quickly populate new applications for ready use. Endpoint software such as endpoint firmware is a means of delivering profiles and applications via a single pane of glass, regardless of device.
- Understanding User Expectations. Your average worker today wants to use many devices, with the expectation the device will deliver what they need to do their job. The ‘desktop’ of today can range from software-driven endpoints to USB devices. Endpoint security and optimization must be able to manage all these devices, control application access and mitigate security risk. It is challenging since, for example, there are many versions of Android and iOS in use, with the threat that users are loading up applications that can pose risk to the network.USB devices pose one solution, freeing the user from physical boundaries, yet delivering the desired level of endpoint security. A new employee, for example, can plug the device into their personal laptop, and securely receive the configuration and applications they need, without IT ever having to touch the device.Enterprises are searching for these types of solutions that deliver an optimal user experience without adding to operational complexity.
- Looking at the Bigger Picture. Getting ahead of digital transformation technology needs, and advancements, is critical to winning the digital game. The alternative is never really catching up with technology and being overwhelmed by the complex IT environments that are becoming standard today.
In the study of operational waste, IT professionals said, if they could reclaim those two hours a day, they would spend more time researching and deploying new systems/technologies.Staying up to speed on virtualization technology is essential to digital transformation succeeding. Companies such as Citrix and VMware are innovating technology that plays right into the enablement of high VDI performance. Remote display technology that accommodates workers using graphics intensive applications is an example of delivering innovation that users expect. Freeing up IT time to continue to integrate these enhancements in the user experience has to be part of a thorough digital transformation.
Move Digital Transformation Forward with Optimized VDI
Enterprises are grappling with the challenges of digital transformation, from figuring out cloud deployment, data storage, and BYOD security threats to how to deliver an endpoint experience that optimizes performance.
These five actions will help IT deliver VDI performance that supports digital transformation initiatives. Improvements such as enabling workers to be more self-sufficient, and streamlining endpoint security and optimization will reduce operational waste, reduce both operational and capital expenditures, and maps to the market trend toward centralized endpoint security and optimization software that can accommodate a variety of devices.
Freeing up IT time will allow IT to better plan for more integration of digital technologies which in turn, increases the enterprise’s competitive strength. After all, this is the purpose of digital transformation!
Note: This article initially appeared in APM Digest on September 12, 2017.
The post Raising Virtual Desktop Infrastructure (VDI) at the Endpoint | IGEL appeared first on IGEL.
]]>The post Proper Endpoint Security Keeps Virtual Desktops Safe for Mobile Employees | IGEL appeared first on IGEL.
]]>Because governments perform tasks critical to the health, safety and well-being of its citizenry, public sector organizations have a particular sensitivity to threats like the WannaCry ransomware attacks. Adding to this threat is the fact that public agencies work in a distributed environment where employees access data from remote locations using a variety of devices, one where vast amounts of information are made available through the Internet. This complex puzzle of devices, locations, and layers of user access create an environment ripe for cyberattacks. One person curiously opening an email attachment or clicking on a web link can provide the runway necessary to bring down a system.
Information technology teams in the public sector face significant challenges supporting remote workers’ access to the applications and data required to be productive while, at the same time, maintaining security controls that protect against the constant barrage of exploits. These controls are taking on greater importance as ransomware attacks are multiplying, while workers and contractors are demanding expanded information access to do their jobs.
Advanced Endpoint security and optimization Must be Considered for Productivity and Security
Like every other user of technology, the government user lives on the edge. This is to say that the device they use to access information technology is on the edge of the network. For this reason, the endpoint, including all forms of endpoints and virtual desktops, has to be a focus when considering productivity and security. And because users are curious people, advanced endpoint security and optimization is essential to helping ensure secure access to these virtual applications and desktops. Advanced endpoint security and optimization provides the controls necessary to protect workers while giving them the freedom and tools to do their job well, while further lessening the risk that they will fall victim to the next exploit or ransomware attack.
A case in point is UNC Health Care, a not-for-profit, integrated health care system owned by the State of North Carolina and based in Chapel Hill. The system is comprised of UNC hospitals, its provider network, clinical programs at UNC School of Medicine, and nine affiliate hospitals and hospital systems. UNC Health Care was ready to go to the next stage of virtualization with a complete Citrix rollout. In so doing, UNC Health need to find a software-based endpoint solution that could leverage some of its existing assets, to control new investment costs. The answer was to employ endpoint software that reduced costs, increased security at the endpoint, and centralized IT management while supporting the various workflows used in healthcare. Furthermore, UNC Health was able to improve the end user experience by provide physicians and staff the flexibility to access medical records and other information while roaming between workstations.
Virtualization Technology Can Streamline Access and Protect Against Malware
Private sector health care organizations like UNC Health are constantly seeking ways to improve application and data access for its staff, and virtualization is proving to be the means to streamline access while protecting against exploits and malware. UNC Health Care illustrates a number of solution best practices that are applicable for a public sector agency wanting to secure its remote and/or roaming workforce:
- User Context. IT has to consider that staff and contractors will take their work home with them, on occasion, thus creating additional security risk. Agencies need to put in place access controls to limit what the user is allowed to do, based on their location.
- Device and Network Awareness. Endpoints can be profiled according to network, location or user. Using device management technology, it is possible to lock out devices similar to the way network access controls work. If a device is found to be operating outside of defined parameters, controls are in place to automatically cause these devices to cease to function.
- Roaming Mode. With staff moving constantly between locations and workstations locations, IT has to provide security controls that support this mobility and yet allow fast access to critical files and applications. IT can configure a roaming mode which allows staff, for example, to simply tap their badge to securely login to their desktop from any roaming endpoint. Additionally, IT could provide a kiosk mode which stays logged in, but runs programs under the user’s context. Users are required to type in their password only twice a day; the rest of the time they simply tap the employee badge on the card reader to login automatically.
- Certificate-Based Communication. Using software-driven endpoint technology, IT can deploy certificate-based communication between management servers and virtual endpoints. This protects against DoS and man-in-the-middle attacks.
- USB Control Devices. Where appropriate, another method of giving users the productivity tools they need, and further mitigating risk, is providing staff with a USB-bootable managed micro endpoint. The user simply boots to the USB device to run their PC as a virtual endpoint, accessing only the desktop applications for which they have authorization.
Manage Security at Your Network’s Endpoints For Best Control
Managing security at the endpoint, and controlling application and file access in the appropriate user context, is of paramount concern in the cyberattack era. Advanced endpoint security and optimization that controls limited function devices operating as endpoints are a compelling option for public sector organizations that must balance the desire to provide a flexible, productive user experience with the need to have effective, efficient control over the security of the organization and its data.
Note: This article first appeared in the Industry Insight section of Government Computer News on July 5, 2017.
The post Proper Endpoint Security Keeps Virtual Desktops Safe for Mobile Employees | IGEL appeared first on IGEL.
]]>